Securing Your Entire Hybrid Network
Hybrid networks are fragmented, fast-changing, and increasingly complex. Every new cloud service, policy, and connection expands the attack surface and makes it harder to enforce consistent security.
Tufin delivers a unified control plane that provides centralized visibility, risk-aware prioritization, and automated policy enforcement across on-premises, multi-cloud, and hybrid environments. By consolidating policies, detecting misconfigurations, and orchestrating remediation, Tufin helps organizations reduce risk, simplify compliance, and strengthen their hybrid cloud security posture at scale.
Hybrid Cloud Security Use Cases
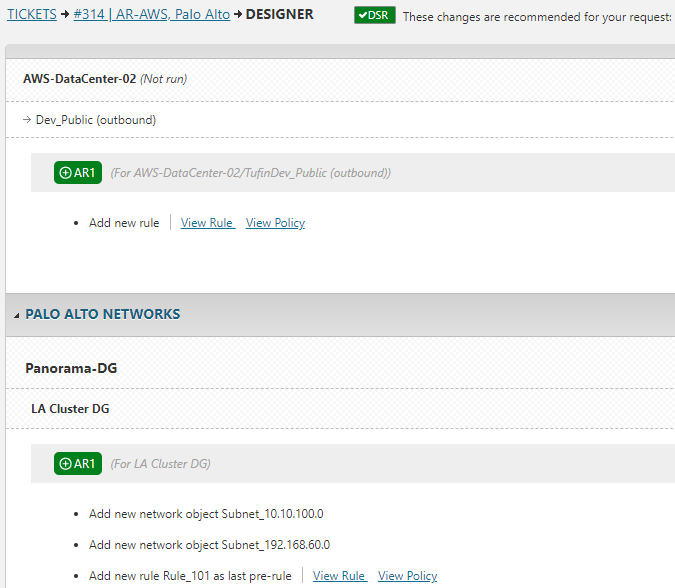
Unify Security Operations
Bring network and cloud teams together with a single source of truth. Tufin’s control plane ensures security policies are consistent, and collaboration is seamless across hybrid environments.
- Apply Zero Trust policies enterprise-wide with confidence.
- Automate risk analysis to speed incident response.
- Eliminate silos with centralized posture management.
- Reduce complexity with unified visibility across environments.
- Ensure continuous alignment with regulatory frameworks.

Streamline Your Segmentation
Simplify and scale segmentation, a cornerstone of Zero Trust. Tufin automates segmentation policies and validates them against posture insights to minimize lateral movement and reduce risk.
- Design, validate, and enforce segmentation across hybrid networks.
- Detect and remediate non-compliant rules automatically.
- Contain threats by isolating workloads, users, and applications.
- Monitor segmentation posture continuously with real-time alerts.
- Reduce exposure without slowing operations or innovation.
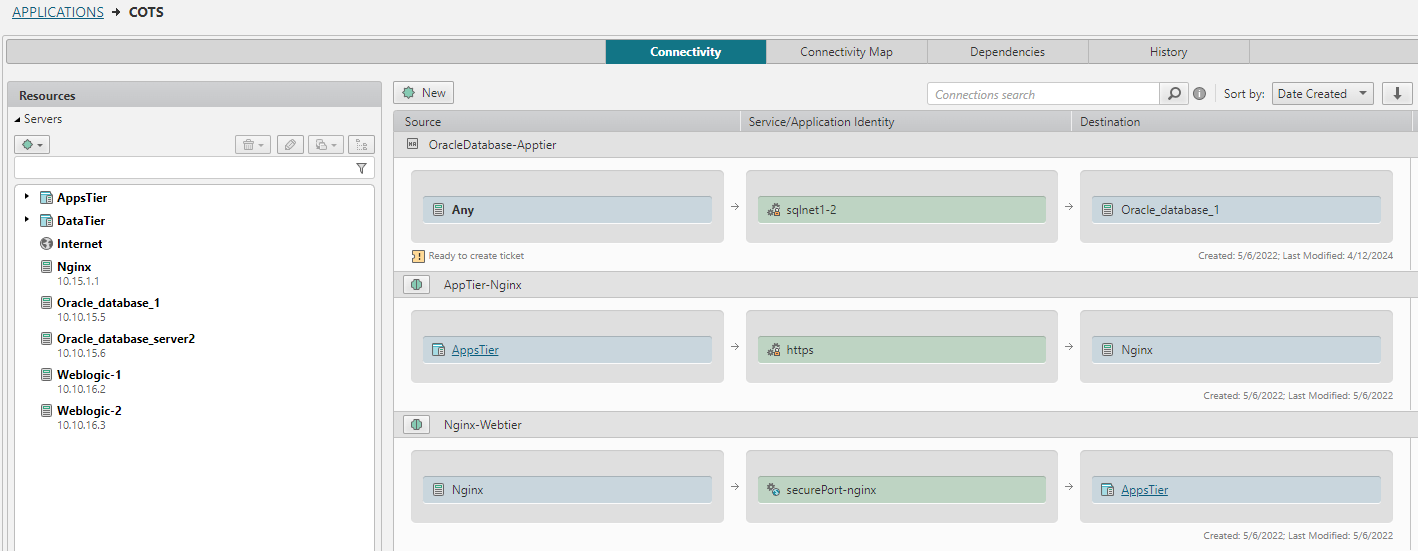
Gain Application-Level Visibility
Understand how applications connect and where exposures exist. Tufin provides real-time visibility into application traffic and posture to help teams secure critical workloads.
- Map application traffic flows across hybrid and multi-cloud environments.
- Identify misconfigurations that expose sensitive data.
- Validate application access paths against Zero Trust policies.
- Gain context for prioritizing remediation of exploitable exposures.
- Support business continuity with reliable, secure connectivity.
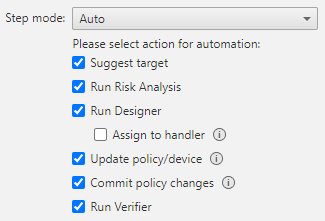
Automate Hybrid Cloud Access
Accelerate business agility while reducing risk. Tufin automates hybrid cloud access changes through the single control plane, ensuring policies are validated before deployment.
- Orchestrate access changes across on-premises, cloud, and edge environments.
- Validate every request against posture and compliance policies.
- Block risky or non-compliant changes before they’re introduced.
- Reduce SLAs from days to minutes with automation.
- Ensure consistent enforcement across firewalls, cloud, and hybrid infrastructure.
How Tufin Delivers Hybrid Cloud Security
The Tufin Platform is a comprehensive, AI-driven solution that provides a unified control plane for network security policy management. The platform is comprised of:
SecureTrack+
See every risk before it becomes a problem — with unified visibility, accurate topology mapping, and continuous risk assessment across firewalls, cloud, SASE, and microsegmentation. Automate policy optimization to reduce exposure and ensure continuous compliance.
SecureChange+
Turn slow, error-prone changes into secure, automated workflows. Accelerate delivery and cut SLA times by up to 90% with automated design, rule lifecycle management, and hybrid connectivity troubleshooting that eliminates delays and misconfigurations.
Enterprise
Scale security without slowing innovation. Automate access provisioning, accelerate application connectivity, and ensure uptime with built-in high availability and global scalability for the largest, most complex networks.
Hybrid Cloud Security with Tufin
With Tufin, organizations move beyond fragmented tools and manual processes to a unified, posture-driven approach. The result: fewer misconfigurations, faster remediation, stronger, and reduced risk — all managed through a single control plane.
FAQs
Hybrid cloud security is the practice of protecting data, applications, and workloads across hybrid cloud environments, which combine public cloud, private cloud, and on-premises infrastructure. It ensures consistent enforcement of security policies, strong access controls, and protection for sensitive data wherever it resides. Hybrid cloud security solutions address security risks such as misconfigurations, unauthorized access, and cyberattacks by applying automation, threat detection, and continuous monitoring across the entire hybrid cloud infrastructure.
Tufin helps organizations secure hybrid cloud architecture by orchestrating firewall and network security policies across cloud platforms, data centers, reducing the attack surface and improving security posture.
- Protect sensitive data stored across cloud services, virtual machines, and on-premises systems
- Mitigate security risks such as ransomware, malware, and data breaches that exploit cloud vulnerabilities
- Ensure compliance with regulations like GDPR, HIPAA, and PCI DSS by enforcing consistent security measures and data protection controls
- Support digital transformation by enabling scalable, secure adoption of cloud-native applications
- Strengthen security posture through automation, remediation, and centralized security tools for hybrid cloud environments
Tufin enables security teams to maintain consistent security across multi-cloud environments like AWS, Azure, and Google Cloud, while also covering private cloud environments and on-premises systems.
Cloud data security is a subset of cybersecurity focused on safeguarding sensitive data stored in cloud services, cloud workloads, and cloud-native applications. It includes protecting data at rest and in motion through encryption, enforcing identity and access management (IAM), applying multi-factor authentication, and monitoring for misconfigurations that could expose data.
In hybrid cloud environments, cloud data security is essential to reduce security risks, prevent data breaches, and ensure data privacy across both public cloud and private cloud systems.
- Misconfigurations in cloud platforms or hybrid cloud infrastructure that expose cloud resources
- Unauthorized access from weak IAM or insufficient access controls
- Malware, ransomware, and other cyber threats targeting apps, endpoints, and cloud workloads
- Data breaches from improperly secured APIs or exposed sensitive data
- Inconsistent security policies across cloud service providers and on-premises environments
- Shared responsibility gaps where organizations and cloud service providers misunderstand ownership of security measures
Tufin reduces these risks by automating enforcement of consistent security across all environments, streamlining incident response and ensuring that security teams can validate and remediate issues quickly.
Multi-cloud security protects workloads and apps running across multiple cloud service providers such as AWS, Azure, and Google Cloud. It ensures consistent security policies, coordinated security controls, and unified threat detection across environments. Multi-cloud security strategies reduce complexity, safeguard sensitive data, and help prevent unauthorized access or compliance violations in multi-cloud environments.
Tufin provides the visibility and orchestration layer that helps organizations apply a unified cloud security strategy, ensuring consistency across all Azure, AWS and GCP cloud platforms.
- Adopt Zero Trust by enforcing strict access controls and applying the principle of least privilege
- Implement segmentation of hybrid cloud infrastructure, data centers, and endpoints to reduce lateral movement
- Use automation and orchestration to streamline workflows, apply remediation in real time, and reduce human error
- Encrypt sensitive data and enforce data protection policies across cloud environments and on-premises systems
- Continuously monitor for vulnerabilities, security threats, and cyberattacks across apps, APIs, and cloud workloads
- Ensure compliance with regulatory compliance requirements by aligning with industry frameworks and benchmarks
Tufin enables organizations to optimize these strategies by automating firewall and security controls, ensuring consistent implementation across hybrid networks.
- Identify and classify sensitive data across cloud resources, apps, and on-premises systems
- Enforce IAM and MFA to secure user access and reduce unauthorized access
- Encrypt data in transit and at rest within hybrid cloud infrastructure
- Apply consistent security policies across cloud service providers, private cloud, and data centers
- Leverage automation to detect misconfigurations, improve incident response, and streamline remediation efforts
- Continuously monitor using threat detection and security tools to address new vulnerabilities and reduce the attack surface
Tufin helps organizations ensure hybrid cloud data security by providing centralized policy orchestration, enabling security teams to enforce consistent controls across hybird environments.
Additional Resources
Discover how Tufin automates security policies, segmentation, and orchestration across hybrid cloud infrastructures.
Firewall Management Resources
Articles
Solutions
Get Started with Tufin
See how Tufin simplifies and secures hybrid cloud environments through unified posture management.






