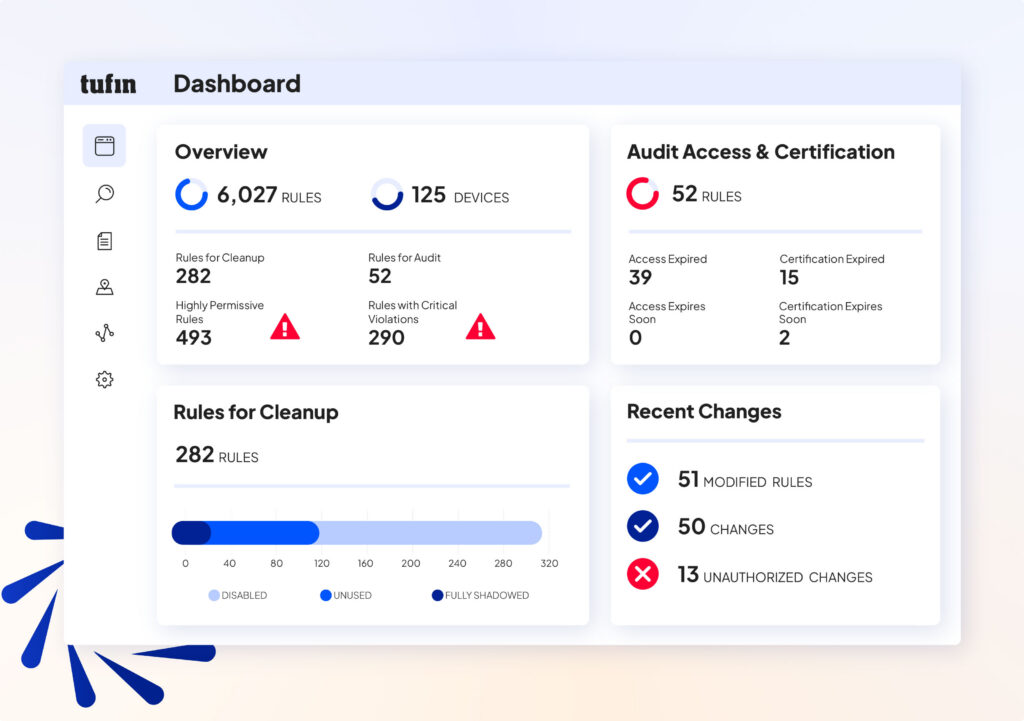
Accelerate Your Zero Trust Initiatives Today
Zero Trust is no longer optional; it’s a strategic imperative for securing modern hybrid environments. But fragmented tools and fast-changing environments make it difficult to enforce consistent policies, reduce exposure, and maintain compliance.
Tufin delivers a unified control plane for centralized visibility, automated policy orchestration, and continuous compliance across on-premises, cloud, and hybrid environments.
Why Tufin for Zero Trust
With Tufin, organizations can reduce lateral movement, eliminate security blind spots, and keep their Zero Trust architecture continuously aligned with regulatory frameworks.
Centralized Visibility
Eliminate blind spots and gaps across firewalls, cloud platforms, and hybrid networks.
Risk-Based Enforcement
Focus Zero Trust controls where exposures are the highest and exploitable.
Automated Policy Orchestration
Streamline access changes and enforcement with automated compliance.
Continuous Compliance
Validate Zero Trust security alignment with NIST, PCI DSS, DORA, and more.
Zero Trust Use Cases
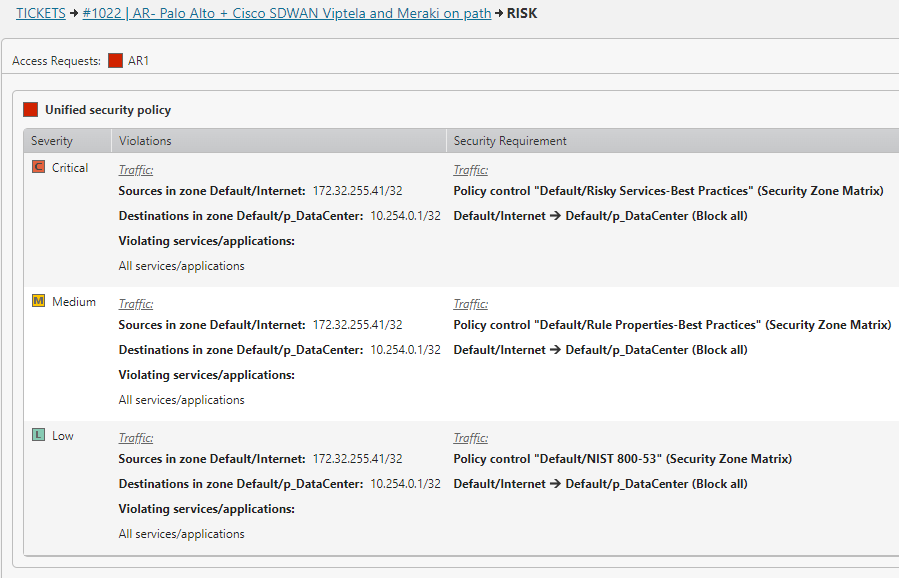
Optimize Zero Trust Policy Enforcement
Automate and validate policy enforcement to reduce errors and accelerate Zero Trust initiatives.
- Ensure consistent application and updates across hybrid networks.
- Reduce human error with automated workflows.
- Maintain accurate, real-time policies that align to posture and compliance requirements.
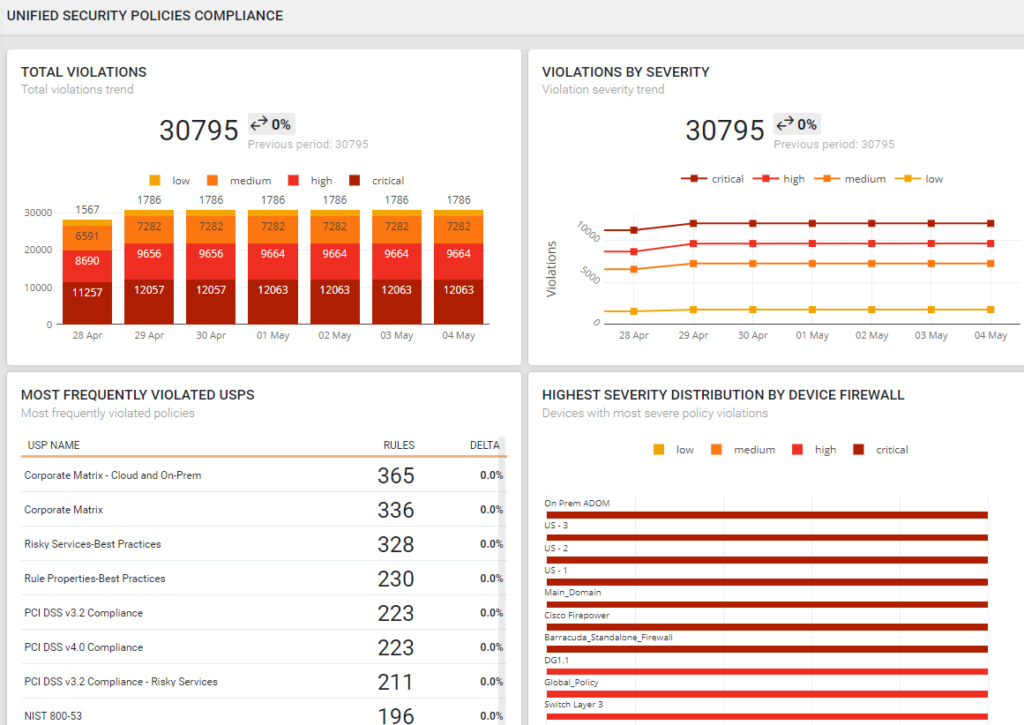
Achieve Continuous Compliance
Zero Trust requires ongoing validation. Tufin continuously maps policies to frameworks and generates audit-ready reports to simplify compliance.
- Automate compliance checks across workflows and devices.
- Detect and remediate violations in real time.
- Streamline audit preparation with centralized reporting.
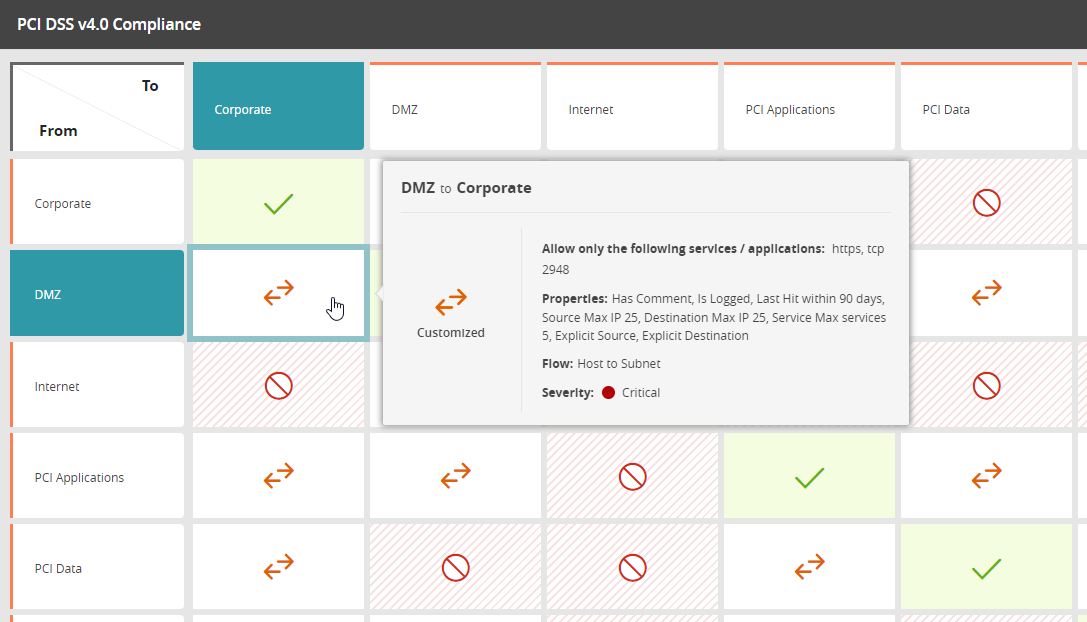
Enable Cloud-First Zero Trust
Tufin extends Zero Trust across multi-cloud environments with centralized visibility and control.
- Monitor and enforce Zero Trust policies in AWS, Azure, and GCP.
- Apply consistent controls across on-premises and cloud platforms.
- Validate who and what can communicate — and block what shouldn’t.
How Tufin Delivers Zero Trust
The Tufin Platform is a comprehensive, AI-driven unified control plane for network security policy management. The platform is comprised of:
SecureTrack+
See every risk before it becomes a problem — with unified visibility, accurate topology mapping, and continuous risk assessment across firewalls, cloud, SASE, and microsegmentation. Automate policy optimization to reduce exposure and ensure continuous compliance.
SecureChange+
Turn slow, error-prone changes into secure, automated workflows. Accelerate delivery and cut SLA times by up to 90% with automated design, rule lifecycle management, and hybrid connectivity troubleshooting that eliminates delays and misconfigurations.
Enterprise
Scale security without slowing innovation. Automate access provisioning, accelerate application connectivity, and ensure uptime with built-in high availability and global scalability for the largest, most complex networks.
Zero Trust with Tufin
With Tufin, Zero Trust becomes more than a strategy — it becomes an operational reality. Organizations gain fewer breaches, reduced risk, faster remediation, and stronger compliance, all managed through a single control plane.
FAQs
Zero Trust Network Access is a Zero Trust security model designed to replace the broad access of traditional VPNs. ZTNA enforces Zero Trust principles by authenticating user identity and device health, applying least-privilege access, and providing secure, segmented connections to specific apps or workloads. This Zero Trust approach minimizes the attack surface, prevents unauthorized access, and supports modern use cases such as remote work and multi-cloud deployments.
Tufin complements ZTNA by aligning firewall and network security policies with Zero Trust solutions, ensuring access controls are enforced consistently across hybrid infrastructures.
Zero Trust Network Access (ZTNA) provides secure access to applications and workloads without exposing the broader organization’s network. Instead of relying on a VPN and a trusted network perimeter, ZTNA enforces never trust, always verify principles. Access is granted only after validating user identity, device health, and context such as location or role. ZTNA then creates a secure, segmented connection directly to the application, reducing the attack surface and preventing unauthorized access.
Tufin integrates ZTNA concepts with network segmentation and firewall automation, ensuring access aligns with centralized security policies and workflows across hybrid and cloud environments.
- Least privilege: Grant only the permissions needed for a specific task or user access scenario
- Continuous monitoring: Track network traffic, endpoints, and user identity in real time
- Microsegmentation: Break down the network into smaller zones to stop lateral movement
- Strong authentication: Require MFA, validation of devices, and strict access controls
- Automation and workflows: Enforce security policies, detect cyber threats, and remediate vulnerabilities without delay
- Threat intelligence: Use context from APIs and tools to block cyberattacks before they impact sensitive data
Tufin provides the policy foundation for Zero Trust architecture by automating firewall and network security controls, helping organizations apply Zero Trust principles consistently across on-premises, multi-cloud, and SaaS environments.
- Assess security posture: Map your organization’s network, workloads, and cloud environments to identify vulnerabilities and gaps.
- Define access policies: Base them on least privilege, user identity, and access management best practices.
- Strengthen authentication: Require multi-factor authentication and validate every access request.
- Implement network segmentation: Use microsegmentation and firewall rules to restrict lateral movement.
- Automate enforcement: Deploy tools that enforce security policies, optimize workflows, and provide real-time threat intelligence.
- Continuously monitor: Track network traffic, detect phishing or cyber threats, and adapt security measures over time.
Tufin supports Zero Trust strategies by providing centralized visibility and automation for firewall and access control policies, reducing complexity while improving cybersecurity posture.
Zero Trust is critical because traditional security models that rely on a strong network perimeter are ineffective in today’s multi-cloud and remote access world. Cyber threats such as phishing, malware, and data breaches exploit vulnerabilities in endpoints, workloads, and APis. A zero trust strategy applies never trust, always verify principles, reducing attack surface and enforcing strict access controls.
Tufin enables organizations to operationalize zero trust by automating security measures, aligning firewall and access policies, and giving security teams centralized control to protect sensitive data and prevent cyberattacks.
- User identity and access management: Strict access controls, MFA, and validation for every access request
- Device and endpoint security: Ensure endpoints meet defined security posture requirements before granting access
- Network segmentation: Apply microsegmentation and firewall rules to contain lateral movement
- Data protection: Safeguard sensitive data in cloud environments, saas, and on-premises systems with strong security measures
- Continuous monitoring and automation: Use threat intelligence, real-time detection, and automated workflows to remediate vulnerabilities and stop cyber threats
Tufin strengthens all five pillars by automating and centralizing network security and access policies, enabling organizations to enforce Zero Trust principles consistently across hybrid and multi-cloud infrastructures.
Traditional security models assumed that anything inside the private network was trusted, relying on VPNs, firewalls, and the network perimeter for protection. Once inside, users often had broad permissions, making lateral movement easy for attackers.
Zero trust security is based on never trust, always verify. Every access request is validated in real time using user identity, least privilege, and multi-factor authentication. Continuous monitoring, network segmentation, and strong security controls ensure attackers cannot easily move through the organization’s network.
Tufin helps organizations adopt this Zero Trust approach by automating the enforcement of granular security policies across multi-cloud, on-premises, and SaaS environments.
A Zero Trust policy could require that every access request to an application or workload is validated in real-time based on user identity, device health, and least-privilege access rules.
For example, a remote employee connecting to a cloud-based SaaS tool must use multi-factor authentication and meet defined security posture requirements before access is granted. Policies can also enforce microsegmentation, limiting lateral movement between apps, IoT devices, or data center resources.
Tufin enables security teams to translate Zero Trust principles into enforceable firewall and network security rules. By automating security policies and continuously monitoring them across multi-cloud and on-premises environments, organizations ensure permissions are granted only where necessary.
Additional Resources
Learn how Tufin automates Zero Trust network policy enforcement and prioritizes mitigation of critical exposures.
Firewall Management Resources
Articles
Solutions
Get Started with Tufin
See how Tufin makes Zero Trust actionable across hybrid and multi-cloud environments.