Network and security teams had to shift the majority of their workforces to remote practically overnight in March. The demand for speed prevented them from following all of their security practices or even leveraging some recently acquired technologies. The existing challenges network teams already faced were (are) compounded with an additional set of obstacles. It is widely agreed that these challenges will not be alleviated anytime soon – the remote workforce is here for the foreseeable future. Organizations surveyed largely agree on short-term solutions for addressing the security gaps created when enabling the remote workforce. In the longer term they are considering a range of options to efficiently make the New Normal secure, and in some cases also taking advantage of the change to elevate the productivity, effectiveness and visibility of their security posture and processes.
Network configuration changes created security gaps – you are not alone
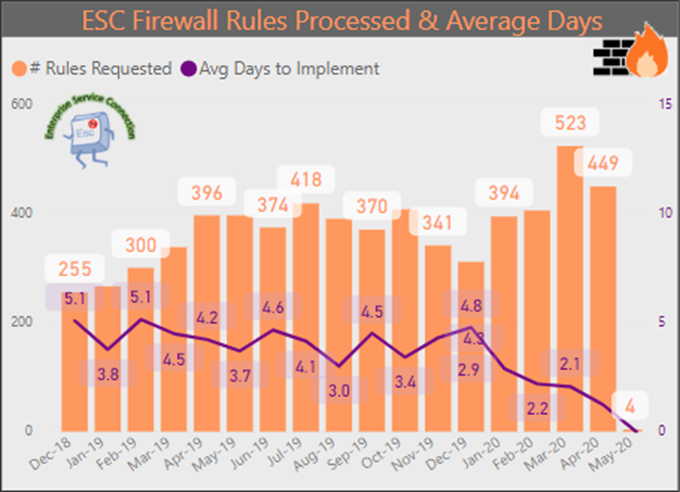
COVID-19 caused a dramatic shift in how companies operate. Based on surveying large organizations, companies had to increase the size of their remote workforce by a factor of 5 to 7 within a few days in early March. One large bank went from 5,000 to 40,000 remote employees. Many service organizations now have over 90% of their workforce working remotely. Network teams had to deal with a dramatic increase in the number of access change requests to accommodate the shift. The Office of the CIO for the State of Michigan saw a 30-50% increase in the number of access change requests in March.
Most IT departments relied on existing, established technologies for enabling remote connectivity. Companies tended to employ their legacy remote VPN solutions, some used remote access VPN solutions offered by their firewall vendors, and in addition many used remote virtual desktop (VDI) technologies for a small portion of their employees. For the most part, organizations kept a single (or small number of) remote access IP pool(s), and treated all IPs in the remote access IP pool (or pools) the same.
By using a small number of remote access IP pools, all connecting remote employees are granted the same internal network access. What was surprising was even organizations that had upgraded to next-generation firewalls (NGFW) did not use them to provide better security and control for remote users connecting via VPN, presumably as the need for speed drove activities. The result is access regardless of a person’s role and “normal” permissions. This leaves security and access control to application-specific user permissions and authentication. This essentially removes segmentation and eliminates zero-trust principles, enabling easy lateral movement within the network for an intruder. This goes against good security practices. To accommodate the changes for the remote workforce security postures have been weakened while attack surfaces have increased.
Risks compounded by increased threat activity
Network security risks have been compounded. Existing risks were enhanced by the growth of the attack surface from the many new entry points, furthered by permissive access. At the same time new cyberthreats have grown. In an attempt to take advantage of general fears of Corona and the change in employee behavior, threat actor activity has increased, especially in the form of phishing attacks. As of May, 2020, according to the Anti-Phishing Working Group (APWG) phishing attacks are at a 3 year high. Verizon’s 2020 Data Breach Investigation reports that phishing is a top threat claiming responsibility for 22% of data breaches. As other means of data breaches are closed, attackers are focusing on the human factor – the weak link in security.
Now – because all remote users have the same network access, lateral movement is not limited. The moment a successful phishing attack takes control over a device which can connect to the office remotely, this device now gives the attacker unlimited lateral movement abilities within the network.
Organizations are finding it is difficult to mitigate the new risks introduced by the network configuration changes. Visibility or knowledge of what changes were provisioned is not necessarily available. Given how the access changes had to be made hastily, the audit trail or documentation processes may have been by-passed. Even with visibility of the changes through a firewall configuration management view or a multi-vendor tool such as Tufin (through the Compare View), if change request workflows were not followed, the owner of the change or reason for the change could still be unknown. As changes may not have been taken through the risk analysis processes, there is a chance they do not adhere to corporate standards. On top of that, many of them were manually conducted, leading to a higher probability of human error and misconfigurations.
What now? Short-term mitigation priorities
To improve the security posture, organizations generally agree the first priority is to identify and assess gaps, and prioritize the risks. The changes that were made quickly need to be reevaluated to reduce risk, prevent audit issues and restore compliance. This involves:
- Gain visibility of the access changes. This includes understanding what changes were made, who requested the change, the purpose for the change, and visibility of what kind of network access remote workers now have. Tufin provides this information for all leading brands of firewalls and routers. Tufin customers can use the Object Change Report for instant visibility by device, security group or timeframe.
- Determine if all access changes were necessary. For higher risk zones or assets, determine if there is a business justification for the access and if the access rules are being used – do they have actual traffic. Tufin customers can use the Rule and Object Usage Report to view hit rates.
- Assess the risk of changes. Map access rules against the organization’s security policy to ascertain impact on compliance. Tufin customers can use SecureTrack risk assessment, permissiveness level checks and rule change validation against the USP.
The goal is to understand the risks and mitigation options.
Once risks are assessed, security policy best practices are recommended, including:
- Rule optimization or clean-up to reduce the attack surface and improve policy health
- Decommission unused or redundant rules that may have been implemented in the haste of enabling the remote worker access, or due to not knowing what access was necessarily really required when the changes needed to be made. Tufin customers can use the Rule and Object Usage Report to view usage levels or hit rates.
- Replace overly permissive rules with more granular rules, where overly permissive is defined as allowing access that is unused. Tufin customers can run an Automated Policy Generation (APG) job on a rule which will watch actual business traffice for a specified amount of time and then suggest a recommended set of rules to reduce the permissiveness of the existing rule.
- Enforce specific controls to specific users to improve containment
- Create basic segmentation using different IP pools for different user roles/groups. Tufin customers can use the Unified Security Policy (USP) or segmentation templates for quick-start-launch.
- Establish least privileged access ensuring that remote users only are granted the access they need.
- Develop a remote access segmentation policy to limit lateral movement
- Apply the same segmentation principles for remote users that is utilized in the on-premise segments.
- Take the highest risk changes through the security evaluation processes
- Ensure the changes that involve sensitive data or your crown jewels go through the risk analysis, verification and approval processes you have defined. Tufin customers can use Tufin SecureChange to simulate the change and conduct impact and risk analysis to confirm alignment with organization’s security policy, either as a stand alone step or as part of the accesss request workflow.
- Apply proper recertification
- Ensure the rules are reevaluated periodically per your security standards. Tufin customers can use the SecureChange rule recertification workflow.
Combined these steps will leverage the core benefits of security policy management to restore your intended security posture and reduce your attack surface.
You never know when you will need to pivot again – longer term considerations
In the longer-term organizations can’t manage their complex, hybrid networks with piecemeal solutions and manual processes and consider themselves a modern, digital enterprise. Organizations aim to establish network security practices that enable agility to support the speed of the business, accelerate collaboration for increased compliance as security responsibilities becomes more distributed, and integrate network insights into their security fabric for improved effectiveness and ROI. Suggestions include:
- Consider adopting a centralized, multi-vendor, multi-cloud security policy orchestration system to provide automated visibility and guardrails for compliance across the entire network.
- Consider moving to more specific granular access technologies, leveraging User Identities with NGFW.
- Consider adopting more modern (cloud-based) remote connectivity solutions.
These will provide solutions that are scalable, as secure as legacy solutions, foster shared visibility to encourage collaboration cross-functions, and don’t require major changes to on-prem infrastructure and security controls to be implemented.
Today, more than ever, organizations have to manage resource shortages, a rapidly changing environment and high levels of uncertainty. In such unique circumstances it becomes critical to have clear, well documented and repeatable processes with minimal manual intervention. By implementing proven, highly-secure practices to accelerate change processes today, your organization will be primed and ready to handle the next crisis.
From the Office of the CIO for the State of Michigan, the orange bars represent the number of access change requests per month, showing a 30-50% increase in March.
Most IT departments relied on existing, established technologies for enabling remote connectivity. Companies tended to employ their legacy remote VPN solutions, some used remote access VPN solutions offered by their firewall vendors, and in addition many used remote virtual desktop (VDI) technologies for a small portion of their employees. For the most part, organizations kept a single (or small number of) remote access IP pool(s), and treated all IPs in the remote access IP pool (or pools) the same.
By using a small number of remote access IP pools, all connecting remote employees are granted the same internal network access. What was surprising was even organizations that had upgraded to next-generation firewalls (NGFW) did not use them to provide better security and control for remote users connecting via VPN, presumably as the need for speed drove activities. The result is access regardless of a person’s role and “normal” permissions. This leaves security and access control to application-specific user permissions and authentication. This essentially removes segmentation and eliminates zero-trust principles, enabling easy lateral movement within the network for an intruder. This goes against good security practices. To accommodate the changes for the remote workforce security postures have been weakened while attack surfaces have increased.
Risks compounded by increased threat activity
Network security risks have been compounded. Existing risks were enhanced by the growth of the attack surface from the many new entry points, furthered by permissive access. At the same time new cyberthreats have grown. In an attempt to take advantage of general fears of Corona and the change in employee behavior, threat actor activity has increased, especially in the form of phishing attacks. As of May, 2020, according to the Anti-Phishing Working Group (APWG) phishing attacks are at a 3 year high. Verizon’s 2020 Data Breach Investigation reports that phishing is a top threat claiming responsibility for 22% of data breaches. As other means of data breaches are closed, attackers are focusing on the human factor – the weak link in security.
Now – because all remote users have the same network access, lateral movement is not limited. The moment a successful phishing attack takes control over a device which can connect to the office remotely, this device now gives the attacker unlimited lateral movement abilities within the network.
Organizations are finding it is difficult to mitigate the new risks introduced by the network configuration changes. Visibility or knowledge of what changes were provisioned is not necessarily available. Given how the access changes had to be made hastily, the audit trail or documentation processes may have been by-passed. Even with visibility of the changes through a firewall configuration management view or a multi-vendor tool such as Tufin (through the Compare View), if change request workflows were not followed, the owner of the change or reason for the change could still be unknown. As changes may not have been taken through the risk analysis processes, there is a chance they do not adhere to corporate standards. On top of that, many of them were manually conducted, leading to a higher probability of human error and misconfigurations.
What now? Short-term mitigation priorities
To improve the security posture, organizations generally agree the first priority is to identify and assess gaps, and prioritize the risks. The changes that were made quickly need to be reevaluated to reduce risk, prevent audit issues and restore compliance. This involves:
- Gain visibility of the access changes. This includes understanding what changes were made, who requested the change, the purpose for the change, and visibility of what kind of network access remote workers now have. Tufin provides this information for all leading brands of firewalls and routers. Tufin customers can use the Object Change Report for instant visibility by device, security group or timeframe.
- Determine if all access changes were necessary. For higher risk zones or assets, determine if there is a business justification for the access and if the access rules are being used – do they have actual traffic. Tufin customers can use the Rule and Object Usage Report to view hit rates.
- Assess the risk of changes. Map access rules against the organization’s security policy to ascertain impact on compliance. Tufin customers can use SecureTrack risk assessment, permissiveness level checks and rule change validation against the USP.
The goal is to understand the risks and mitigation options.
Once risks are assessed, security policy best practices are recommended, including:
- Rule optimization or clean-up to reduce the attack surface and improve policy health
- Decommission unused or redundant rules that may have been implemented in the haste of enabling the remote worker access, or due to not knowing what access was necessarily really required when the changes needed to be made. Tufin customers can use the Rule and Object Usage Report to view usage levels or hit rates.
- Replace overly permissive rules with more granular rules, where overly permissive is defined as allowing access that is unused. Tufin customers can run an Automated Policy Generation (APG) job on a rule which will watch actual business traffice for a specified amount of time and then suggest a recommended set of rules to reduce the permissiveness of the existing rule.
- Enforce specific controls to specific users to improve containment
- Create basic segmentation using different IP pools for different user roles/groups. Tufin customers can use the Unified Security Policy (USP) or segmentation templates for quick-start-launch.
- Establish least privileged access ensuring that remote users only are granted the access they need.
- Develop a remote access segmentation policy to limit lateral movement
- Apply the same segmentation principles for remote users that is utilized in the on-premise segments.
- Take the highest risk changes through the security evaluation processes
- Ensure the changes that involve sensitive data or your crown jewels go through the risk analysis, verification and approval processes you have defined. Tufin customers can use Tufin SecureChange to simulate the change and conduct impact and risk analysis to confirm alignment with organization’s security policy, either as a stand alone step or as part of the accesss request workflow.
- Apply proper recertification
- Ensure the rules are reevaluated periodically per your security standards. Tufin customers can use the SecureChange rule recertification workflow.
Combined these steps will leverage the core benefits of security policy management to restore your intended security posture and reduce your attack surface.
You never know when you will need to pivot again – longer term considerations
In the longer-term organizations can’t manage their complex, hybrid networks with piecemeal solutions and manual processes and consider themselves a modern, digital enterprise. Organizations aim to establish network security practices that enable agility to support the speed of the business, accelerate collaboration for increased compliance as security responsibilities becomes more distributed, and integrate network insights into their security fabric for improved effectiveness and ROI. Suggestions include:
- Consider adopting a centralized, multi-vendor, multi-cloud security policy orchestration system to provide automated visibility and guardrails for compliance across the entire network.
- Consider moving to more specific granular access technologies, leveraging User Identities with NGFW.
- Consider adopting more modern (cloud-based) remote connectivity solutions.
These will provide solutions that are scalable, as secure as legacy solutions, foster shared visibility to encourage collaboration cross-functions, and don’t require major changes to on-prem infrastructure and security controls to be implemented.
Today, more than ever, organizations have to manage resource shortages, a rapidly changing environment and high levels of uncertainty. In such unique circumstances it becomes critical to have clear, well documented and repeatable processes with minimal manual intervention. By implementing proven, highly-secure practices to accelerate change processes today, your organization will be primed and ready to handle the next crisis.
Ready to Learn More
Get a Demo





