Tufin vs. Algosec Comparison
When evaluating network security policy management (NSPM) platforms, two of the most well-known names are Tufin and AlgoSec.
Both vendors provide solutions for firewall policy management, risk reduction, and compliance across hybrid cloud and on-premises environments. However, there are key differences that make Tufin the more scalable and extensible option for large, complex enterprises.
Why Choose Tufin?
Tufin delivers advanced network segmentation and application connectivity insights that help security teams design and enforce a Zero Trust security strategy at scale.
The global leader in firewall management for hybrid-cloud and edge networks, Tufin, boasts the most extensible features, including:
Broadest Vendor Coverage
Support for traditional firewalls, next-generation firewalls (NGFWs), SASE, SD-WAN, SSE, and cloud-native controls.
Most Flexible Change Process Customizations
Enabling risk-aware and automated firewall rule management.
Widest Variety of Network Automation Functionality
Including firewall automation, application-centric access controls, and security compliance workflows.
Most Extensive Range of Partner Integrations
Through a robust API ecosystem that supports SIEM, SOAR playbooks, vulnerability scanners, and ticketing systems.
Network Security Posture Management Use Cases
While both Tufin and AlgoSec address firewall policy management and compliance, the two diverge in critical areas:
For organizations adopting cloud security policy management alongside traditional firewalls, Tufin’s broader vendor coverage and deeper automation deliver more long-term value.
Features Comparison
Fully customizable out-of-the-box change management automation workflows
Complete Cisco SD-WAN network model
Detailed topology mapping and cloud security automation, including full scalability
Out-of-the-box vulnerability scans and third-party intelligence
Automatic audit-ready rule documentation updates
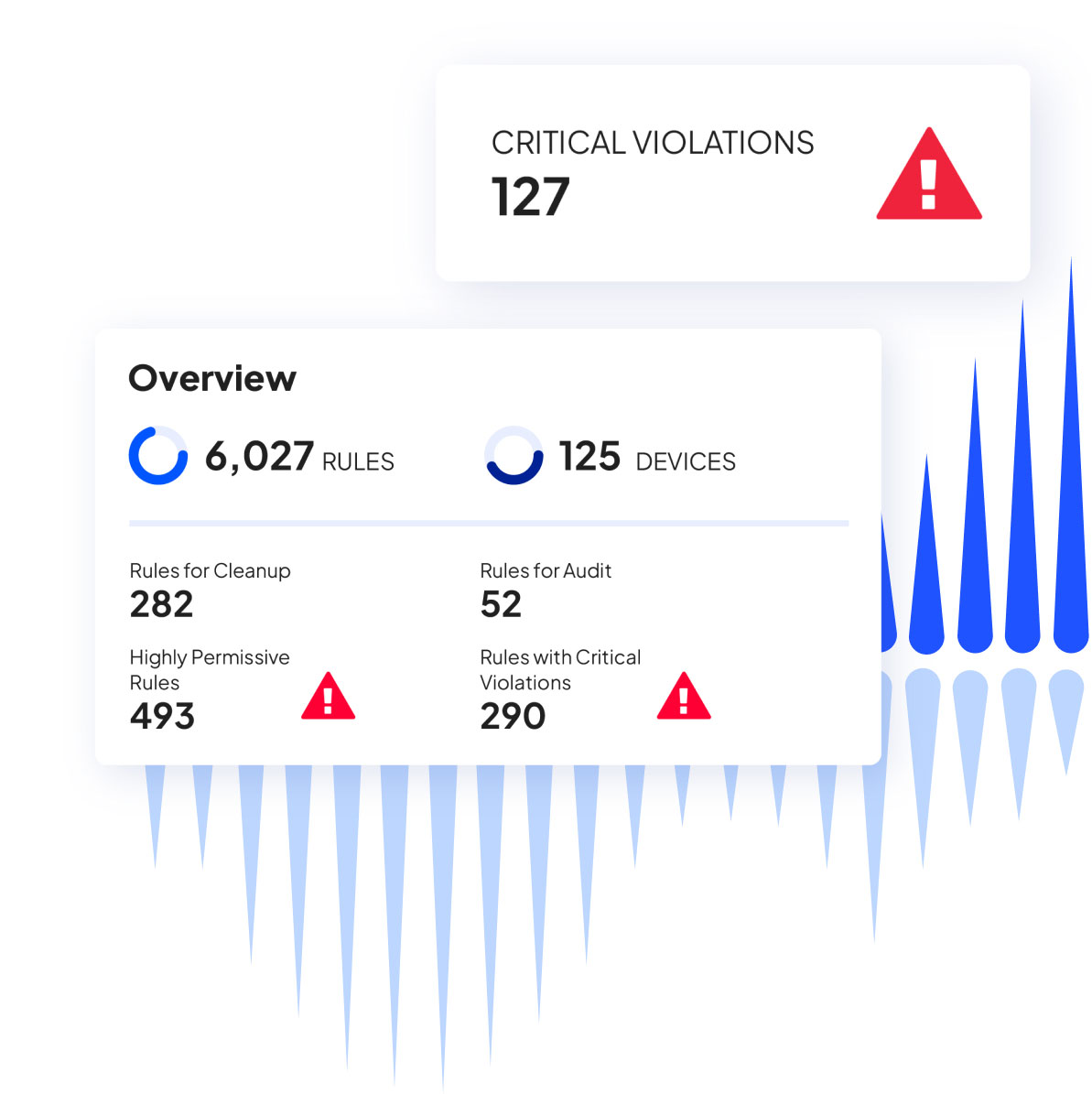
Rule and object cleanup reporting
Rule and object cleanup automation
Scheduled firewall policy installation
Regulatory compliance reports
Automatic real-time change tracking
Automatic discovery of application connections
Monitoring of 250M routes and over 10K devices
We looked at a number of [automation] products, including the one that we had at the time. They always fell short. Tufin finds the optimal route, implements the change, and validates the change [as] planned, reducing our SLA from several days to a couple hours.
Learn Why Tufin is the Market Leader
Find out why thousands of customers trust Tufin





Tufin Drives Results
144%
ROI with a less than 6-month payback period
94%
reduction in effort for network change analysis and implementation
80%
reduction in risk of vulnerability- related breach
95%
audit preparation and reporting efficiency gain
75%
reduction in application connectivity management effort
85%
reduction in effort for ongoing rule maintenance
Summary
When comparing Tufin vs. AlgoSec, the key differentiator lies in Tufin’s ability to combine visibility, automation, and policy intelligence across the widest range of technologies, from legacy firewalls to cloud-native controls.
Organizations looking for scalable firewall policy management, application-aware automation, and stronger support for hybrid-cloud environments consistently find Tufin to be the more future-proof choice.
By unifying policy, compliance, and automation in one platform, Tufin helps enterprises reduce risk, streamline operations, and confidently move toward a Zero Trust security model.
FAQs
Tufin enables its customers to gain end-to-end visibility, automate policy management, and mitigate risks across their global hybrid network, from traditional enterprise firewall infrastructure to modern cloud environments and CI/CD pipelines – without impacting speed or agility.
Tufin SecureTrack+ centralizes network security policy management, risk mitigation, and compliance monitoring across firewalls, NGFWs, routers, switches, SDN, SASE and hybrid cloud environments.
Tufin is the most extensible solution in the NSPM market, supporting virtually any vendor, including Cisco, Palo Alto Networks, Check Point, Juniper, Fortinet, Google Cloud, Microsoft Azure, and many more. This breadth surpasses AlgoSec’s vendor coverage.
Tufin Orchestration Suite provides the business application context for managing network connectivity and security. By linking applications directly to security policy, Tufin eliminates the complexity of traditional firewall rule changes. This approach also supports compliance management, reduces human error, and accelerates secure cloud migration.
Tufin’s network topology map provides visibility and context others can’t match, supporting customers with thousands of devices and global hybrid networks. This topology-driven approach enables more effective risk management, policy clean-up, and segmentation design.
Tufin automates firewall change requests across firewalls, rules, and security groups, while empowering you to control the level of automation and oversight. This ensures faster SLAs and fewer misconfigurations, compared to AlgoSec’s narrower change automation workflows.




