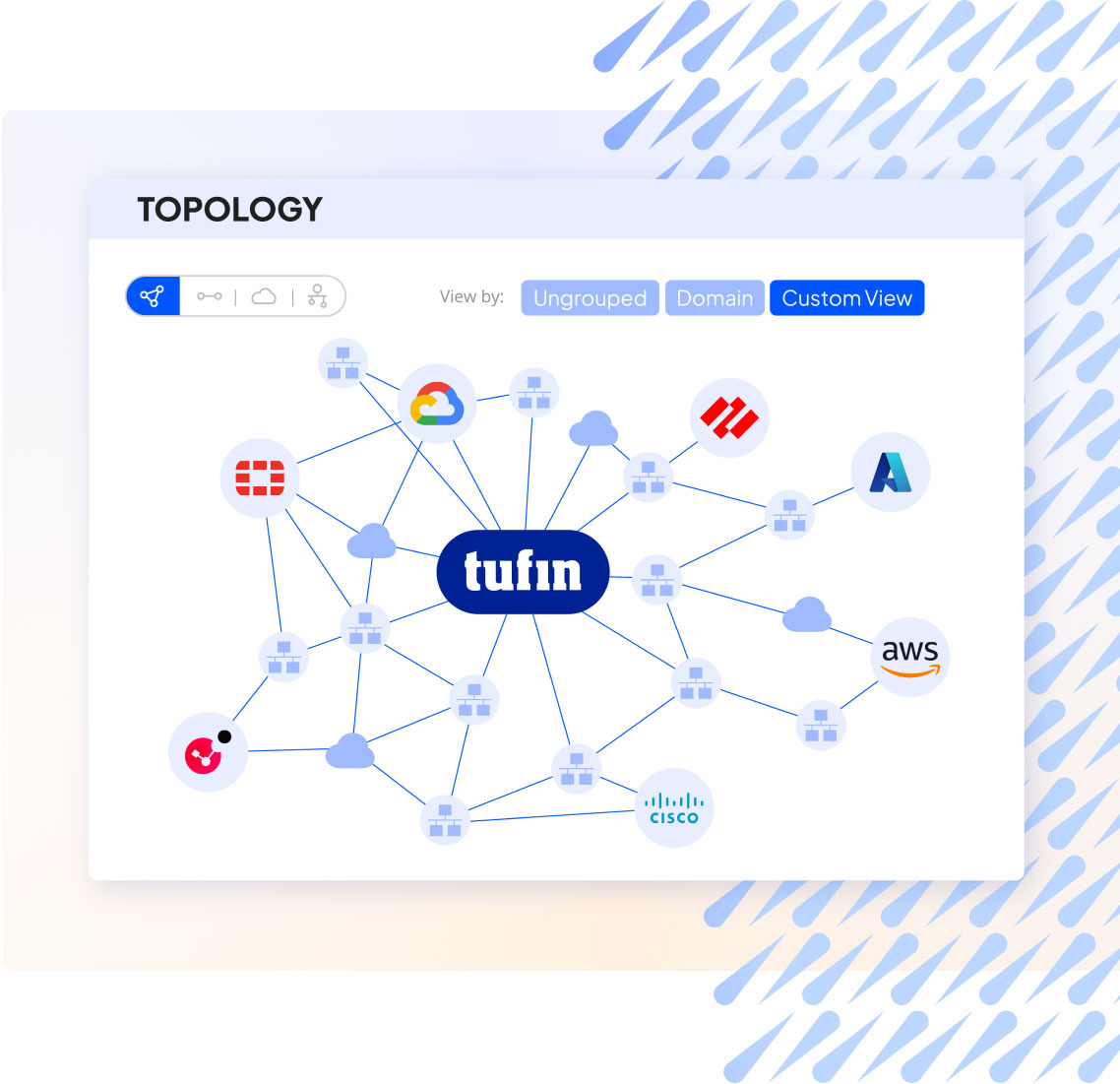
Network Topology Mapper
Gain full visibility into network devices, subnets, nodes, and routers with the Tufin network mapping tool. The interactive map visualizes your entire network across any IT network infrastructure, including cloud-based, hybrid, and on-premises.
Key Features:
- Add generic devices, interfaces, and routes to optimize network visualization.
- Holistic security policy orchestration and automation for all types of networks.
- Intelligent target selection and access change automat
- Real-time display of connectivity and metrics.
- Security policy management across physical network and virtual environments, routers, load balancers, web proxies and apps.
- Rapidly identify, troubleshoot and fix network outages, bottlenecks and dependencies.
- Network topology map syncs IP addresses and subnets daily.
Unmatched Scalability Supporting 10,000+ Devices and 200M+ Routes
The industry’s leading network topology mapper makes Tufin one of the most powerful and accurate network monitoring solutions, providing real-time policy violation alerts and security posture awareness.
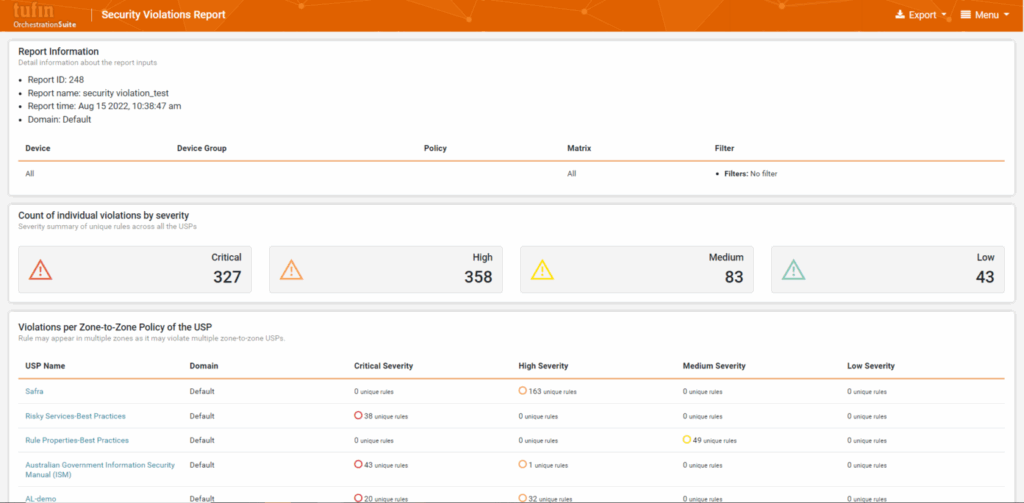
The Best Network Security Policy Monitoring Tool
Compliance monitoring across thousands of network and cloud resources provides real-time risk awareness. Network teams can see risky access and firewall security policy violations in real-time from a central dashboard and receive alerts. The security policy monitoring solutions checks network changes against security/compliance policies, prioritizing violations by criticality.
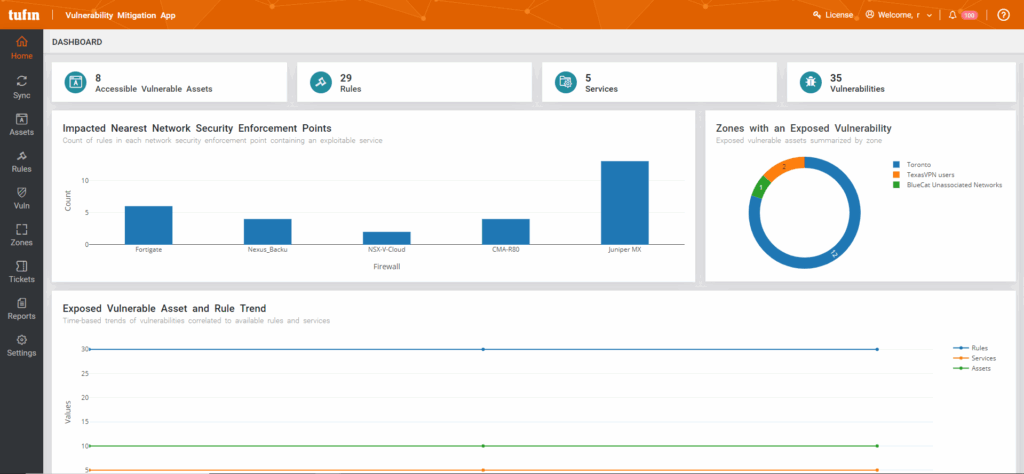
Vulnerability Mitigation
Tufin integrates with your vulnerability management solution, allowing you to correlate network topology intelligence with vulnerability scanning data. This allows you to prioritize patching faster.
Tufin supports several vulnerability scanning providers, including Rapid7, Tenable and more.
Interactive Network Mapping Software
Tufin delivers the best network diagram and topology intelligence powers many of the capabilities that set Tufin apart from the competition. Centralize and automate network management on a single console with market leading accuracy and scalability.
- Highly accurate target selection and visualization of proposed change designs from on-premises to cloud.
- Automate network access changes from request to deployment to optimize efficiency.
- Verification that access was successfully added.
- Path analysis enables investigation of traffic paths for fast troubleshooting to remove bottlenecks.
- Simulating and managing network traffic paths (e.g. managing multi-cloud paths) across IT infrastructure.
- Easily export network maps, templates, and diagrams in multiple formats, including Microsoft Visio.
Tufin Protects the Largest Networks in the World
Gain end-to-end visibility, automate policy management, and mitigate risks across your global hybrid network – from traditional enterprise firewall infrastructure to modern cloud CI/CD pipelines – without impacting speed or agility.
SecureTrack+
Firewall & Security Policy Management
Drive your security policy journey with SecureTrack+
- Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud
- Automate policy optimization
- Prioritize and mitigate vulnerabilities
SecureChange+
Network Security Change Automation
Enhance your visibility and automate mundane tasks with SecureChange+
- Achieve continuous compliance
- Reduce network change SLAs by up to 90% with network change design and rule lifecycle management
- Identify risky attack vectors and detect lateral movement
- Troubleshoot connectivity issues across the hybrid cloud
Enterprise
Zero-Trust Network Security at Scale
Fortify your network security operations with Enterprise
- Achieve zero-touch automation through provisioning of network access changes
- Deploy apps faster through application connectivity management
- Minimize downtime and data loss with High Availability and built-in redundancy
FAQs
Network maps visualize the entire network — IP addresses, subnets, cloud resources — and can identify issues such as excess network traffic or sudden downtime. This network performance monitoring allows IT teams and admins to quickly troubleshoot network issues for maximum security and minimal downtime.
Network visualization allows IT teams to quickly diagnose network issues, easily monitor devices like routers and servers, and plan for infrastructure that will require upgrading. Network visualization also enhances network control and security so network admins can understand new device interactions and identify suspicious nodes and links. This makes it easier to identify unknown devices and other threats across your on-premise and cloud-based environments.
Tufin’s network topology mapper and monitoring tool provides end-to-end network visibility others simply can’t match. It currently supports customers with 10,000+ network devices and more than 200 million routes.
As a network management solution, Tufin enables smooth change management and automates network security policy changes. Tools like SolarWinds Network Topology Mapper (NTM)offer similar key features, but lack the vendor-agnostic network security policy management and automation capabilities across firewalls and security groups that make Tufin such a standout tool.
Yes, Tufin provides seamless integrations with vendors that include Azure, AWS, Direct Connect, Express Route, Virtual WAN, Azure Load Balancers, AWS Gateway Load Balancers, and more.
Tufin is a compatible with the Linux operating system. As well as the Cloud-based platforms mentioned, Tufin provides seamless integrations with vendors such as Cisco, Palo Alto, Fortinet, Checkpoint and more, along with the ability to add new devices, providing detailed network diagrams which cover your entire network.
Get the visibility and control you need to secure your enterprise
Only Tufin provides automation and a unified security policy, from on-prem to cloud, across NetSec and DevOps.
