Firewall Migration
Enhance network security by automating time-consuming manual tasks, reducing misconfiguration errors in firewall rules, access control, firewall policy, and endpoint management.
Firewall Migration Use Cases
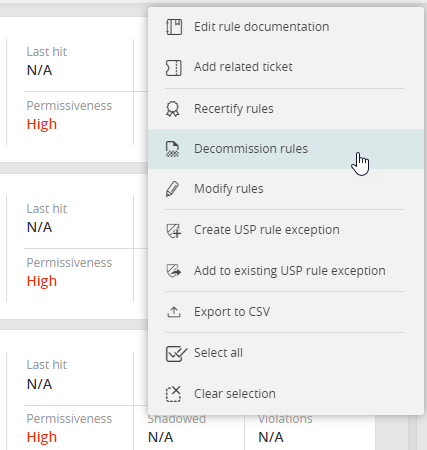
Standardize Rules Across All Vendors
Implement vendor-agnostic security policies to mitigate risks related to translating vendor topology and naming conventions.
- Create Unified Security Policies (USPs) that compare what rules are configured against compliance standards.
- Automate the decommissioning of overly permissive access rules and objects before migration.
- Accurately configure devices and technologies with rule modification and group modification to reduce vulnerability- and misconfiguration-related risks.
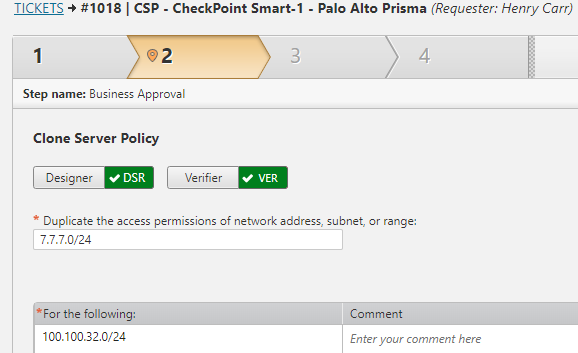
Reduce Time-Consuming, Manual Processes
Automate the cloning and provisioning of static routes and web application policies using a firewall migration tool, enabling faster project completion, reducing reliance on professional services, and ensuring a successful migration with minimized human error risks in firewall management.
- Clone existing servers to migrate rules faster while maintaining consistency.
- Automatically provision policies and changes across all vendors to save time on change management and employee training.
- Use workflows that review risk to ensure changes are implemented accurately.
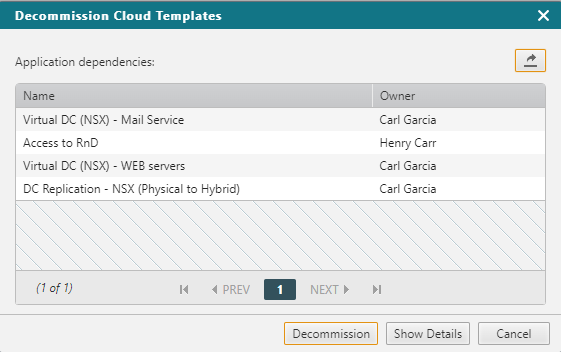
Maintain Application Availability
Minimize business disruption and migration costs by maintaining visibility and control over firewall configuration and application connectivity changes, ensuring high availability and seamless functionality with the new firewall’s access control settings.
- Streamline application owner and network administrator collaboration with a central console for all network-related application connectivity changes.
- Improve business application availability with faster misconfiguration troubleshooting and root cause investigation.
- Automate processes for defining, implementing, and decommissioning application connectivity.
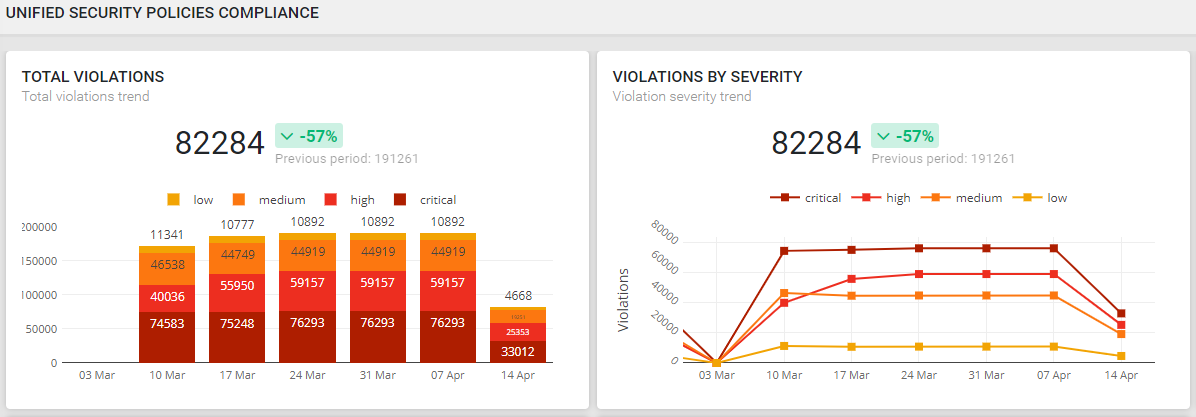
Automate Risk and Compliance Monitoring
Protect against policy change violations and streamline your firewall migrations.
- Use pre-defined regulatory compliance templates to build security policies faster.
- Leverage workflows that automatically detect and review network changes for compliance.
- Receive alerts that identify critical security policy violations to effectively fix or exempt changes that impact security.
Get Started with Tufin
Contact our experts to learn more about pricing, receive a free network and firewall risk assessment, or schedule a demo.
Additional Resources
Learn more about how Tufin streamlines firewall migration processes through automation.
Transforming Network Security & Automation
Elevate your network security and cloud security operations with Tufin’s product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.
SecureTrack+
Firewall & Security Policy Management
Drive your security policy journey with SecureTrack+
- Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud
- Automate policy optimization
- Prioritize and mitigate vulnerabilities
SecureChange+
Network Security Change Automation
Enhance your visibility and automate mundane tasks with SecureChange+
- Achieve continuous compliance
- Reduce network change SLAs by up to 90% with network change design and rule lifecycle management
- Identify risky attack vectors and detect lateral movement
- Troubleshoot connectivity issues across the hybrid cloud
Enterprise
Zero-Trust Network Security at Scale
Fortify your network security operations with Enterprise
- Achieve zero-touch automation through provisioning of network access changes
- Deploy apps faster through application connectivity management
- Minimize downtime and data loss with High Availability and built-in redundancy



