Zero Trust is a popular term seen everywhere lately, but it’s not a new concept. The Zero Trust Network, or Zero Trust Architecture model was created in 2010 by John Kindervag who was a Forrester analyst. Eleven years later, CISOs and CIOs are increasingly adopting and implementing the Zero Trust security model into their organizations.
The Zero Trust model suggests we shift security from a perimeter-based model to a model that’s based on continuous verification of trust. Actually, this model assumes that a network has already been breached. A key recommendation is to create micro-perimeters or micro-segments to control access to sensitive assets, and limit the potential damage from attackers.
Over the years, Forrester extended the original model beyond its segmentation focus to include other elements to ensure only the right people or resources have the right access to the right data and services, such as:
- Data – Categorize and classify data based on sensitivity; they also mention data encryption
- Workloads and Devices – Apply Zero Trust controls, such as encryption and data security
- People/Identities – Limit and strictly enforce access controls
- Network – Identify sensitive, valuable assets, and define micro-segmentation around them
- Visibility & Analytics – Log, correlate, and analyze every activity across environments
- Automation & Orchestration – Implement automation, and integrate with other tools to improve detection and response
As a CISO, I’ve often been asked how I translate Zero Trust principles into practice. So, here’s my take on the Forrester Zero Trust 5-step implementation method.
Zero Trust Implementation: 5-Step Method
- Identify your Sensitive Assets
The first step is about identifying and prioritizing the most valuable assets, which also require the highest level of protection (the protect surface vs. the attack surface). This is where I involve other business stakeholders to help me identify what and where these assets are. Keep in mind, this process is complete only after management team’s approval.
Here’s how I think and how I‘d also present Zero Trust to the board:
- What are the sensitive assets? List the mission-critical, valuable assets that could cause the most damage if compromised. Valuable assets can be data, such as credit card data, PII, PHI, financial data, and more. But, it’s not limited to data only — it can be your legacy systems where the primary business transactions take place. By the way, the definition of sensitive, critical, or valuable assets is completely subjective. If you ask your CRO, the answer would likely be customer data, but if you ask the CFO, it may be financial data. At the end of the day, it’s ultimately about what can kill you vs. what can harm you.
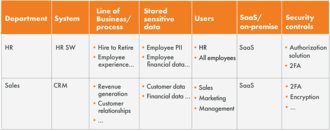
- Which lines of business or processes is the data used for? Consider the processes use these sensitive assets such as customer relationships, employee experience, revenue generation, regulatory compliance, and others. For example, it is important to understand if a compromised code repository could result in a regulatory violation and litigation.
- Who currently has access? Which users currently have access? Are they privileged users or not? Consider the potential number of affected users in case of a breach.
- Where does the data reside (SaaS or on-premise)?
- What are the current security controls? Which controls are in place, so we can identify the gaps, and take action?
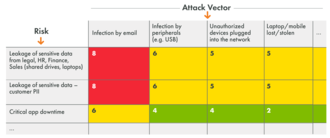
Next, I use this simple probability matrix below to map the risks (in the first column), and list the attack scenarios based on probability along the top. This is a great summary of the most critical risks that have the highest probability to occur. This is also a simple matrix that you can present to the board or the management team.
Here, in the second column, we can see that the highest probability for data leakage is due to infection by email. This type of matrix will help you identify and prioritize how you use your resources.
- Map the main business flows of your sensitive assets
This step is about mapping out and visualizing communication flows across the hybrid, multi-cloud environment. It’s a complex, time consuming process to identify all the assets in the network, and figure out how they communicate. By analyzing the traffic, however, we can build a blueprint for the access controls and segmentation policies.
This is where I use Tufin. Tufin provides a centralized console that helps me gain end-to-end visibility and create an accurate topology map that provides clear insights into what is deployed where, and what talks to what (workloads, applications and their dependencies, network control points, and more) across the hybrid environment. It saves a lot of time and provides a highly-accurate model of the environment to jumpstart or modify the segmentation project. One important note here — the more accurate the topology, the less likely it is to break something when putting security controls in place.
- Building the Zero Trust architecture segmentation
In this step, the architecture is segmented by looking into all sub-networks and deciding if we want to separate them even further. It is also important to decide where to implement additional security controls, such as MFA, PIM, and more. For this stage in the process, Tufin lets you assess current segmentation rules, and detect misconfigured, overly- permissive, unused, redundant, shadowed rules, and others.
Tufin provides relevant information, such as last hit, last modified, shadowing status, rule description, and more, all of which helps reduce risk and better modify the rule base.
In addition, the Automatic Policy Generator (APG) from Tufin inspects traffic flows to optimize existing policies or automatically generate new policies which helps clean up and redesign segmentation.
For every new rule or rule change, path analysis and what-if analysis highlights the potential impact of the change across the multi-vendor, hybrid environment.
- Creating the Zero Trust policy
This step is about creating the Zero Trust security policies that ensure only the right people or resources have the right access to the right data and services across the hybrid environment. This is where you want to ensure your policies fit to protect your critical assets.
Tufin can help create segmentation policies. For IP-based segmentation, the Tufin Security Policy matrix creates a security policy to control what traffic is allowed between zones.
- Continuously monitor and maintain Zero Trust environment
The last step is about ensuring an up-to-date rule base by continuously monitoring, and automating changes, if needed. When infrastructure is complex, it is impossible to manage security without automation. Rules continuously change, and should be reviewed on a regular basis to remove and update them as required. This is almost impossible without a holistic, accurate topology.
The truth is, most security teams do not change or decommission rules out of fear of causing a problem. And, over time, you have hundreds of rules that are impossible to manage manually, and are no longer relevant to current business needs and communication flows.
It’s essential to monitor all aspects of the network, in order to detect policy violations, such as unauthorized access changes, or overly-permissive rules. In addition, it is critical to identify highly-connected and vulnerable assets so you can prioritize and apply effective remediation.
In addition to using Tufin to centrally manage segmentation policies, Tufin SecureChange+ can implement changes quickly and automatically. This actually saves us a huge amount of time.
With SecureChange+, every change is designed on the most optimized path and vetted to ensure it meets security and compliance mandates. No human finger in the pot, and no changes are allowed outside of the federated process. All changes are then automatically implemented to all relevant firewalls, cloud-native firewalls, security groups, and beyond, to ensure an accurate, error-free process.
On a final note, I’m often asked how to best initiate a Zero Trust project, and my response is always the same – start small, and start fast. It’s important at the get-go to achieve some level of success. If you’re able to quickly show the management team or the board ZT’s real added-value, you’ll gain their trust – and you might even be granted the resources to expand your ZT deployment beyond what you expected.
For me, it’s always a great pleasure to talk about Zero Trust.
You can also drop me a line – eitan.satmary@tufin.com
Have a great summer!
Eitan
Ready to Learn More
Get a Demo





