What’s common to all cloud migration projects, whether they are lift-and-shift, migration between cloud platforms, or app refactoring projects, is that the end results are portable workloads (e.g. application, database, storage, VM, etc.) cloud-native or not, that can potentially run in the cloud, or on-prem. This is a very agile operation, completely abstracted from the underlying infrastructure. The same principle is valid for the security policy. Simply put, your security policy should be applied to apps/workloads, irrespective of their location in the network.
Here are some tips to help you implement a secure migration process when migrating apps to the cloud or deploying them in a hybrid network:
1. Discover apps, map out traffic, and identify security gaps
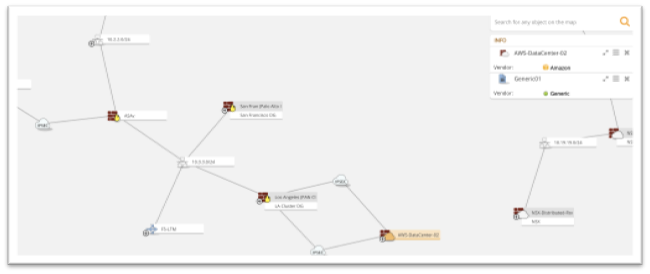
The first step to help you migrate apps efficiently is to understand which cloud platforms are used, what apps/workloads are running across your hybrid environments, and how they connect.
This type of visualization will help you discover apps you might not have been aware of, plan your segmentation policy more effectively, and identify security gaps (firewalls with any-any rules or an unmanaged server that was not removed) and network configuration errors.
Using Tufin’s auto discovery capability, you can visualize your network topology and use it to optimize and troubleshoot network configuration issues before migration. Tufin analyzes firewall revisions and network traffic to reveal the communication paths (sources and destinations) associated with servers and apps. If an issue is detected, Tufin will provide actionable remediation information for fast mitigation.
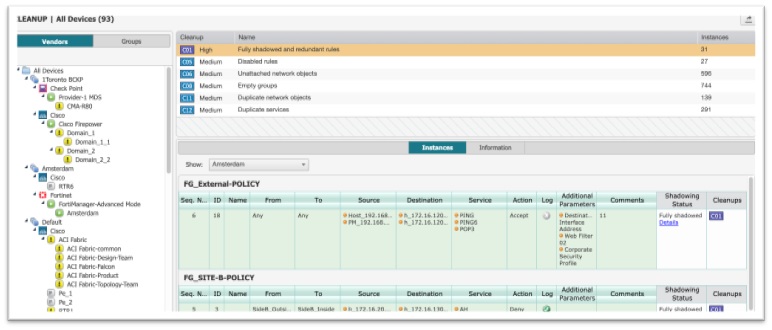
2. Clean up rules and reset firewall policies
With real-time visibility into apps, network devices, and traffic flows, you can start assessing firewall rules, and detect and troubleshoot broken connectivity or misconfigured rules. Ideally, you want to enforce least privileged access. Therefore, look for shadowed, redundant and overly permissive rules, and unused or unattached objects in the environment.
Tufin SecureTrack provides relevant information, such as rule permissiveness level, last hit, last modified, shadowing status, tech and business owner, rule description and more.
In addition, you can query the existing firewall rule base to identify rules that have been decertified and are no longer needed so they can be decommissioned.
Tufin also recommends modifications to rules and offers an audited change workflow to ensure changes are fully documented and vetted.
A recommended starting point would be to apply a rule clean-up process to the relevant apps/workloads that need to be migrated. At a later stage, you can continue to do this for other assets within your environment.
3. Define app profile baseline and establish security policy
It’s also helpful to learn more about the apps/app tiers you are about to migrate, such as their location, connectivity requirements, status, and dependencies.
Using Tufin SecureApp, you can automatically discover and build a repository of all apps and their dependencies, displaying real-time traffic flows.
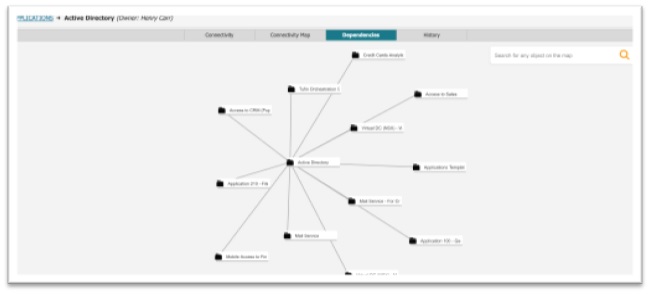
What’s more, Tufin observes how the app behaves across the hybrid environment and automatically documents and generates a recommended access policy that can be used as a baseline before migration.
When an app/workload is migrated from on-prem to a cloud environment, Tufin also identifies the changes needed to the physical firewalls and the new settings required for cloud security groups. This enables you to migrate workloads/apps across the hybrid environment with consistent security policies that follow the workloads and can scale automatically.
For cloud-native apps, Tufin’s cloud solution enables micro-segmentation, full visibility and control of workloads and traffic within the same environments or across clusters and clouds. Policies are automatically applied to workloads, services, and cloud resources based on tags, security groups, namespaces, etc.
4. Analyze the risk and start the migration process
Making changes to a server IP address or moving an app web tier to the cloud, for example, might involve changing physical firewalls, perimeter firewalls, distributed firewalls, and security groups. We all know that this is a complex, time‐consuming and error‐prone process.
You can start the process by opening a ticket in Tufin. Tufin SecureChange then automatically identifies the policy rules that need to be changed or removed across all affected security groups, firewalls and routers, if needed. Tufin then simulates the change and conducts impact and risk analysis to ensure the proposed change is aligned with your organization’s security policy and does not introduce new risks into the network.
Once the change is approved and vetted against the security policy, Tufin enforces and validates implementation of the change.
5. Patch before run
Prior to implementing the change, a good security best practice is to add an automated check to the change request workflow to verify if the proposed migrated app/workload has any known vulnerabilities or configuration issues (e.g. configured with root privileges). Tufin integrates with the most commonly used vulnerability management solutions, such as Tenable, Qualys, and Rapid 7, to retrieve vulnerability data on the workload for early assessment prior to migration. In case vulnerabilities are detected, Tufin will alert for further investigation, and the security team can decide whether to accept or reject the change.
In conclusion, the steps above are an integral part of an automated process that offers an effective and easy way to avoid a manual and typically labor-intensive cloud migration process.
To learn more about Tufin’s recommendations to help you through your cloud migration project, check out our Practical Guidelines to Security Policy for Your Cloud Environment webinar.
Ready to Learn More
Get a Demo





