Enhanced Next-Generation Firewall and SDN Support
We recently released Tufin R19-2 with new features and improvements, a result of customer feedback and requests. R19-2 highlights include management of dynamic objects, integration with Cisco ACI to deliver full visibility and monitoring, and advanced next-generation firewall support.
Enhanced visibility and topology modeling for Cisco ACI
One of the newly added features enables you to gain centralized visibility and real-time monitoring of the Cisco ACI Fabric in the context of your overall IT environment. This helps to accelerate the adoption and bridge the gap between the Cisco ACI and the rest of your IT environment.
You can easily add the Cisco ACI as another environment to manage directly from Tufin by connecting to the Cisco Application Policy Infrastructure Controller (Cisco APIC). The ACI Fabric will be automatically added into the Tufin topology map, providing a graphic display of the Fabric — EPGs and applications, including traffic traversing the ACI fabric along non-ACI devices, and network zones.
Once the ACI Fabric is added, Tufin immediately starts documenting any changes that are made to the Fabric, so you can begin tracking Fabric- related revisions (e.g. if a contract was deleted from the policy).
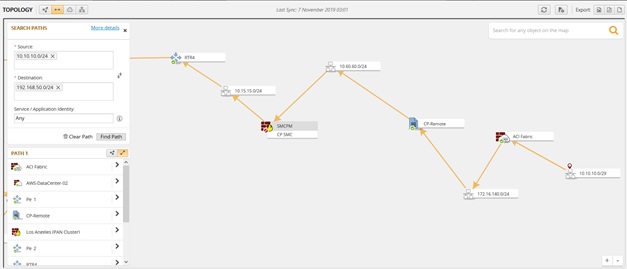
Cisco ACI topology with external routes
Ready to Learn More
Get a Demo





