Accelerate Your Threat Response Remediation
Traditional vulnerability management solutions flood network security teams with thousands of alerts every day, but lack the context to know which risks matter most. In today’s complex networks, prioritizing exposures and accelerating remediation is a constant challenge.
Tufin provides a unified control plane for enriching vulnerability data with connectivity and posture insights to spotlight the exposures that are truly exploitable.
Why Tufin for Vulnerability Management
With full attack surface visibility, context-aware prioritization, automated workflows, and continuous compliance, Tufin turns vulnerability management from reactive patching into proactive risk reduction.
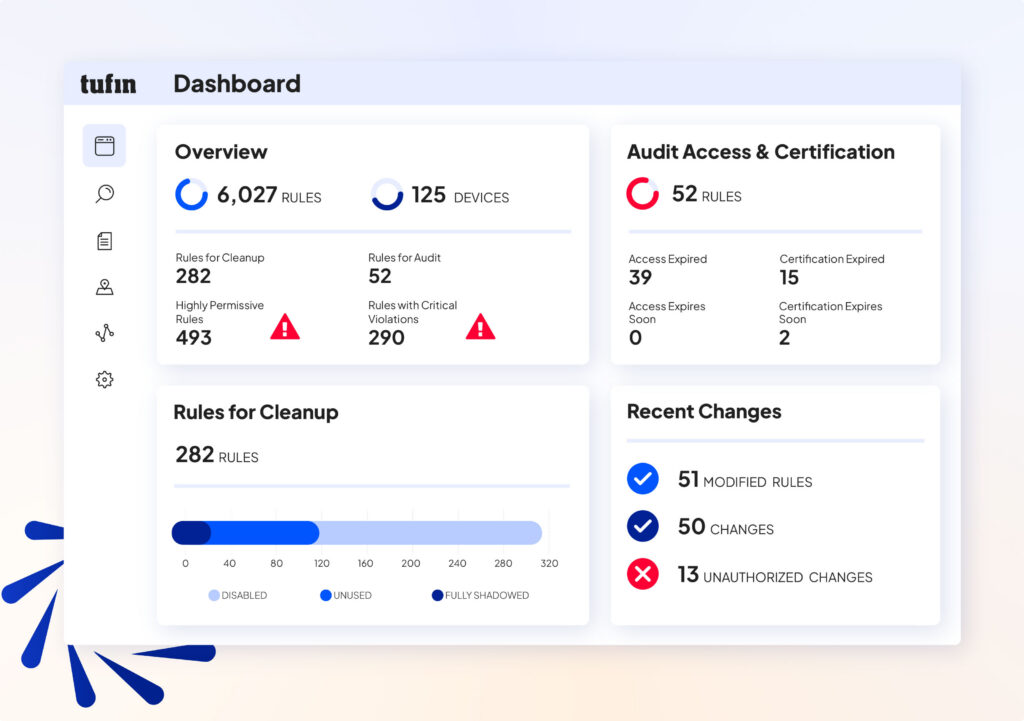
Full Attack Surface Visibility
Consolidate scanner results with network reachability and posture data to eliminate blind spots.
Context-Aware Prioritization
Focus on vulnerabilities that are truly exploitable based on reachability and business impact.
Automated Risk Response
Orchestrate remediation workflows across IT and DevOps tools to cut MTTR.
Continuous Compliance
Map vulnerabilities to frameworks like NIST, PCI DSS, and DORA with audit-ready reporting.
How It Works
Tufin turns vulnerability data into actionable insights by enriching it with posture context, consolidating visibility, and automating remediation to reduce risk faster.
- Add context to scanner data with reachability analysis
- Centralize vulnerability and posture visibility in one dashboard
- Automate workflows that block or fix risky access
- Provide alternatives when patching isn’t immediately possible
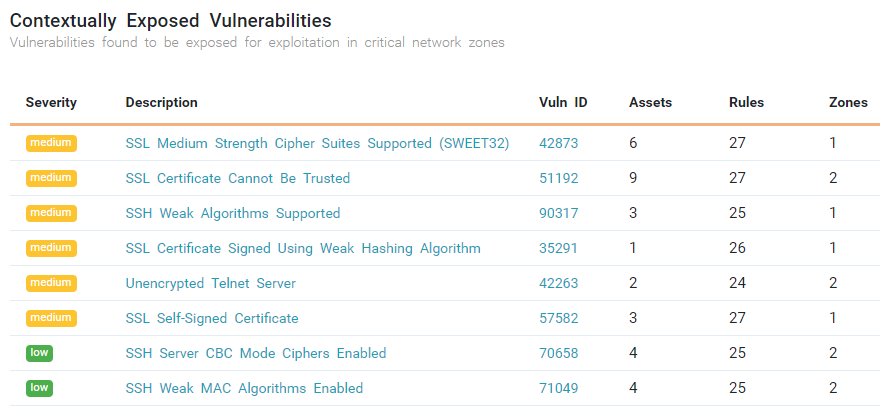
Add Context Where It Matters
Go beyond CVSS scores by identifying which vulnerabilities are truly exploitable, helping teams focus only on what reduces real risk.
- Enrich scan data with network connectivity and posture insights
- Highlight exposures that are reachable and impactful
- Cut through noise to prioritize critical vulnerabilities
- Eliminate wasted effort on non-exploitable findings
A Unified Posture and Risk Dashboard
Gain a single source of truth that merges vulnerability and posture data for faster, more informed decisions.
- Aggregate results from multiple scanners into one view
- Combine vulnerability insights with posture monitoring
- Track exposures across hybrid and multi-cloud environments
- Simplify operations for enterprises and MSSPs
- Drive collaboration with consistent, shared data

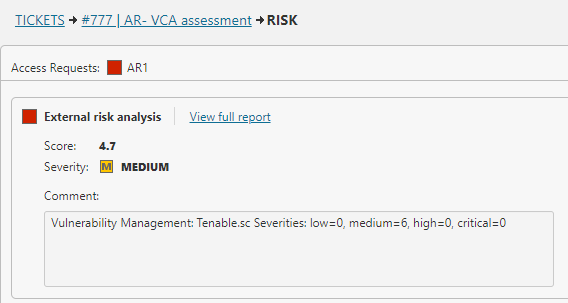
Automate Risk Mitigation
Accelerate response and reduce human error with automated workflows that remediate exposures before they’re exploited.
- Embed vulnerability checks into change workflows
- Automatically block risky access until remediation is complete
- Orchestrate fixes across firewalls, SDNs, and cloud security groups
- Shorten MTTR by eliminating manual steps

Mitigate When Patching Isn’t Possible
Contain risk quickly when patches can’t be applied, keeping business moving while exposures stay controlled.
- Isolate vulnerable assets with automated network controls
- Restrict access paths to prevent exploitation
- Maintain protection until patching is feasible
- Reduce operational disruption while sustaining security posture
How Tufin delivers Vulnerability Management
The Tufin Platform is a comprehensive, AI-driven solution that provides a unified control plane for network security policy management. The platform is comprised of:
SecureTrack+
See every risk before it becomes a problem — with unified visibility, accurate topology mapping, and continuous risk assessment across firewalls, cloud, SASE, and microsegmentation. Automate policy optimization to reduce exposure and ensure continuous compliance.
SecureChange+
Turn slow, error-prone changes into secure, automated workflows. Accelerate delivery and cut SLA times by up to 90% with automated design, rule lifecycle management, and hybrid connectivity troubleshooting that eliminates delays and misconfigurations.
Enterprise
Scale security without slowing innovation. Automate access provisioning, accelerate application connectivity, and ensure uptime with built-in high availability and global scalability for the largest, most complex networks.
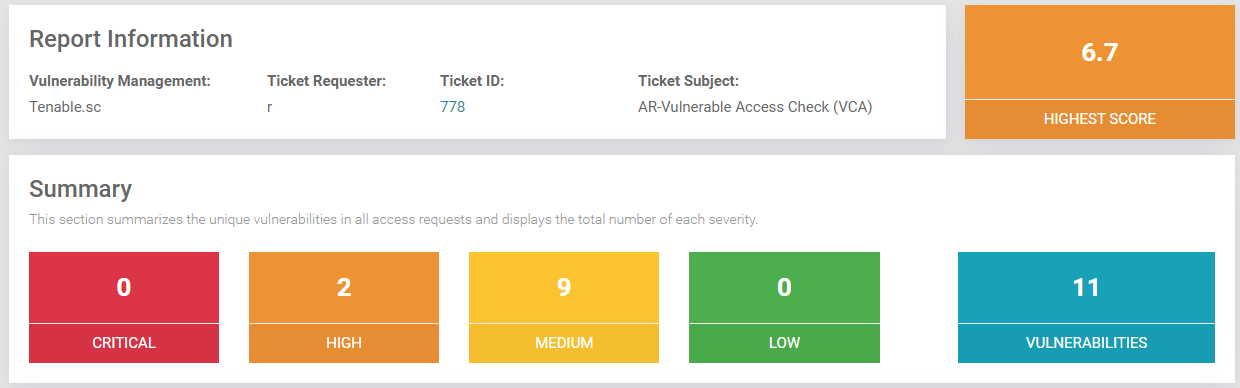
Vulnerability Management with Tufin
With Tufin, vulnerability management shifts from endless patch lists to targeted, posture-aware risk reduction. Organizations gain faster prioritization, fewer breaches, reduced operational cost, and stronger compliance, all from a single control plane.
FAQs
Vulnerability management is a continuous process within cybersecurity that helps organizations identify vulnerabilities, evaluate their criticality, and take action to remediate them. A vulnerability management program typically combines vulnerability scanning, risk-based prioritization, and remediation efforts that improve overall security posture. By addressing known vulnerabilities and monitoring for new vulnerabilities across endpoints, workloads, and cloud environments, security teams can reduce the attack surface and defend against cyber threats.
Tufin supports effective vulnerability management by helping security teams align firewall and network policies with remediation workflows, ensuring that security risks are addressed consistently across hybrid and multi-cloud environments.
- Reduce security risks by identifying vulnerabilities and security weaknesses before they can be exploited by hackers
- Prevent data breaches and mitigate cyberattacks caused by malware or misconfigurations
- Maintain compliance with frameworks like CIS, NIST, and other regulatory requirements
- Support IT teams and stakeholders with dashboards and metrics to measure progress and track remediation efforts
- Strengthen security posture through risk-based vulnerability management and patch management strategies
Vulnerability management solutions give security teams the ability to streamline the vulnerability management process, prioritize vulnerabilities, and coordinate remediation across complex networks and cloud environments.
Vulnerability scanning, as defined by NIST, is the automated process of identifying vulnerabilities in IT assets, operating systems, applications, and cloud environments. Vulnerability scanners detect security weaknesses, misconfigurations, and known vulnerabilities from sources such as the National Vulnerability Database and assign CVSS scores to measure exploitability and criticality.
Scanning is a key step in the vulnerability management lifecycle, helping security teams address vulnerabilities with risk-based prioritization and integrate results into the broader vulnerability management program.
- Configuration vulnerabilities such as weak permissions, open APIs, and firewall misconfigurations
- Software vulnerabilities in operating systems, cloud-native applications, and SaaS workloads
- Endpoint vulnerabilities caused by unpatched devices or outdated antivirus protection
- Network vulnerabilities in flat networks, routers, or segmentation policies that allow lateral movement
- Human-related vulnerabilities like phishing, poor password practices, or lack of validation steps
- Cloud vulnerabilities such as misconfigured cloud environments and exposed sensitive data
Identifying vulnerabilities across all IT assets allows organizations to remediate vulnerabilities faster and mitigate the risk of data breaches.
Vulnerability assessments should be conducted on a recurring basis as part of an effective vulnerability management process. Best practices recommend:
- Regular scanning cycles for all operating systems, endpoints, and workloads to identify vulnerabilities and known exposures
- Real-time validation of critical vulnerabilities to mitigate immediate risks
- Continuous monitoring of cloud environments and IT assets to address new vulnerabilities as they appear
- Periodic penetration testing to validate the effectiveness of vulnerability management tools and remediation efforts
- Lifecycle tracking with metrics and dashboards to measure improvements in security posture over time
Organizations that prioritize vulnerabilities based on exploitability, criticality, and risk scores can remediate vulnerabilities more effectively, reduce their attack surface, and prevent cyber threats.
Additional Resources
Learn more about how Tufin integrates vulnerability and posture insights to prioritize and remediate critical risks.
Firewall Management Resources
Articles
Solutions
Get Started with Tufin
See how Tufin unifies vulnerability and posture management to make risk reduction practical and measurable.