SecureChange+
Automate and Control Every Step of the Network Change Process
Manual changes, disconnected approvals, and slow handoffs make network access management one of the biggest operational bottlenecks in security.
Why is SecureChange+ Different?
SecureChange+ automates target device selection, change design, risk analysis, verification, and audit documentation. It eliminates manual effort, reduces risk, and ensures every change is fast, accurate, and fully compliant across hybrid environments.
SecureChange+ includes all SecureTrack+ features, plus the following:
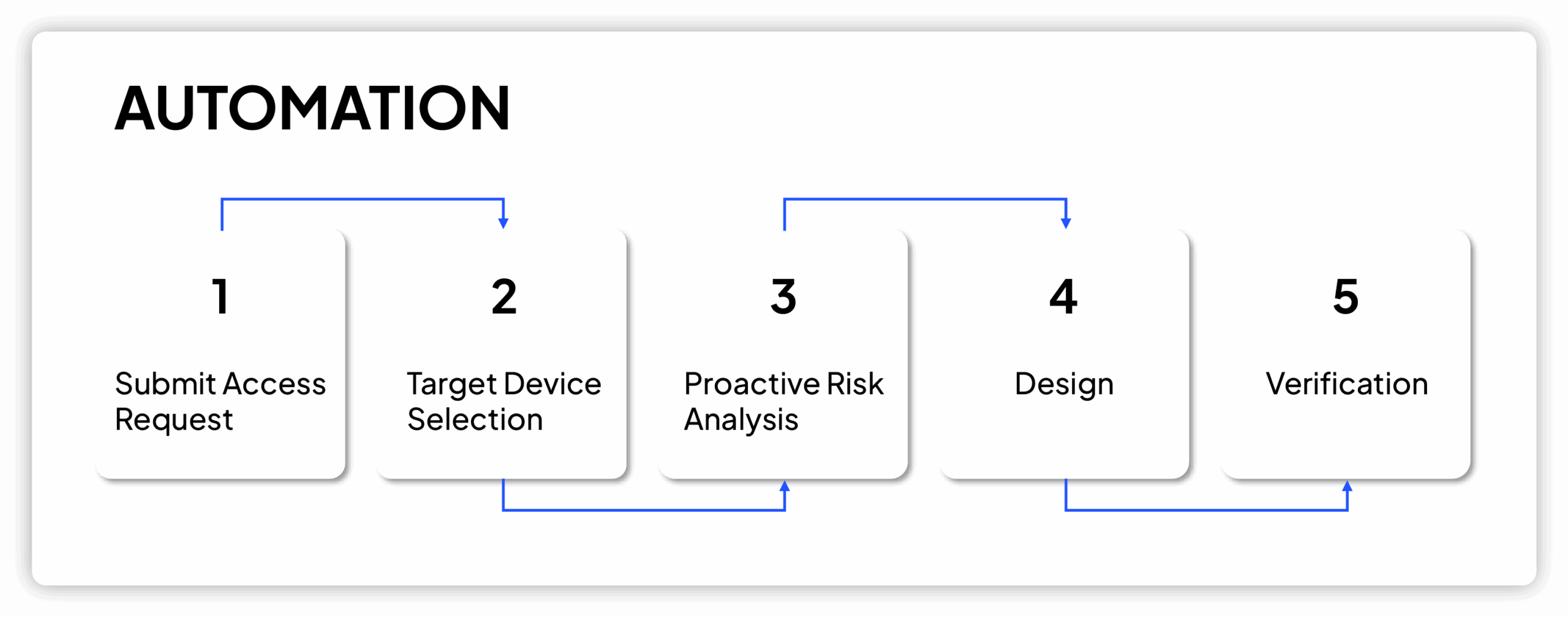
Access Request Workflow
Using the Access Request workflow, you can easily navigate each step of creating and approving network access. With built-in risk analysis, dynamic task routing, and design recommendations, requests move automatically throughout the workflow.
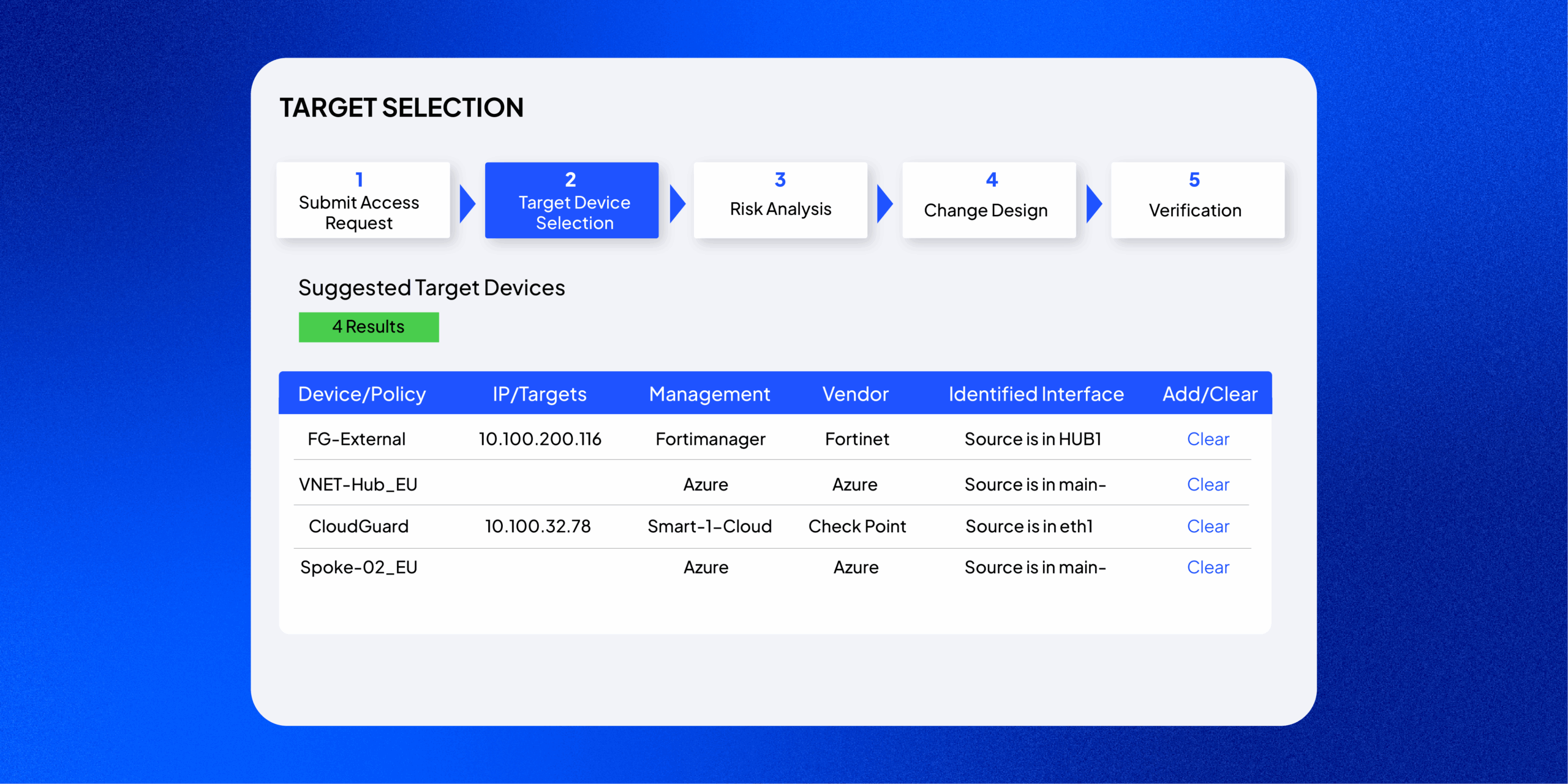
Automated Path Identification & Target Selection
SecureChange+ automatically identifies the optimal network path and target devices for each access request. It uses precise topology and policy data to ensure changes are designed and deployed with accuracy, reducing manual effort and risk across complex environments.
Features:
Automatic Target Suggestion
Leverage topology data to determine which network devices are involved in a traffic path. This streamlines design by eliminating guesswork and ensuring every change request targets the correct devices from the start.
Topology Map
Gain a precise visual view of your network, showing how devices, subnets, and clouds are connected. Trace traffic paths, diagnose broken links, and validate that rule changes align with real-world connectivity.
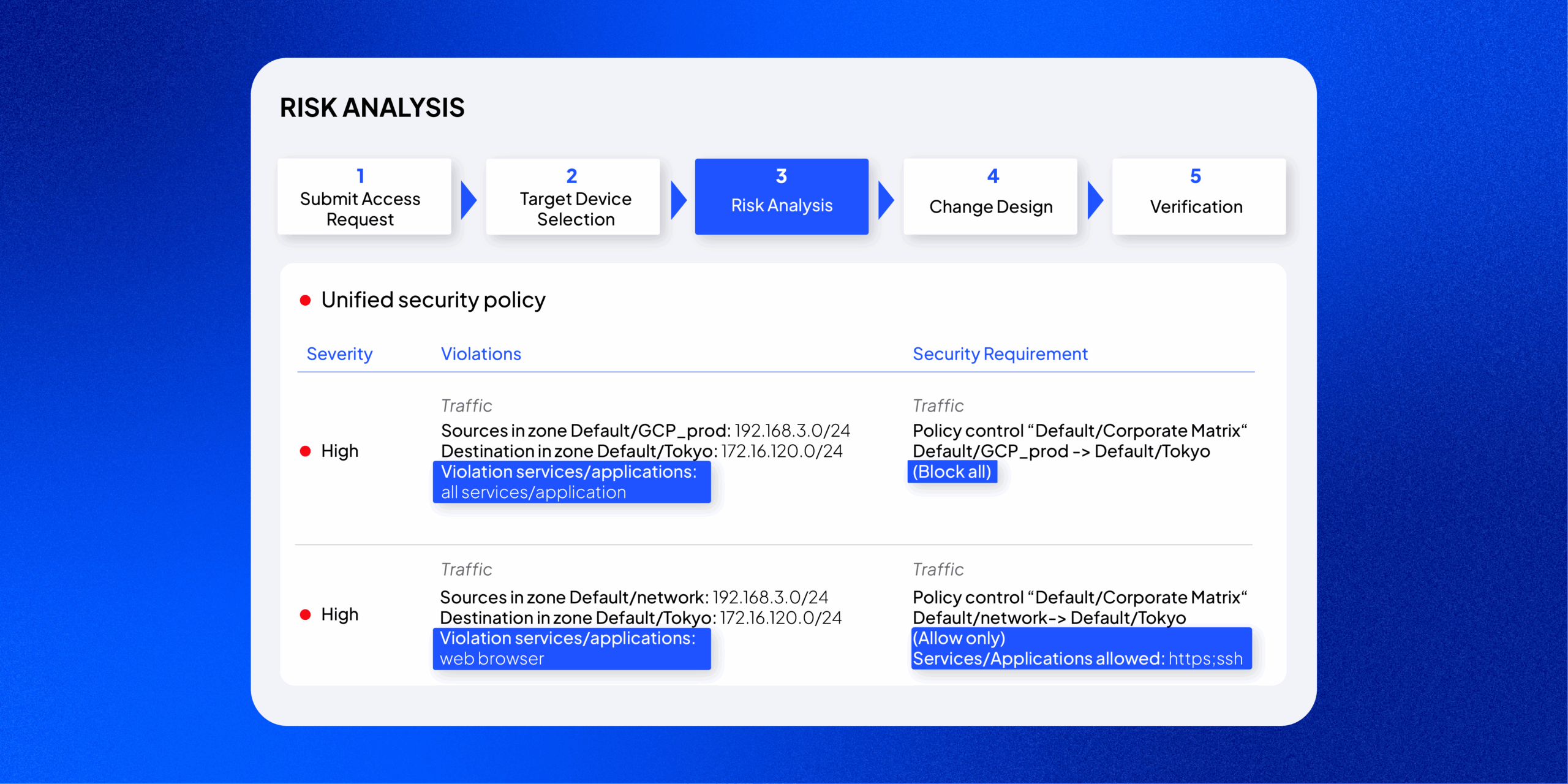
Automated Proactive Risk Assessment
SecureChange+ automatically evaluates the security and compliance impact of every network change before it’s made. It integrates policy intelligence and vulnerability data into the change workflow, helping teams identify risks early and automate approvals for safe, compliant access.
Features:
Risk Analysis
Automatically check each access request against your Unified Security Policy and third-party risk data. It flags compliance violations, calculates exposure, and provides clear options to approve, reject, or adjust requests based on defined thresholds.
Unified Security Policy (USP)
The Unified Security Policy defines allowed traffic between network segmentation zones and continuously measures real-world behavior against it. By mapping change requests to this matrix, SecureChange ensures continuous compliance is enforced across every access decision.
Vulnerability Change Automation (VCA) App
The VCA App integrates SecureChange+ with leading vulnerability scanners to automatically assess the risk of affected assets. It synchronizes scan results, applies severity thresholds, and generates shareable reports that accelerate approval decisions and reduce exposure. Explore Vulnerability-based Change Automation Extension.
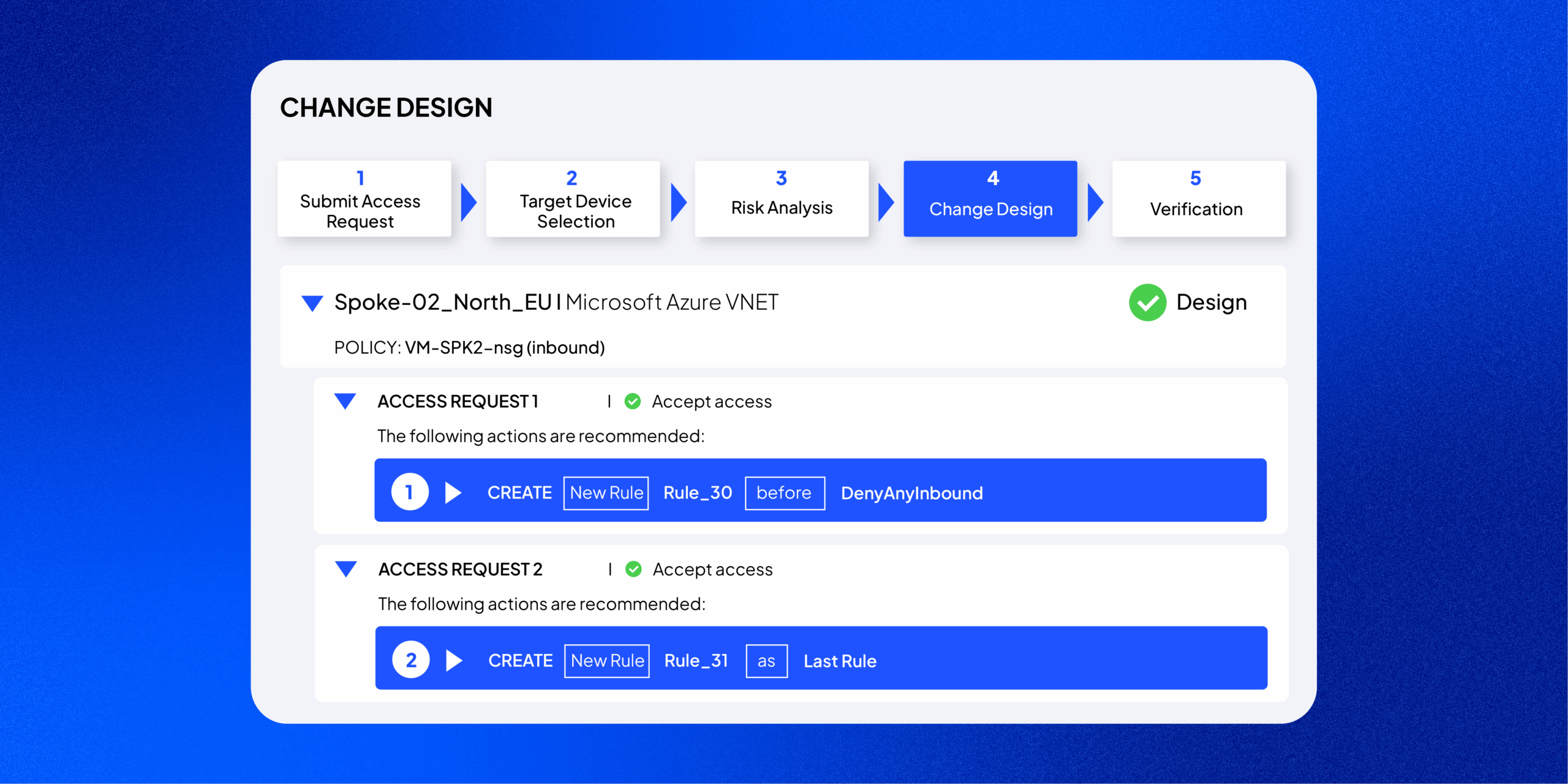
Automated Change Design
SecureChange+ automates the design phase of network change requests. By analyzing topology, security policies, and rulebases, it recommends the updates needed to add or remove access safely and efficiently.
Feature:
Designer
Analyze access requests and leverage suggested rule, object, and policy changes needed to fulfill them. It uses topology and device data to generate accurate, vendor-specific recommendations that can be designed and verified directly within the workflow.
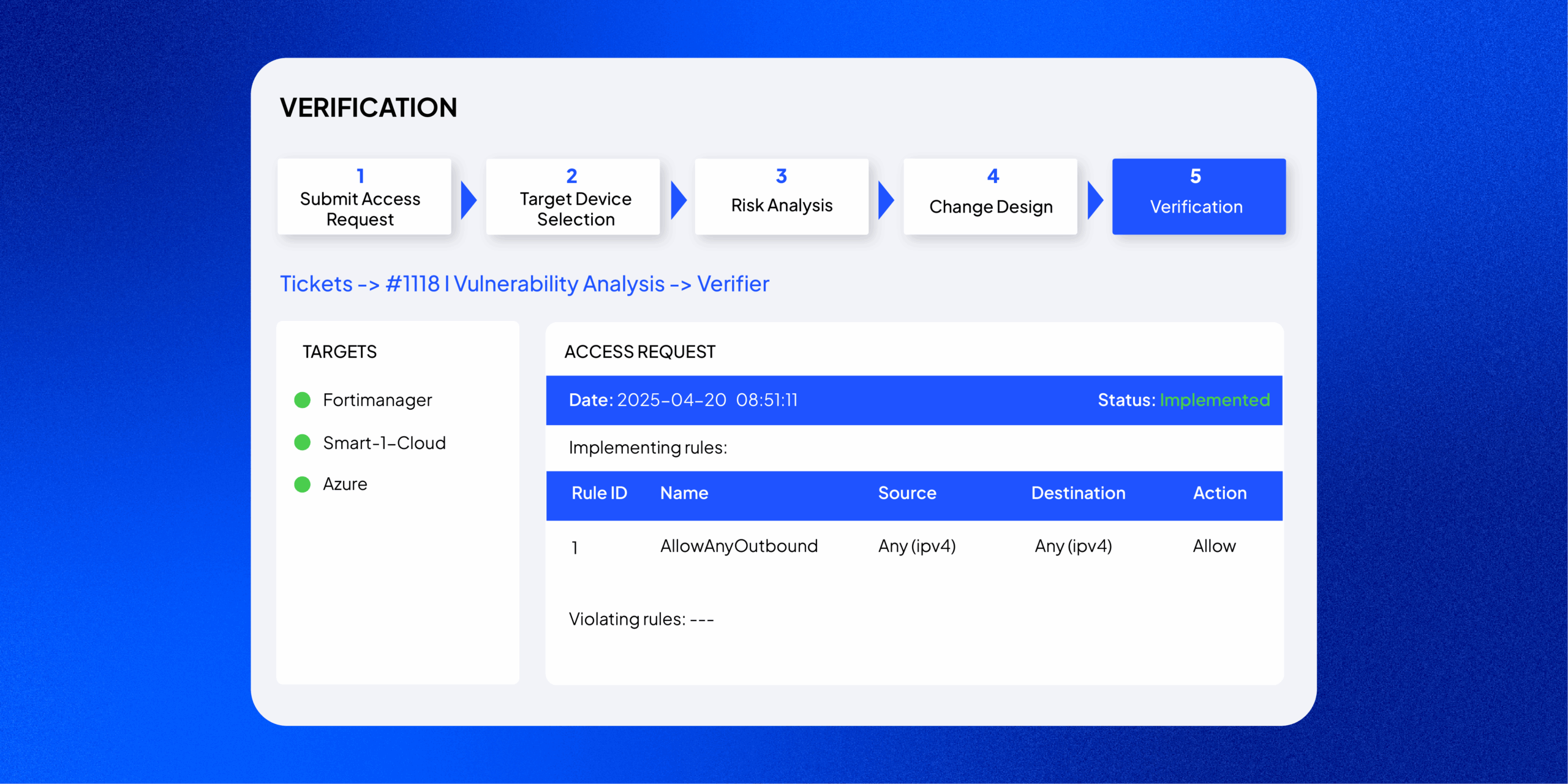
Automated Change Request Verification
SecureChange+ automatically confirms that approved network changes are successfully implemented. It compares live device configurations against approved access requests, ensuring every change is validated, compliant, and fully documented for audit readiness.
Feature:
Verifier
Verify that every implemented change delivers the intended access outcome. The tool automatically tests device policies against approved requests, confirms compliance, and blocks progression until results meet your defined verification criteria.
Network Mapping & Visualization
SecureChange+ brings full visibility into your network environment.
By mapping devices, subnets, and connectivity, it helps teams visualize dependencies, validate change impact, and maintain accurate topology for automated design and risk assessment.
Features:
Topology Map
Gain a visual view of your network, showing how devices, subnets, and clouds are connected. Trace traffic paths, diagnose broken links, and validate that rule changes align with real-world connectivity.
TOS Discovery
Discover unmanaged devices and keep your topology up to date automatically. TOS Discovery identifies routers and switches not yet monitored, imports them into Tufin, and streamlines maintenance through scalable grouping and automated onboarding.
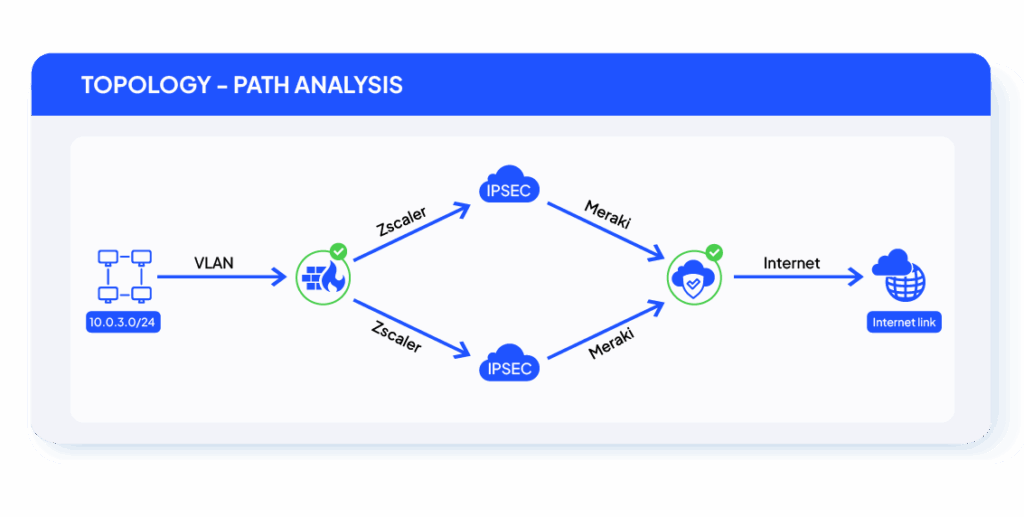
Network Path Analysis & Troubleshooting
SecureChange+ helps teams quickly trace traffic paths and diagnose connectivity issues across hybrid environments. It visualizes how traffic moves through the network, identifies where it’s being blocked, and provides the insights needed to resolve access problems fast.
Features:
Path Analysis Queries
Run path analysis queries to instantly see how traffic flows between selected sources and destinations. Identify the devices, routes, and rules that affect connectivity, detect blocking points, and export detailed reports to support troubleshooting and compliance.
TufinMate for IT
Use natural language to analyze paths, check access, and generate topology reports. TufinMate for IT, powered by TufinAI, helps teams validate connectivity, view devices on a path, and even open network change tickets directly from the chat, simplifying troubleshooting and change initiation.
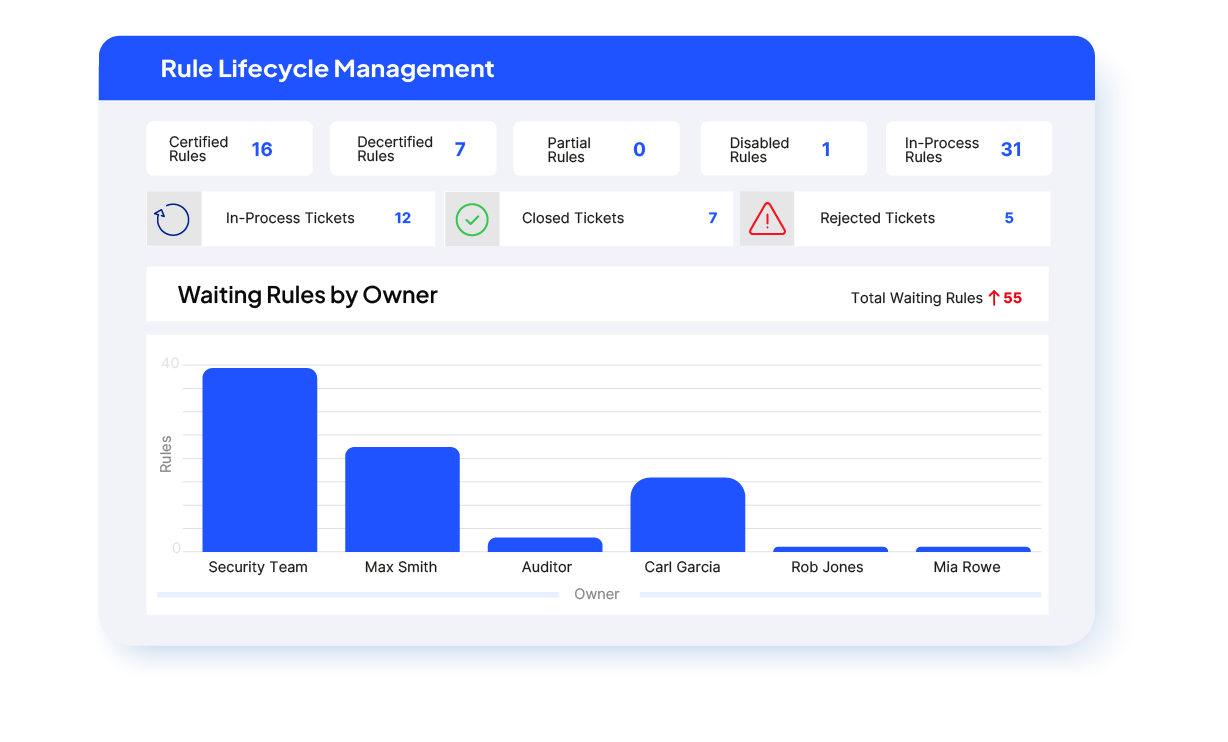
Rule Lifecycle Management
SecureChange+ automates every stage of rule governance, from creation to recertification and removal. It ensures that only valid, necessary rules remain active by orchestrating reviews, ownership decisions, and decommission workflows across your network.
Features:
Rule Lifecycle Management App
Automate rule recertification and eliminate manual tracking. The Rule Lifecycle Management App identifies expiring or unused rules, assigns them to owners for review, and opens SecureChange tickets to certify, modify, or remove them based on their status.
Rule Modification Workflow
Easily update existing firewall rules without disrupting security or compliance. The workflow automates approval and documentation so every change to sources, destinations, or services is accurate, traceable, and audit-ready.
Rule Decommissioning Workflow
Streamline the process of disabling outdated or decertified rules. When a rule is marked for removal, SecureChange automatically opens a decommission ticket, runs Designer and Verifier to confirm the change, and tracks progress.
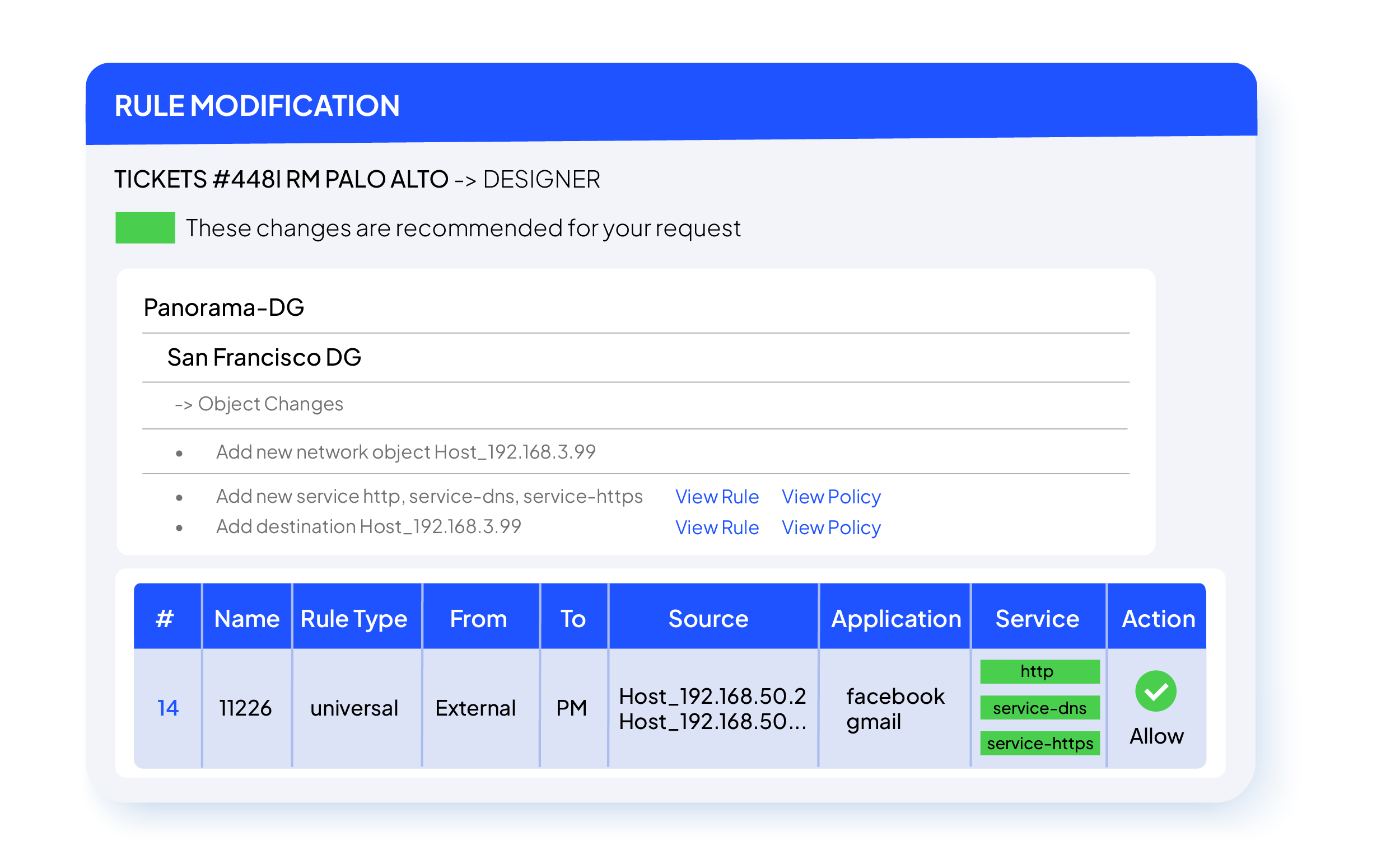
Rule and Group Management
SecureChange+ streamlines the process of modifying firewall rules and network groups through structured, automated workflows. It allows teams to safely design rule and network group changes across supported devices.
Features:
Modify Group Workflow
Create or adjust network object groups directly through guided workflows. Teams can safely add, remove, or update group members with built-in validation and approval steps that keep device configurations consistent and error-free.
Rule Modification Workflow
Easily update existing firewall rules without disrupting security or compliance. The workflow automates approval, and documentation, so every change to sources, destinations, or services is accurate, traceable, and audit-ready.
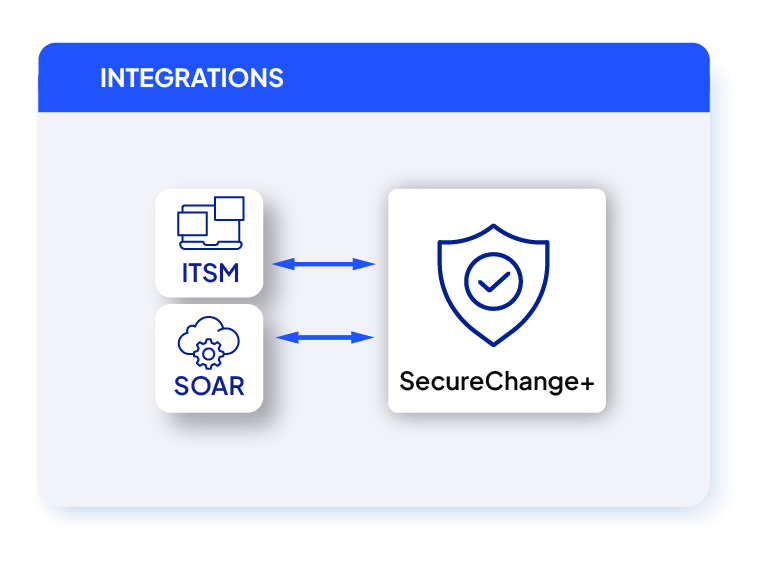
ITSM-Led Change Process
SecureChange+ connects network security automation with your ITSM system for a unified, audit-ready change process. It keeps security, operations, and compliance workflows in sync by exchanging updates, tickets, and results automatically across platforms.
Feature:
Workflow Integrator
Integrate SecureChange+ with your ITSM platform to automate ticket updates, approvals, and status tracking. The Workflow Integrator App synchronizes ticket data, tool outputs, and custom fields across systems using REST APIs, removing manual steps and ensuring full process visibility.
Transforming Network Security & Automation
Elevate your network security and cloud security operations with Tufin’s product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.
SecureTrack+
Firewall & Security Policy Management
Drive your security policy journey with SecureTrack+
- Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud
- Automate policy optimization
- Prioritize and mitigate vulnerabilities
SecureChange+
Network Security Change Automation
Enhance your visibility and automate mundane tasks with SecureChange+
- Achieve continuous compliance
- Reduce network change SLAs by up to 90% with network change design and rule lifecycle management
- Identify risky attack vectors and detect lateral movement
- Troubleshoot connectivity issues across the hybrid cloud
Enterprise
Zero-Trust Network Security at Scale
Fortify your network security operations with Enterprise
- Achieve zero-touch automation through provisioning of network access changes
- Deploy apps faster through application connectivity management
- Minimize downtime and data loss with High Availability and built-in redundancy
Why Choose Tufin? Let Us Show You.
Schedule a demo and see for yourself.




