Tufin Enables Energy and Utilities Organizations to Navigate Complex Security Challenges
Energy and Utilities organizations face significant cybersecurity challenges, including protecting critical infrastructure, defending against ransomware attacks, ensuring supply chain security, upgrading legacy systems, and maintaining regulatory compliance.
In addition to these, network and cloud security policy management hurdles such as advanced persistent threats (APTs), securing operational technology (OT) networks, mitigating insider threats, managing patching and vulnerabilities, and ensuring effective network visibility and control.
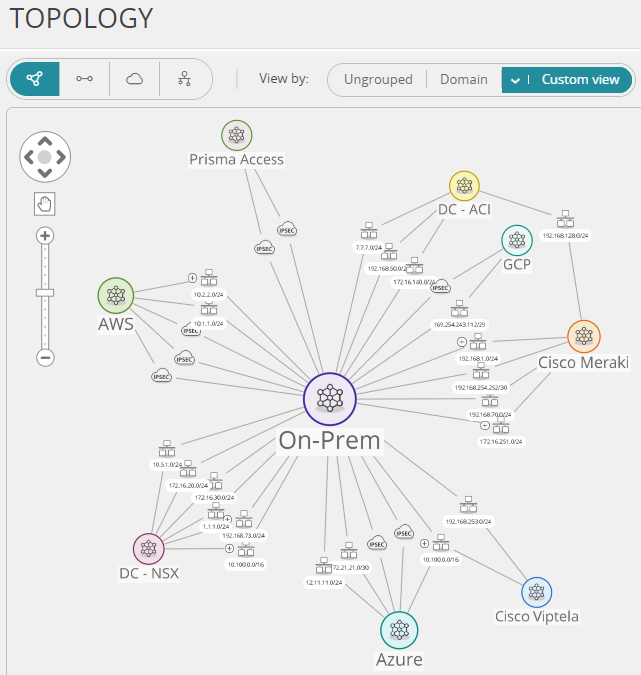
Unmatched Scalability
Whether you need to add another cloud network vendor or have 10,000+ devices and 200M+ routes to manage, our ability to ease your network security policy management challenges does not degrade. In the energy sector, our solutions enhance detection and response capabilities, reduce the attack surface, and leverage automation to streamline security operations.
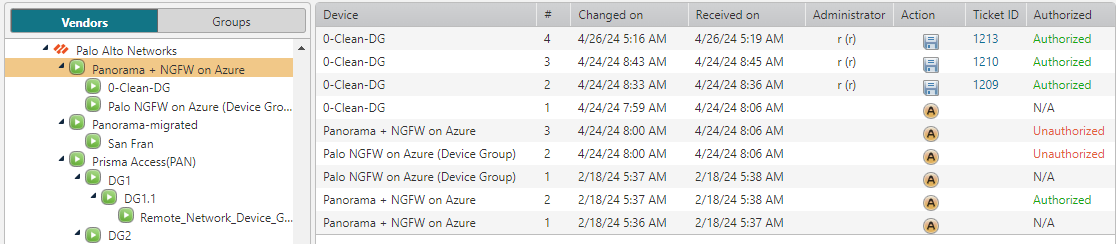
Protect Critical Infrastructure and Data
Tufin ensures that your Energy and Utilities organization can safeguard your critical infrastructure and sensitive data against cyber threats. Our solutions offer unparalleled visibility and control over your network security policies, protecting essential services from disruptions, and being accessed by malicious insiders or threat actors.
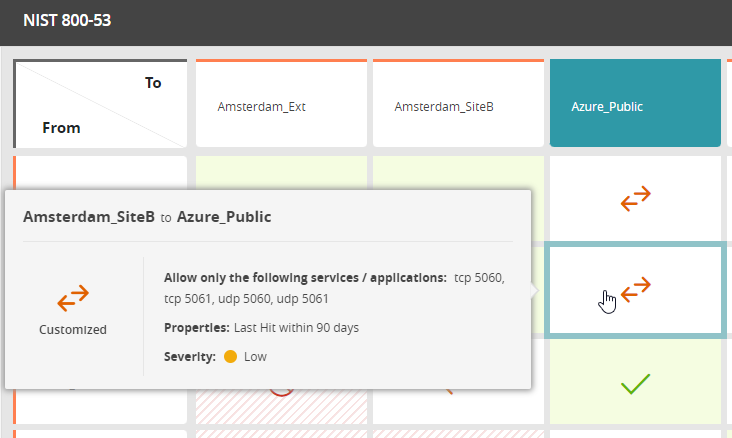
Automated Policy Management & Network Security
By enhancing threat detection and providing comprehensive cybersecurity services, Tufin helps protect your energy infrastructure. Our solutions leverage segmentation and threat intelligence to bolster cyber resilience, ensuring that your operations remain secure and efficient.

Compliance and Regulatory Adherence
Tufin’s security solutions help you ensure compliance with frameworks such as NERC CIP, GDPR, and other regional regulations.
With real-time alerting and quick identification of critical security policy violations that impact your compliance status, Tufin provides constant audit readiness.
By addressing the evolving threat landscape, our solutions enhance authentication measures, protect against hackers and phishing attacks, and mitigate the risk of outages. Effective risk management ensures your energy infrastructure remains secure and compliant.
Tufin Customers’ Networks are Supported by the Industry’s Broadest Technology Partnerships
Tufin has pre-built integrations with all major network and cloud security vendors. This allows our customers in the utilities sector, including those focusing on renewable energy, to manage, monitor, and modify all their network security policies from one unified location.
By enabling comprehensive risk assessments and endpoint protection, Tufin enhances your overall cybersecurity posture and facilitates effective mitigation of potential threats.
Ready to see a live demo or get a free trial?
All it takes is your business email address, your first name, and your last name.
