Just before the year comes to a close, we are excited to announce the release of Tufin Orchestration Suite R21-3. Key release highlights include integration with Zscaler Cloud Firewall, a new Security Policy dashboard, enhanced access change automation workflows, and NGFW support, to help our customers centralize and streamline segmentation policy management across the hybrid cloud, in addition to simplified and automated migration and compliance.
Here’s a brief summary of what’s inside the Tufin 21-3 release:
Tufin and Zscaler Cloud Firewall integration provides centralized visibility and simplified policy management
Tufin continuously integrates with leading solutions to enable organizations to centrally manage and apply consistent and effective segmentation policies across their multi-vendor, hybrid cloud environment. In R21-3, Tufin extends its visibility and policy management to support Zscaler Cloud Firewall, part of the Zscaler Zero Trust Exchange. The joint solution enables organizations to easily achieve a unified view, and standardize security policy management of Zscaler Secure Access Service Edge (SASE) policy rules, directly from the Tufin console.
Key features include:
- Rule Viewer. Tufin’s Rule Viewer enables network administrators to gain an instant view of Zscaler Cloud Firewall rules directly from the Tufin dashboard, for fast analysis and violation detection. Users can view rule attributes — sources, destinations, users, applications. The Rule Viewer also provides rule metadata, such as when the rule was last modified, the certification status if rule certification is being enforced via Tufin, and if the rule is overly permissive and should therefore be modified or removed.
- Rule Change Tracker. To ensure continuous compliance and enable faster troubleshooting, Tufin monitors and highlights Zscaler Cloud Firewall rule changes– what was changed, when, by whom, and whether there’s a comment or a reference associated with it. Tufin records every policy revision, maintaining a complete policy history as it evolves over time. Administrators can quickly retrieve and view the Zscaler policy as it existed at a previous point in time. A side-by-side comparison helps admins review changes to identify and fix misconfigurations. This can be invaluable when a change unexpectedly blocks access to a critical asset, enabling auditors to immediately view what has changed since the last audit.
- Rule filter. Admins can filter rules by locations, apps, URL category, and users, for faster resolution of security and connectivity issues.
Tufin and Zscaler integration in action
We see a growing adoption of SASE solutions in the market, and will continue to invest in supporting additional features to help our customers integrate SASE solutions into their network security fabric.
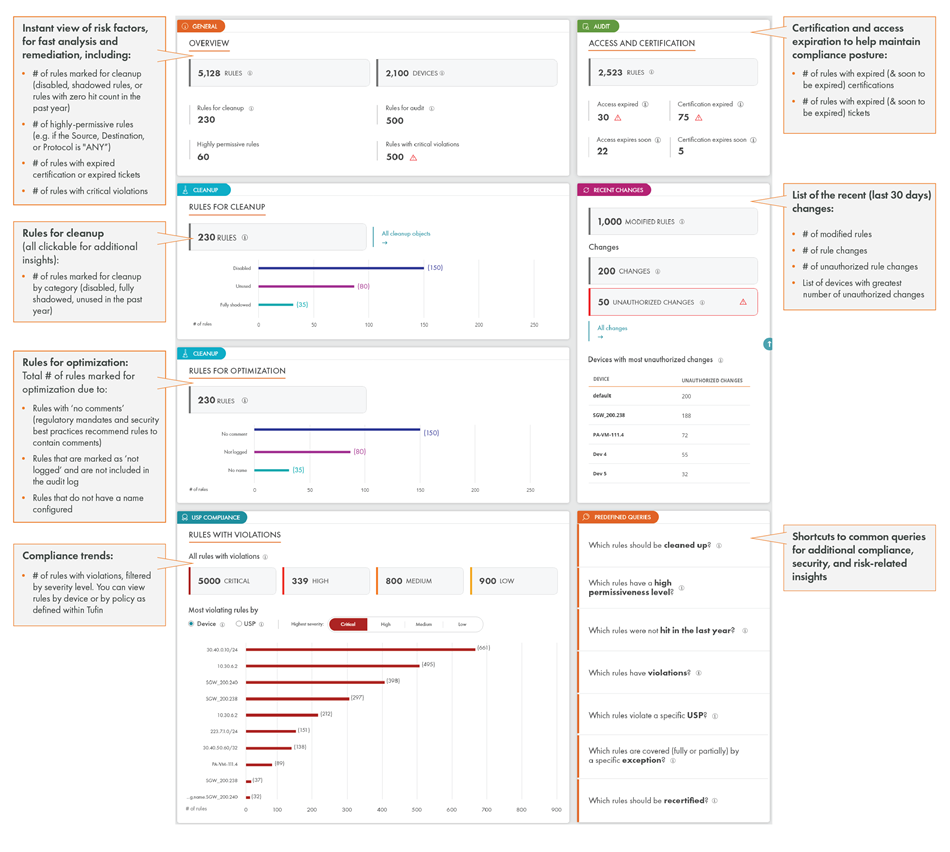
A new security policy dashboard: Critical insights for proactive remediation
To help you effectively manage and control your most critical policy-related activities and focus on what matters most, Tufin has created a new and intuitive security policy dashboard. The new dashboard was designed in close collaboration with Tufin users, to provide real-time, consolidated insights into the most critical operational, security, and compliance metrics across your hybrid environment. This includes security policy violations, expired and uncertified access rules, policy optimization recommendations, and more. Some of the metrics, filtered by criticality, indicate current status, as well as those soon approaching issues (e.g. certifications/access nearing expiration), to facilitate a proactive and timely response.
In addition, the dashboard provides you with a set of smart widgets that you can click to gain additional compliance, security, and risk-related insights. You can also run your own queries or use the predefined queries, for a fast search.
One of the great benefits of this dashboard is that it presents all the network security access data from the different vendors’ solutions, in a single location. Tufin automatically retrieves this data, constantly monitors, and alerts on current and upcoming issues, making it easier to analyze, prioritize, and remediate effectively.
Accelerate data center migration via automated workflows
A typical migration process involves cloning existing network policies, so that the newly migrated networks will maintain the same level of security, as well as the removal of obsolete subnets/Network IP Address ranges from existing policies and rule bases. Doing these changes manually across a mix of tools can be an arduous, time-consuming, and error-prone process.
What’s more, security administrators often avoid removing migrated networks from policies for fear of causing an outage and disrupting business continuity. Leaving these subnets/ranges in policies, can result in increased attack surface. With R21-3, users can leverage Tufin SecureChange workflows to automatically clone security policies of subnets/ranges and remove obsolete subnets/ranges from policies across a multi-vendor, hybrid environment.
Using automation to power both tasks is the most effective way to avoid misconfigurations and helps admins accelerate data center migration projects while maintaining a strong security posture.
Clone security policies for subnets and ranges
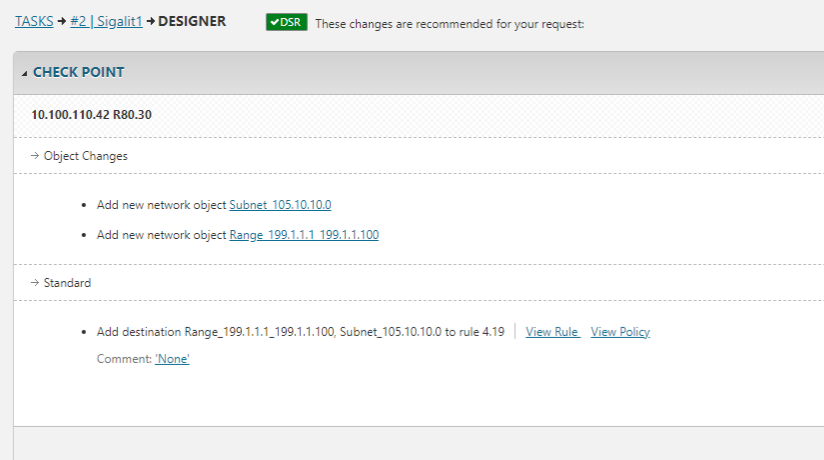
With 21-3, you can use the Tufin SecureChange Clone Server Policy workflow to duplicate access permissions of an existing subnet/range, for a new subnet/range. This workflow includes multiple steps, whereby the Tufin Designer provides recommendations for policy changes. Once approved, changes are provisioned to the relevant devices. After cloning a policy of a subnet/range, all rules which include the existing subnet/range, will also include the new subnet/range.
Decommission obsolete subnets or network ranges
Here, we added the option of removing subnets and ranges that are no longer needed from relevant security policies using the Tufin SecureChange server decommission workflow.
This is also a multi-step automated/semi-automated process that includes impact analysis to identify the affected network devices and policies. For each device, you can view the impacted rules. The Tufin Designer then makes recommendations for the rule changes that need to be implemented. Changes are then provisioned automatically across all relevant vendors’ devices and environments.
Maintain accurate security policies while simplifying daily operation
Use free text to search throughout complex, multi-vendor security policies
Segmentation/micro-segmentation policies are difficult to understand and manage, as they often include hundreds, if not thousands of rules. Searching throughout numerous policies can be a very lengthy process. To simplify your daily operations, with R21-3, you can now use free text in the ‘Rule Viewer’ to search for any policy elements across all rules’ fields. You can type any keywords; for example, a rule business owner, object name, tag, etc., and it will return everything that matches the search. This helps provide quick and easy retrieval of undefined data elements across all policies.
Exempt specific security policy rule/s
One of the challenges security admins face once they’ve created a segmentation policy is having to cope with multiple violation alerts. Some violations are triggered by common scenarios, such as onboarding/offboarding device projects or urgent business requirements, and some can be a result of stale and overly-permissive rules that undergo optimization. No matter the reason, you can now decide if to exempt specific rule/s (either for a limited time or indefinitely) from triggering security policy violations.
You can also choose the scope of the exemption – whether to apply an exception to a specific segmentation policy, all policies, or even a specific zone-to-zone relationship. Any activity matching these exceptions, will not trigger a violation alert. Finally, every exception will include an owner, time stamp, exception justification, and more.
Remove unused access to maintain up-to-date, compliant policies
In large scale environments, manually removing access from policies could be arduous. If left undone, however, it can offer avenues of attack to adversaries. To help you keep your rule base clean, in Tufin’s previous release, R21-2, we provided an enhanced automated process to decommission network access in Cisco ASA, FortiManager, VMWare NSX-v and NSX-T, Amazon AWS and Forcepoint Stonesoft, once it’s no longer deemed appropriate or necessary. All changes can be part of the same ticket. There’s no need to open multiple tickets in order to implement these changes, and the same ticket can include the added and removed access requests.
In this release, R21-3, we’ve added support for access decommissioning in Check Point (R80) and Palo Alto Panorama. This is an automated/semi-automated process that can save you valuable time and resources, and minimize potential security risks caused by misconfigurations and manual processes.
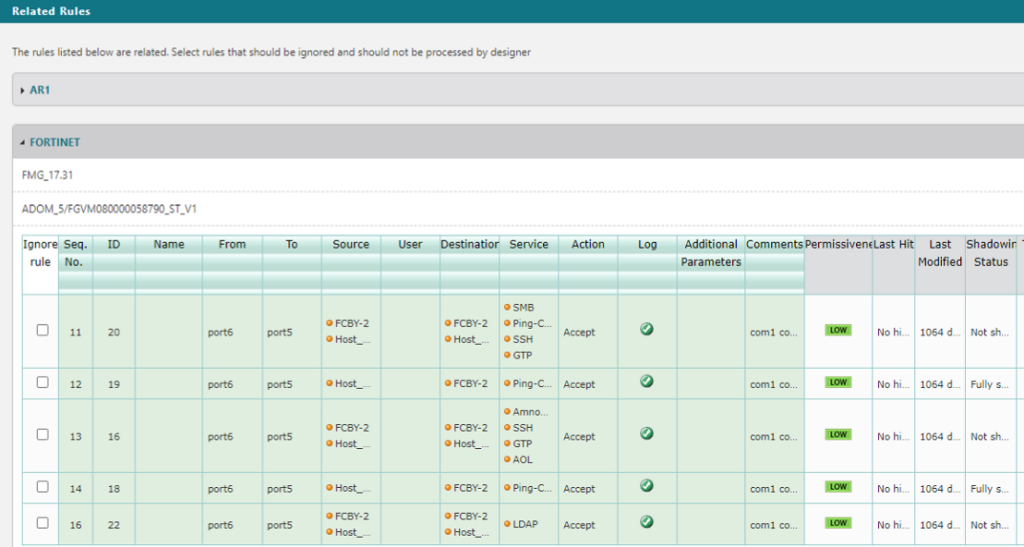
In addition, to support users through the complex and sensitive task of removing network access, we now provide visibility into the specific network objects within relevant rules that implement the network access and should be removed. Tufin highlights the various objects within soon-to-be-changed rules, in the dedicated “Manage Related Rules” screen. This provides users with insight into how network traffic is implemented, and helps them choose which rules should be impacted by the access removal process.
Further, we also added flexibility into rule removal, to support a larger variety of common practices, so users can now choose to disable rules rather than remove them, via workflow configuration.
Simplify and automate Palo Alto Panorama Dynamic Address Groups (DAGs) policy changes
Tracking and controlling changes to policies with Palo Alto Networks Panorama Dynamic Address Groups (DAGs), can be challenging. DAGs are used in policy rules’ source and/or destination, instead of specific IP addresses/static groups. As admins, we need to track which objects are tagged and added to each DAG, and if there were any changes to the DAG. If we don’t have visibility and control of these changes, it’s easy to end up with misconfigurations that can lead to overly-permissive, shadowed rules or other violations.
In 21-3, we further enhanced Tufin support for Panorama Dynamic Address Groups (DAGs), to provide, in addition to visibility into DAGs content and changes (R20-1), the ability to automate policy changes with DAGs, so that any change to the DAG is controlled, and does not violate your security policy.
Admins can use Tufin SecureChange workflows to automate the design and implementation of new access changes and rule modification, as well as multiple firewall (group) modification, with static or dynamic address groups in the source and destination. These changes are then implemented to all relevant network enforcement points, anywhere, across your hybrid cloud environment, reducing time and operation complexity of maintaining Panorama policies
Ready to Learn More
Get a Demo





