Reduce manual effort and minimize the risk of human error by integrating with ITSM platforms and providing real-time change tracking.
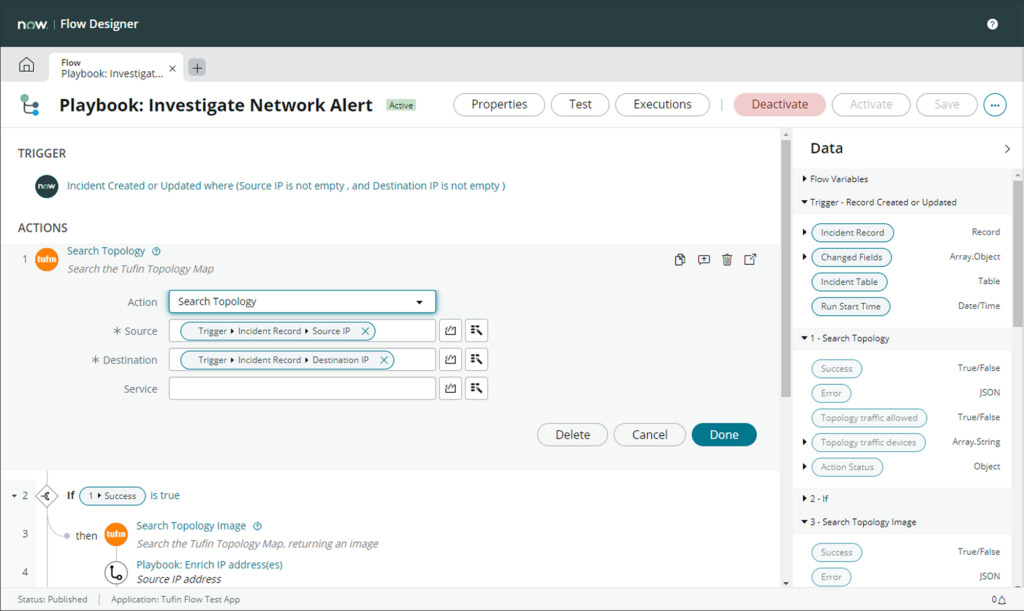
Ensure continuous adherence to regulatory standards and internal policies through automated compliance checks and reporting, reducing the risk of non-compliance and facilitating easier audits.

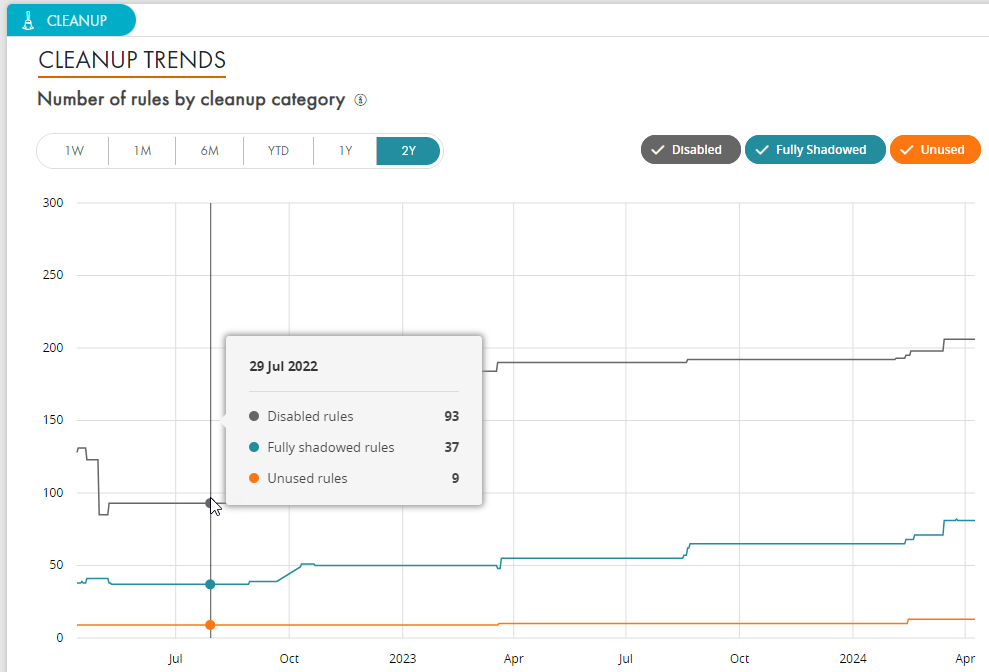
Automatically identify and correct overly permissive, redundant, or shadowed rules and automate the recertification process to detect expired rules and generate cleanup routing and reporting.
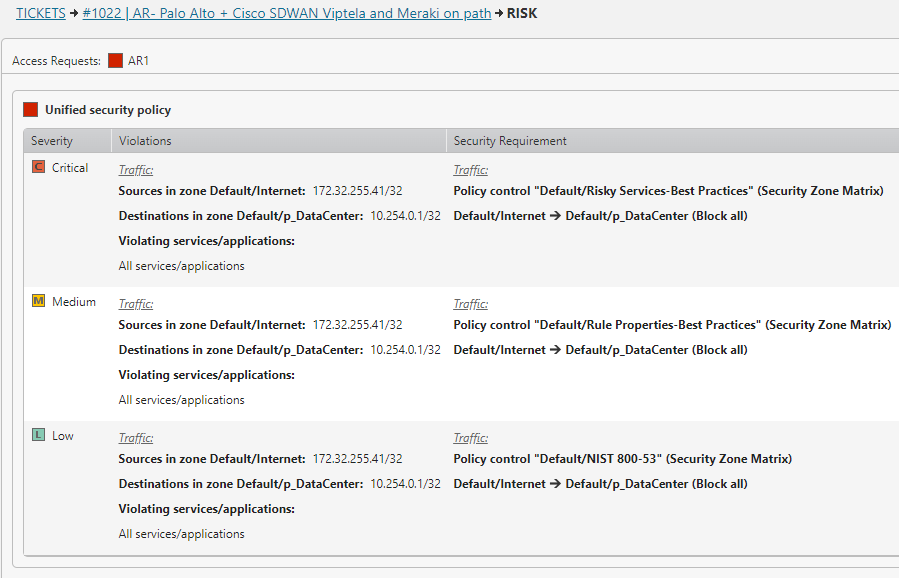
Proactively identify and address potential security risks and compliance issues before implementing network changes with process automation.
Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.