混合环境的自动化网络安全
适用于大型混合环境的企业级可视性、合规性、自动化和云安全性
了解为什么 Tufin 得到了成千上万名客户的信任





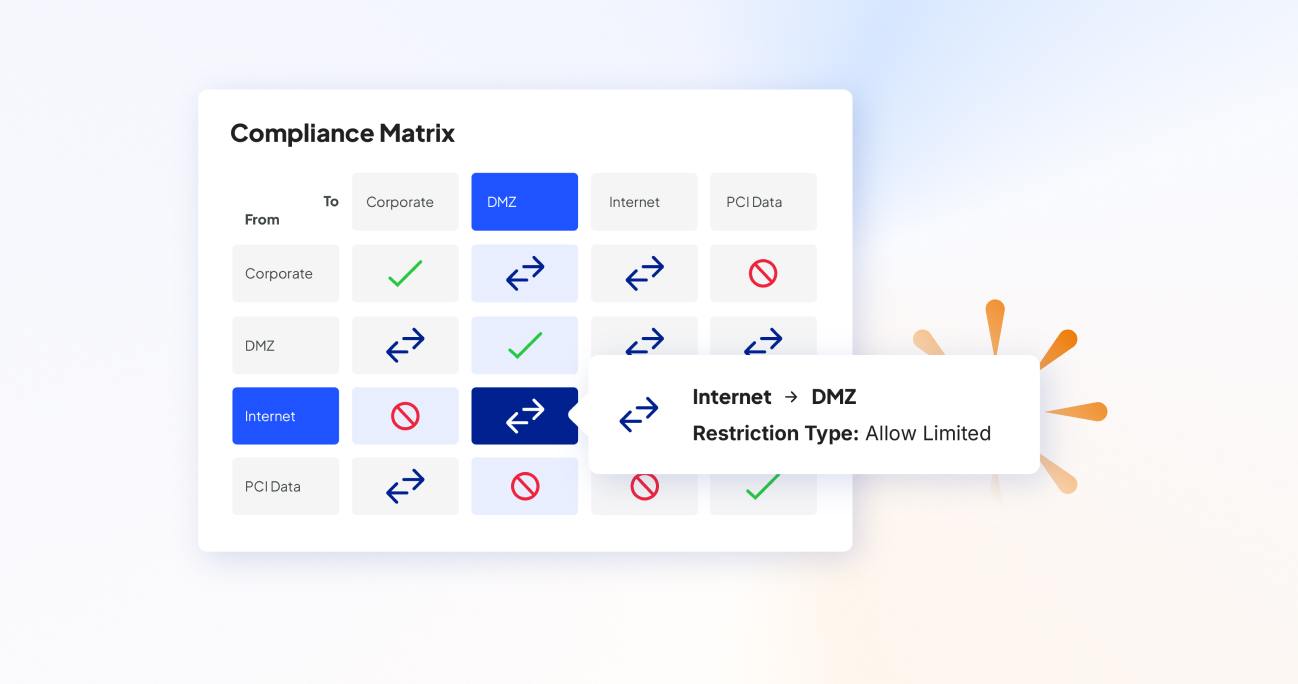
跨混合网络的可靠合规性
提高可见度。 自动化变更。 确保合规。 实现内心的平静。
预防重大问题
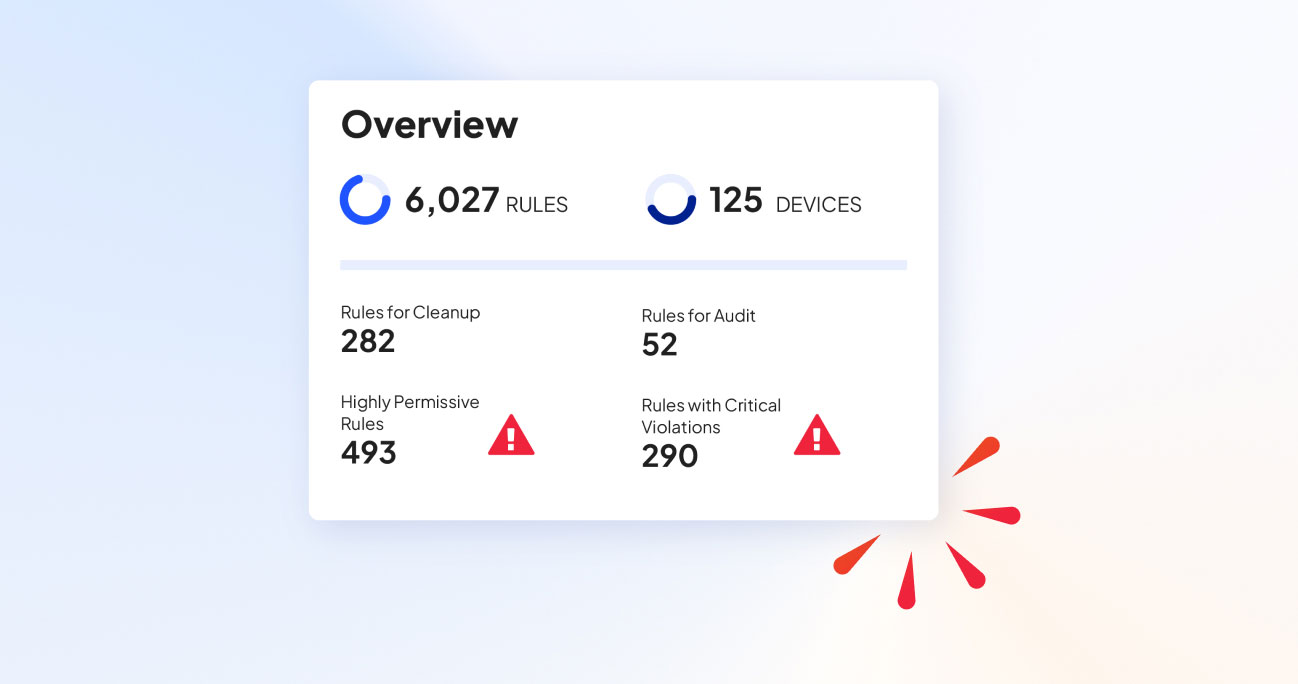
全面了解您的防火墙策略,以便在问题升级之前主动识别和解决潜在违规行为。Tufin 的持续监控和警报系统确保您的策略始终得到执行和保持安全。
增强可视性和自动化
构建一个可在整个网络中自动执行的弹性策略框架。Tufin 确保防火墙策略的一致应用,减少人为错误,并在网络发生变化或中断时保持安全。
满怀信心地解决
使用与不断发展的网络保持同步的自动化工具无缝调整您的防火墙策略。无论是扩大规模、迁移到云端还是适应监管变化,Tufin 的解决方案都能提供适应灵活性,同时保持强大的安全性和合规性。
网络安全综合解决方案
我们的解决方案以强大的防火墙和云策略管理为基础,增强您的网络安全性、确保合规性、自动执行任务并保护混合环境。
获得 Tufin,看得更清楚。
安排您的个性化演示
减少 SLA 时间。提高敏捷性。
无论您是管理防火墙策略、自动执行任务还是保护云环境,Tufin 都能提供适合您特定需求的解决方案
SecureTrack+
防火墙和安全策略管理
使用 SecureTrack+ 推动您的安全策略之旅
- 跨防火墙、NGFW、路由器、交换机、SDN 和混合云的集中网络安全策略管理、风险缓解和合规性监控
- 自动优化策略
- 确定漏洞的优先级并缓解漏洞
SecureChange+
使用 SecureChange+ 增强可视性并自动执行日常任务
- 实现持续合规
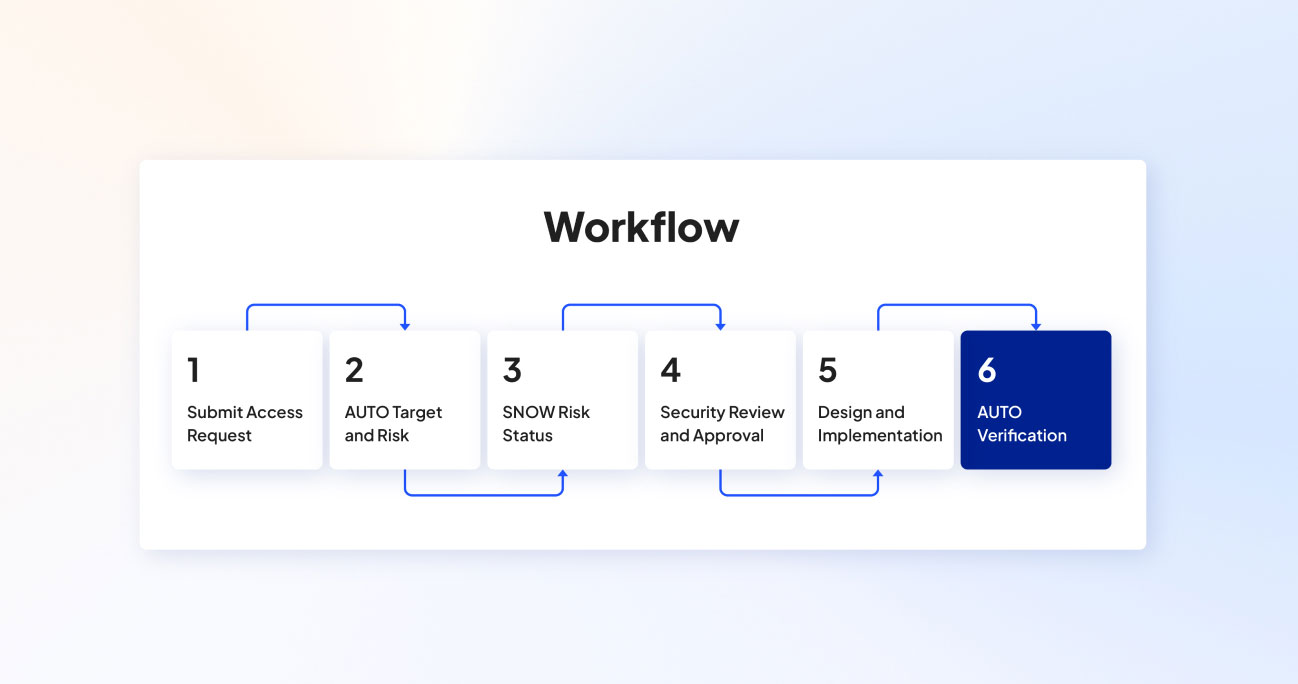
- 通过网络变更设计和规则生命周期管理,将网络变更 SLA 减少高达 90%
- 识别危险的攻击媒介并检测横向移动
- 解决混合云中的连接问题
Enterprise
大规模零信任网络安全
使用企业级解决方案增强您的网络安全运营
- 通过配置网络访问变更实现零接触自动化
- 通过应用程序连接管理更快地部署应用程序
- 利用高可用性和内置冗余最大程度地减少停机时间和数据丢失
案例研究
使用 Tufin 获得真实结果
了解 Tufin 的解决方案如何帮助 IT 专业人员简化操作并增强安全性。
无缝连接您的日常工具
Tufin 可轻松与您日常使用的工具和平台集成,简化您的工作流程并增强您有效管理网络安全的能力。无论您是协调复杂的防火墙策略、确保合规性还是管理多云环境,Tufin 都能将您的所有系统整合到统一而高效的体验中。
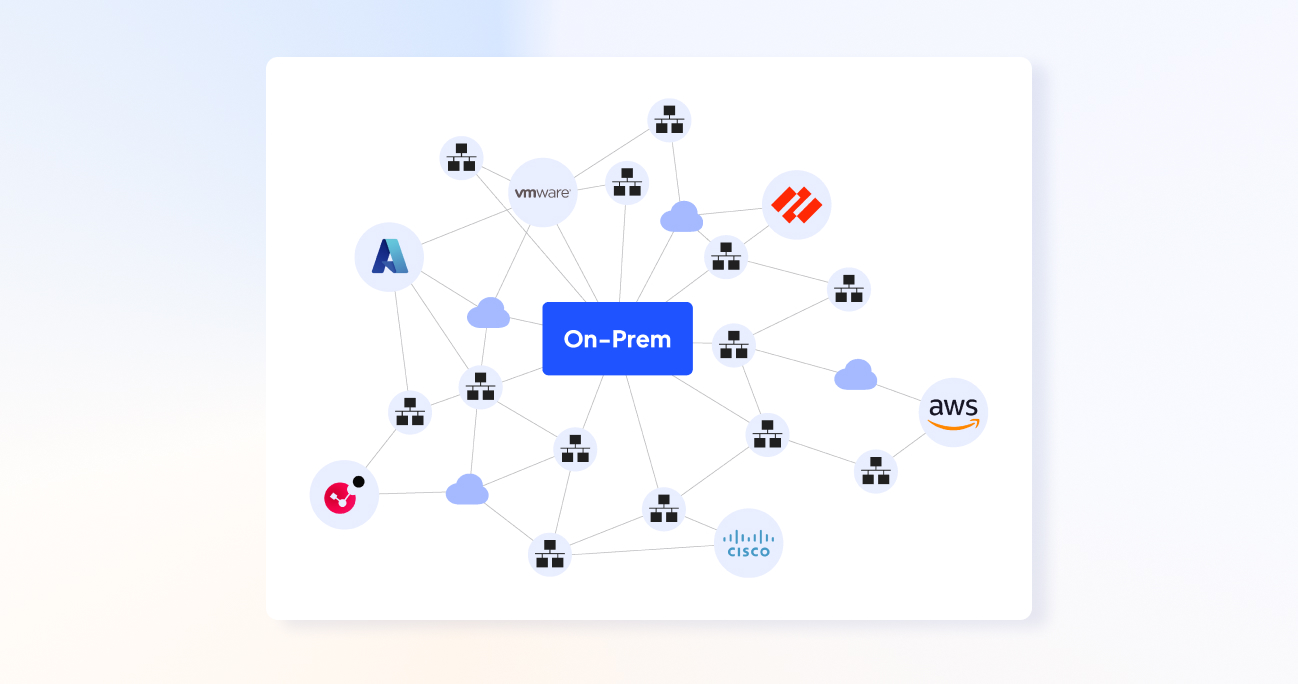
全面的多供应商支持
Tufin 允许您通过单一、直观的界面管理所有主要供应商的防火墙策略,确保一致的实施并降低处理不同网络基础设施的复杂性
无缝合规集成
将 Tufin 与您现有的合规工具集成,以实现审计流程的自动化、持续遵守行业法规并减少合规管理所需的手动工作量。
统一云平台连接
将 Tufin 的安全功能扩展到您的云环境,与 AWS、Azure、Google Cloud 等集成,以确保在集中控制台的所有平台上一致地应用安全策略。
集成安全信息和事件管理 (SIEM)
将 Tufin 与您的 SIEM 工具相结合以整合安全数据,通过对网络安全态势的统一视图,能够对安全事件做出更快、更明智的响应。
防火墙
云
获得 Tufin,看得更清楚。
安排您的个性化演示