Cisco recently cautioned about a security weaknesses on some versions of IOS and IOS XE-based routers, switches and appliances. The risk is related to a certain type of password (Type 4) that could allow an authenticated remote attacker to access sensitive information on a targeted device.
Cisco recommends to check whether such passwords exist on your Cisco devices and to replace them with Type 5 passwords.
While Cisco has provided a method to test devices for existence of these problematic passwords, you may still want a way to ensure that such passwords are not introduced anytime in the future.
Here’s a custom device configuration test that we developed to identify any Type 4 passwords across your router inventory and also to alert if such a password is mistakenly configured in the future.
Assuming your routers are defined in SecureTrack, follow these instructions to test them:
Add the custom test by running this command on the SecureTrack server:
curl -k -u <user>:<password> -X POST -d '<dcr_test_concrete><groupId>8</groupId><id/><name>Forbid Type 4 Passwords</name><isActive>true</isActive><isDefault>true</isDefault><risk>3</risk><severity>3</severity><testDef><description>Verify that Type 4 passwords are not configured.</description><expression>^(enable secret 4|username.*secret.4)[^n]*</expression><id/><input>running_config</input><isCustom>true</isCustom><mustContain>false</mustContain><name>Forbid Type 4 Passwords</name><products><device>IOS</device><id>1</id><vendor>Cisco</vendor></products><remediation>Replace Type 4 passwords with Type 5 passwords.</remediation><testDefUid>CU001</testDefUid><type>line_match</type></testDef><testUid>CU001</testUid></dcr_test_concrete>' -H "Content-Type:application/xml" "http://localhost:8080/securetrack/api/dcrTests/custom"Create a new device configuration report under Reports
Enable the new custom test: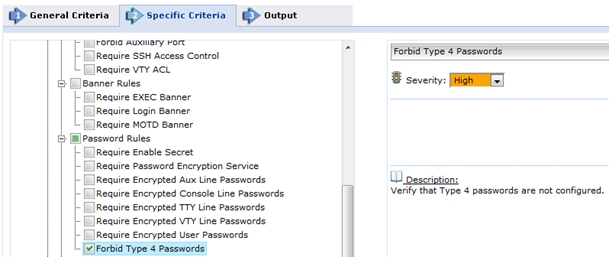
Save and run the report
A properly configured device should pass the test like this: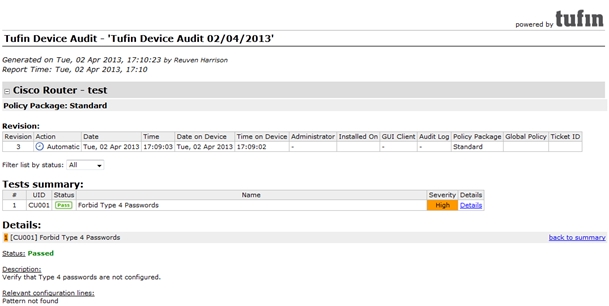
Ready to Learn More
Get a Demo





