Faster Vulnerability Prioritization and Automating Vulnerability Management
Tufin helps vulnerability teams prioritize patching faster and automates vulnerability-aware network access changes.
Prioritize Remediation and Enhance Risk-Based Vulnerability Management
With Tufin’s network intelligence, security administrators have the context they need to identify and focus on the vulnerabilities that pose the greatest threat to critical business assets.
Block access to vulnerable systems from the Tufin dashboard until remediation is possible.
- Tufin integrates with major vulnerability scanners.
- Correlate vulnerability scanning data with Tufin’s network connectivity intelligence to triage faster.
- Automate vulnerability-aware network access changes to avoid exposure.
Enrich Vulnerability Data with Internal Network Intelligence
Security teams rely on vulnerability scanners to provide valuable data on known vulnerabilities in their networks. Acting upon that data, however, can often be challenging because of manual processes and missing contextual information.
Common Vulnerability Scoring Systems (CVSS) can help direct remediation efforts, but they don’t tell the whole story. Tufin combines CVSS risk scores and other vulnerability assessment measurements with network connectivity insights to effectively prioritize remediation and mitigation efforts.
These insights help organizations understand how vulnerabilities could be accessed and exploited in the network, providing the critical context needed to focus on the most potentially dangerous vulnerabilities first.
The vulnerability mitigation dashboard displays the rules that govern access to and from assets, underlying services that can expose the vulnerability, relevant firewalls that provide access, and tracks trends to see how your efforts are impacting your total attack surface.
Consolidate Multi-Vendor Data Into a Single Dashboard
Tufin collects data from all your vulnerability scan results—even across multiple multivendor solutions—and displays them in a single vulnerability dashboard where security professionals can quickly and easily identify the highest-risk vulnerabilities in the highest-value network segments. It’s an ideal tool for large organizations and managed security services providers (MSSPs) that need to improve their vulnerability management process.
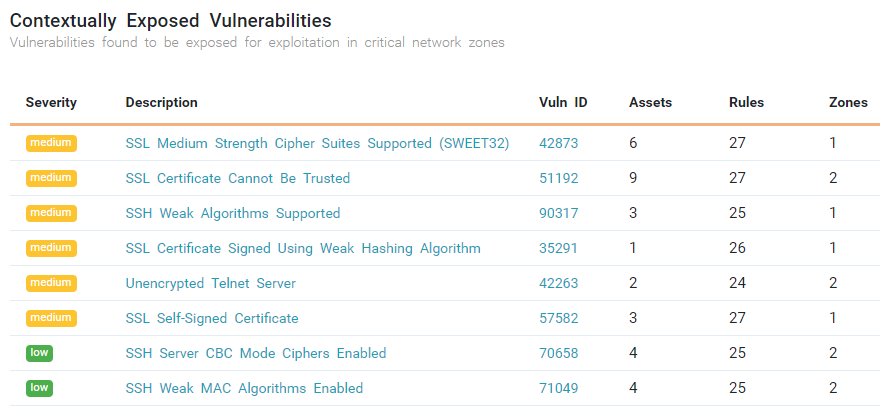
Prevent Cyber Risk Exposure
Tufin’s Vulnerability-Based Change Automation (VCA) application scans for vulnerabilities before you create new cybersecurity rules or provision new access, automatically, to ensure that rules and assets are safe before they’re implemented in the network. VCA integrates with the leading vulnerability management solutions (including Nessus, Qualys, Rapid7, and Tenable) and takes that data to create risk assessments for access request workflows.

Automate Review of Connectivity Requests
IT teams are often inundated with new connectivity requests. Tufin’s vulnerability management tools allow administrators to automatically assess whether new requests will grant access to assets with known security vulnerabilities and either resolve the vulnerability or deny the request.

Mitigate Vulnerabilities When Remediation Isn’t An Option
Vulnerability scans often yield too many vulnerabilities for security teams to address and patch. With Tufin VMA, security teams can effectively focus remediation efforts on the most critical vulnerabilities and mitigate the rest automatically by blocking access to critical assets until patch management can be undertaken.
FAQs
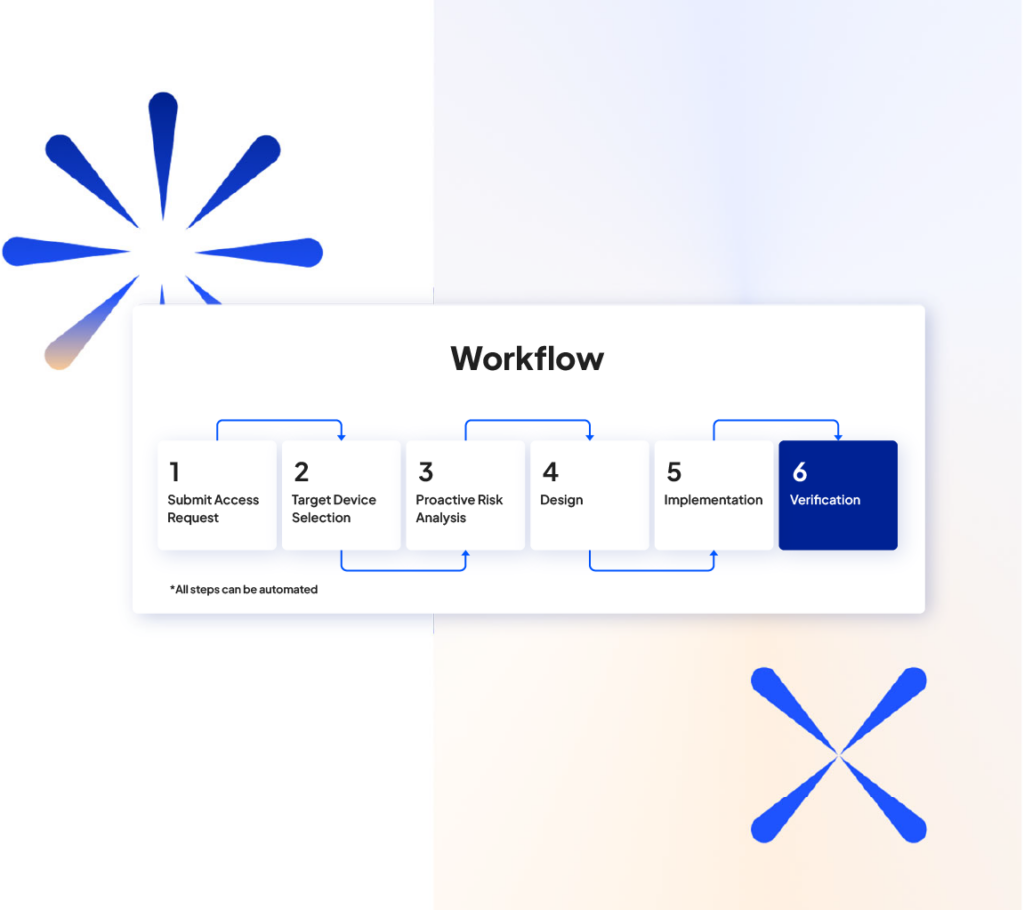
Using Tufin’s VMA, security administrators can remove all network access associated with vulnerable assets through Tufin’s pre-configured server decommissioning workflow, an automated process initiated directly from the app. Tufin SecureChange then streamlines the network change implementation process to locate and update all rules, enabling access to vulnerable assets in all relevant network security devices and infrastructure components including firewalls, SDNs, routers, and security groups.
The necessary rule changes are designed and implemented automatically, removing access to the vulnerable asset and instantly improving your security posture. Tufin then validates that the change has been implemented as intended. This fully automated and tracked process can be managed directly from the app or integrated with your ITSM solution workflows.
Transforming Network Security & Automation
Elevate your network security and cloud security operations with Tufin’s product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.
SecureTrack+
Firewall & Security Policy Management
Drive your security policy journey with SecureTrack+
- Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud
- Automate policy optimization
- Prioritize and mitigate vulnerabilities
SecureChange+
Network Security Change Automation
Enhance your visibility and automate mundane tasks with SecureChange+
- Achieve continuous compliance
- Reduce network change SLAs by up to 90% with network change design and rule lifecycle management
- Identify risky attack vectors and detect lateral movement
- Troubleshoot connectivity issues across the hybrid cloud
Enterprise
Zero-Trust Network Security at Scale
Fortify your network security operations with Enterprise
- Achieve zero-touch automation through provisioning of network access changes
- Deploy apps faster through application connectivity management
- Minimize downtime and data loss with High Availability and built-in redundancy
Get the visibility and control you need to secure your enterprise
Only Tufin provides automation and a unified security policy, from on-prem to cloud, across NetSec and DevOps.
