Today, enterprises are increasingly turning to Next-Generation Firewall (NGFW) features with the goal of moving toward a more proactive user and application-aware approach to enterprise security. A long-term Palo Alto Networks partner, Tufin provides some of the industry’s best support for PanOS and Panorama security policy management, namely NGFW feature support within these products. In addition to our PanOS and Panorama support, Tufin is a founding member of the Palo Alto Networks Fuel User Group, a user-led, non-profit group exclusively for PAN customers interested in advancing their knowledge of information security, primarily in the cloud.
Let’s take a look at some of the most common Palo Alto Networks NGFW features and how they can be managed from the Tufin Orchestration Suite to enhance enterprise networks’ security posture.
Role of App-ID in access management
Palo Alto Networks uses multiple techniques, including application signatures, decryption, protocol decoding, and heuristics, to identify applications, and application functions. These applications and application functions are identified by their App-ID, allowing security admins to create granular application-aware security policies, transition to a positive enforcement model, and apply extra scrutiny to unknown traffic.
Tufin SecureTrack provides complete visibility into App-IDs and their use within the enterprise’s security policies, including support for custom applications. Admins can quickly identify where App-IDs are used within the entire policy base, and immediately identify potential compliance violations via the Unified Security Policy. SecureTrack can also display “last hit for App-ID” information per-policy, enabling security admins to identify App-IDs which may no longer be required for a particular policy, and may indicate overly permissive access.
User-centric security policy management
With an increasingly distributed and mobile workforce, traditional methods of identifying users, such as by IP address, are no longer effective. Palo Alto Networks gathers information from various sources including, VPNs, WLAN controllers, captive portals, directory servers, proxies and more, to generate a User-ID, which can be used to uniquely identify a user as they traverse physical and network locations.
As with App-IDs, SecureTrack provides complete visibility into User-IDs and their use within the enterprise’s security policies. SecureTrack allows admins to visualize security policies that apply to individual User-IDs, painting a picture of the user’s effective access across the entire enterprise network, inclusive of legacy devices, regardless of the user’s location.
Below is an example of the ability to see policies based on UserID (admin):
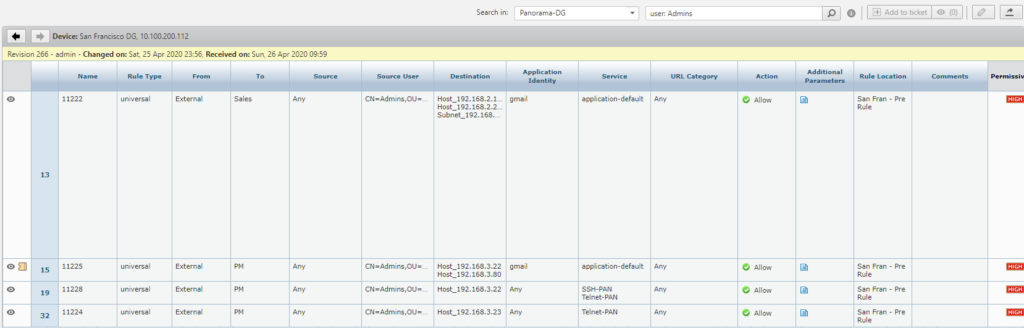
Content-based access and policy management
Palo Alto Networks Content-ID technology delivers a new approach to NGFW security based on a complete analysis of all allowed traffic, using multiple advanced threat prevention technologies in a single, unified engine. The user and application visibility and control of App-ID and User-ID, coupled with the content inspection enabled by Content-ID, empowers IT teams to regain control over application traffic and related content
SecureTrack delivers insight into Content-IDs applied to security policies across the policy base. Understanding how these Content-IDs are utilized by the enterprise’s security policies is critical to accurately assessing overall network security, as well as the effective access permitted by each policy.
Here you can see how Content-ID is supported in the use of App-ID and User-ID:
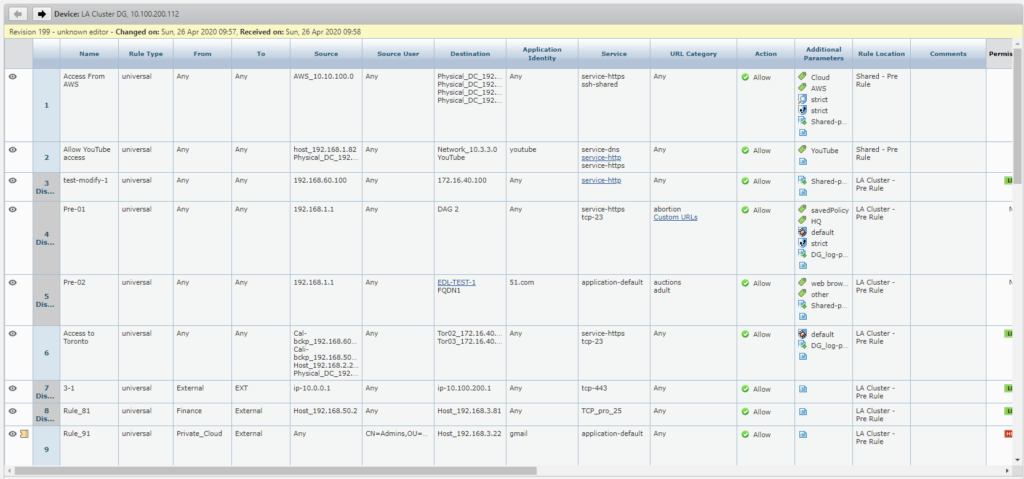
In addition to App-ID, User-ID, and Content-ID, SecureTrack supports many other NGFW features within PanOS and Panorama. These features include FQDN, URL Categories, Dynamic Address Groups, Tags, Custom Applications, and External Dynamic List management.
Each of these features are also fully supported by Tufin SecureChange. With SecureChange, security admins can make use of these Next-Generation features as they implement security policy changes across the hybrid network and perform ‘What-if’ analysis based on App-ID to determine policy change impacts earlier in the process. In today’s ever-changing landscape, the combination of these advanced features from Palo Alto Networks and Tufin SecureChange allows enterprises to maintain business agility, while detecting and blocking even the most sophisticated threats.
To learn more about Tufin’s support for PanOS and Panorama, and how your organization can best deploy cutting-edge NGFW capabilities, check out Tufin Security Policy Automation for Palo Alto Networks Next-Generation Firewall.
Ready to Learn More
Get a Demo





