Gartner recently published three research papers about network security policy management and orchestration. As market leaders and pioneers in this space, this is an important milestone as we believe it recognizes our continued investment and validates the market need.
The research papers were written by different analysts with different perspectives. Based on my experience their perspectives also reflect the way our enterprise customers (over 2,000) use our solutions for three different, but related business needs (see diagram): security policy management, infrastructure protection and network orchestration:
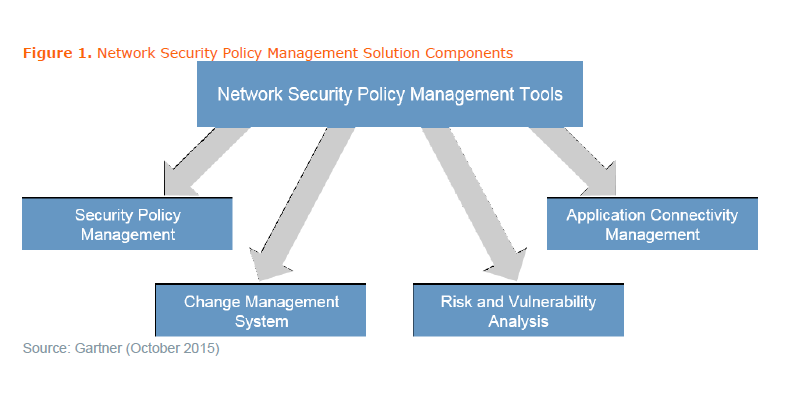
Network Security Policy Management Solutions Have Evolved
The report “Network Security Policy Management Solutions Have Evolved” was published on October 30, 2015 by analysts Adam Hils and Rajpreet Kaur.
This research discusses how network security policy management tools help network security operations with firewall policy management, complex policy change workflows, compliance audit and management of multiple firewall vendors.
- “Many firewalls have thousands of rules accumulated over years of deployment and changing access control lists (ACLs); these rules are often obsolete, conflicting or redundant, impacting a network’s performance and availability, and therefore your business.”
- “As networks grow, applying the right security policies at the right network control points is challenging. Multiple native-point solutions are difficult to maintain. Network security policy management (NSPM) solutions can provide visibility across the dynamic network, and can make policy provisioning easier.”
- “Applications play a critical role in a digital business, and their availability has become very important for business continuity. NSPM tools provide application-based visibility and control, making management of application connectivity easier.”
In 2012, we introduced the first solution for application connectivity management, Tufin’s SecureApp, which is now considered a core component of Network Security Policy Management.
According to the report, “With more business reliance on applications, end-to-end application productivity management tools provide application-based management capabilities to reduce security risks while improving availability. Application-based change request and application connectivity path visualization are examples of the utility of this technology.”
Not surprisingly, the research also mentions the shift to the Cloud: “With infrastructure and associated security controls moving to the cloud, some vendors also support security management of public cloud, such as Amazon Web Services (AWS) via APIs.”
Tufin currently supports Amazon Web Services (AWS), Symantec, Check Point, Cisco, F5 Networks, Fortinet, Forcepoint, Netfilter/IPtables, Juniper Networks, Microsoft Azure, Palo Alto Networks, and VMware.
Effective Network Orchestration Starts by Automating Provisioning
Another excellent Gartner research paper authored by Simon Richard on August 31, 2015, “Effective Network Orchestration Starts by Automating Provisioning”, has mentioned Tufin as a policy-based network orchestration system.
This research discusses available methods to start automating network provisioning now. According to the report, “network automation is required to provide network agility, which in turn is required to provide data center agility. Increased agility is a top priority for the business, and network organizations must start to automate now.”
Hype Cycle for Infrastructure Protection, 2015
“Hype Cycle for Infrastructure Protection, 2015”, by Greg Young, Adam Hils & Neil McDonald, published on August 11, 2015 provides a comprehensive overview of security technologies and services available to protect enterprise IT:
“New this edition are the technology profiles for Network Sandboxing, Network Traffic Analysis, Firewall Policy Management and Threat Intelligence Platforms. All but the last are established technologies; however, their inclusion highlights their more focused place and increased demand in the security landscape.”
If you are a CIO, CISO or security manager, I recommend reading these research reports. We believe they provide a good overview of current challenges and technologies for securing the enterprise in the most effective way.
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Ready to Learn More
Get a Demo





