SecureTrack+
Simplify Network Security Policy Management Across Hybrid Environments
Frequent changes, sprawling devices, and fragmented teams have turned policy management into one of the most resource-draining parts of network security.
SecureTrack+ centralizes network security policy management across hybrid environments.
Why is SecureTrack+ Different?
SecureTrack+ keeps policies consistent, makes every change accountable, ensures continuous compliance, and drives ongoing optimization to reduce risk and simplify operations.
Centralized Security Policy Visibility
SecureTrack+ centralizes oversight of every device, rule, and object in your network. With unified views and tools to drill into policies, it simplifies troubleshooting, ensures accuracy, and makes policy management more efficient.
Features:
SecureTrack Dashboard
A visual dashboard with widgets that summarize key compliance, audit, and rule insights across your network. It highlights cleanup candidates, critical violations, and recent changes, with drill-down shortcuts to detailed rule and device data.
Device Management
A single dashboard provides oversight of every device, policy, and recent changes across the network. It surfaces compliance issues and highlights unused or expired rules so nothing slips through the cracks.
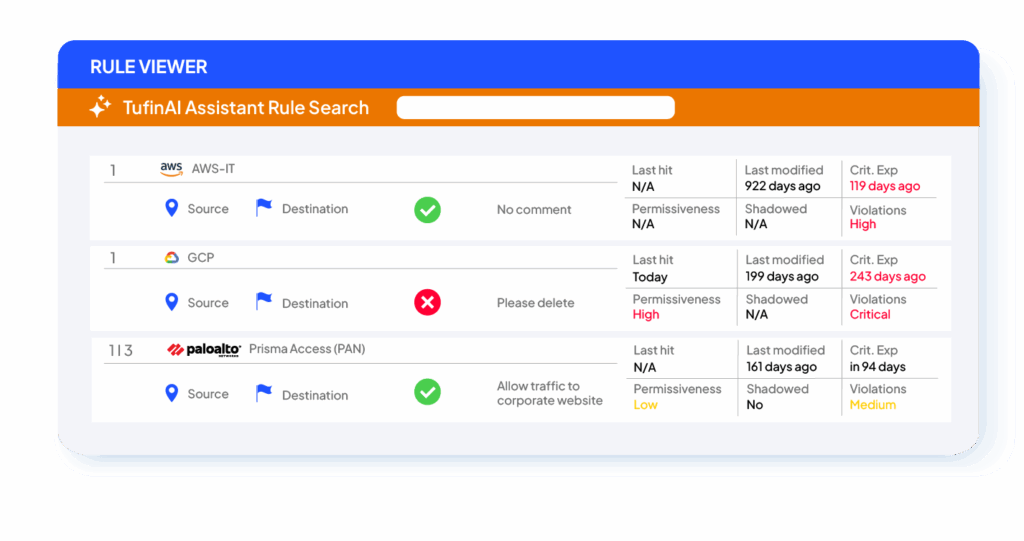
Rule Viewer
View and filter all policy rules across devices in one place. Track documentation, violations, and rule lifecycle actions like recertification, decommissioning, or modification. Now you can also search rules in plain language with TufinAI Rule Search, making it faster to find what you need.
Object Lookup
Search for objects across devices to confirm accuracy of names, IPs, and usage. Instantly see which rules and groups reference an object, helping to prevent misconfigurations and policy conflicts.
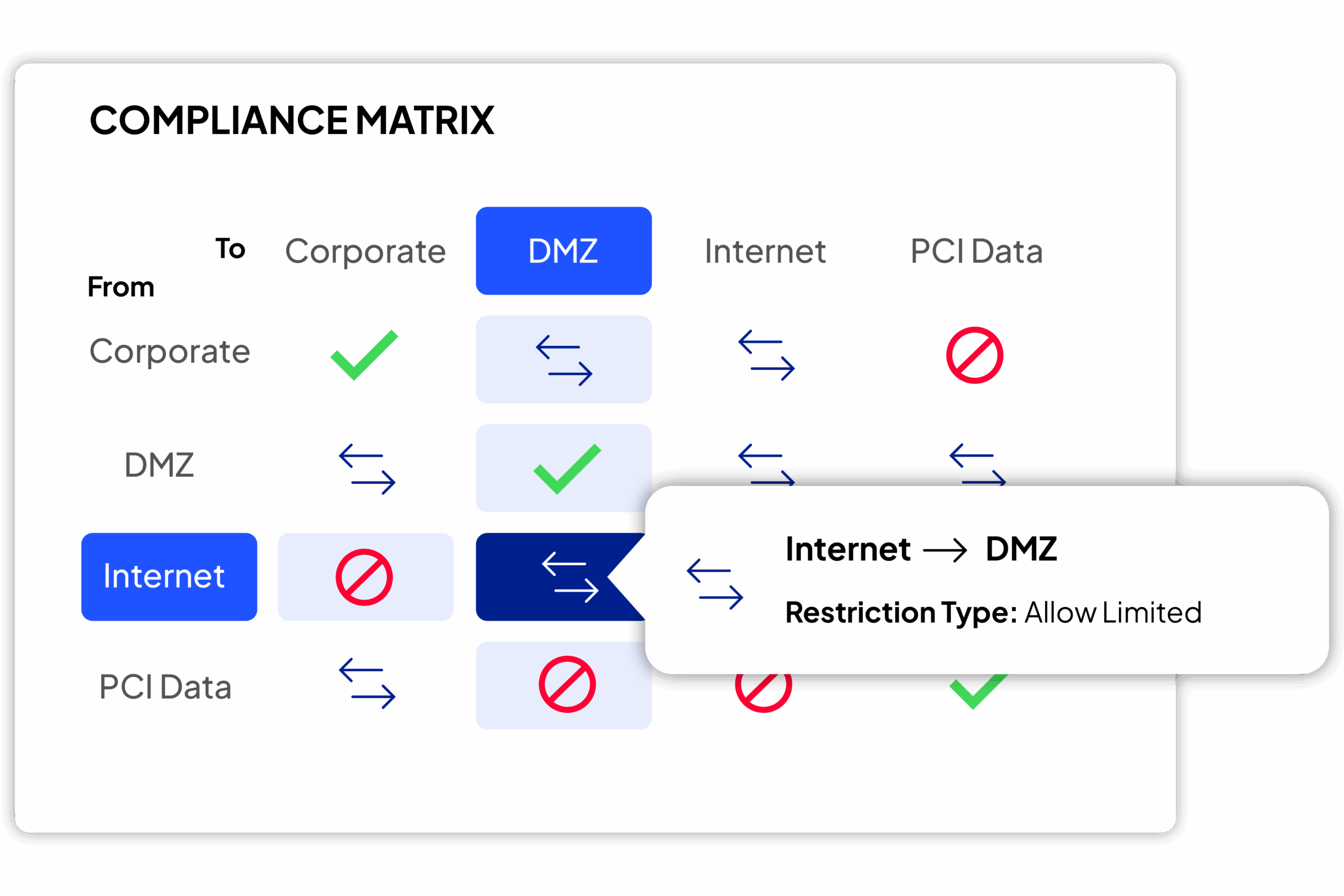
Network Segmentation, Compliance & Audit
SecureTrack+ helps enforce segmentation and compliance by defining clear zone boundaries and continuously checking real-world traffic against your policies. Dashboards and extensions add depth, making it easier to automate policy building, sync with IPAMs, and provide audit-ready proof of compliance.
Features:
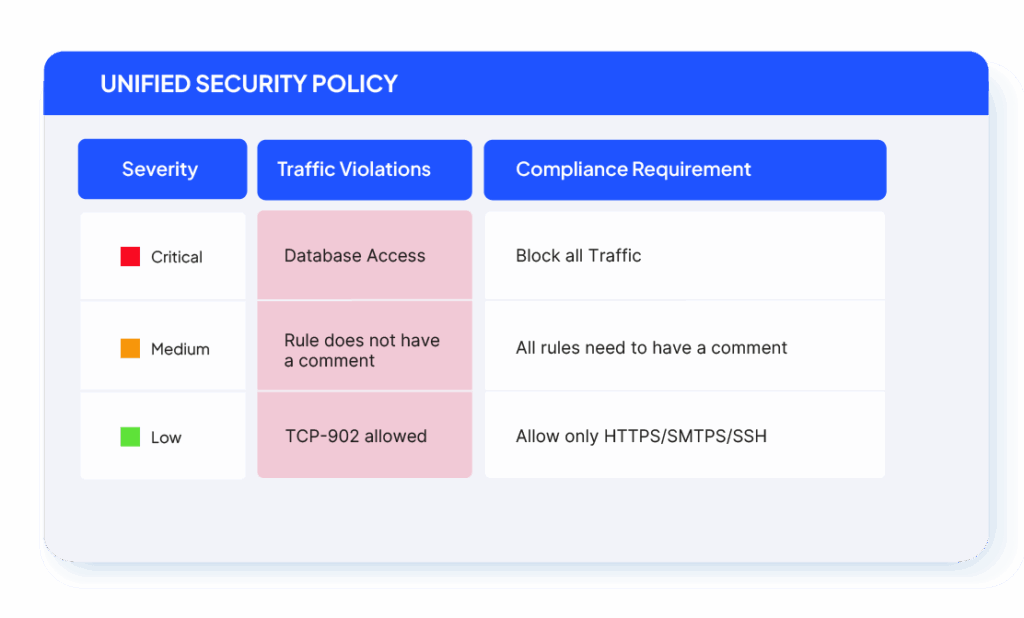
Unified Security Policy (USP) and Zones
Define segmentation zones across all devices, then manage how traffic flows between them through a central policy matrix. SecureTrack continuously measures live network behavior against this framework, flagging violations, managing exceptions, and ensuring compliance with both corporate and regulatory standards.
Advanced Reporting
Advanced Reporting delivers a complete view of security posture and compliance across your network. It automatically evaluates device configurations, policy violations, and adherence to best practices to help teams strengthen controls, close gaps, and stay audit-ready.
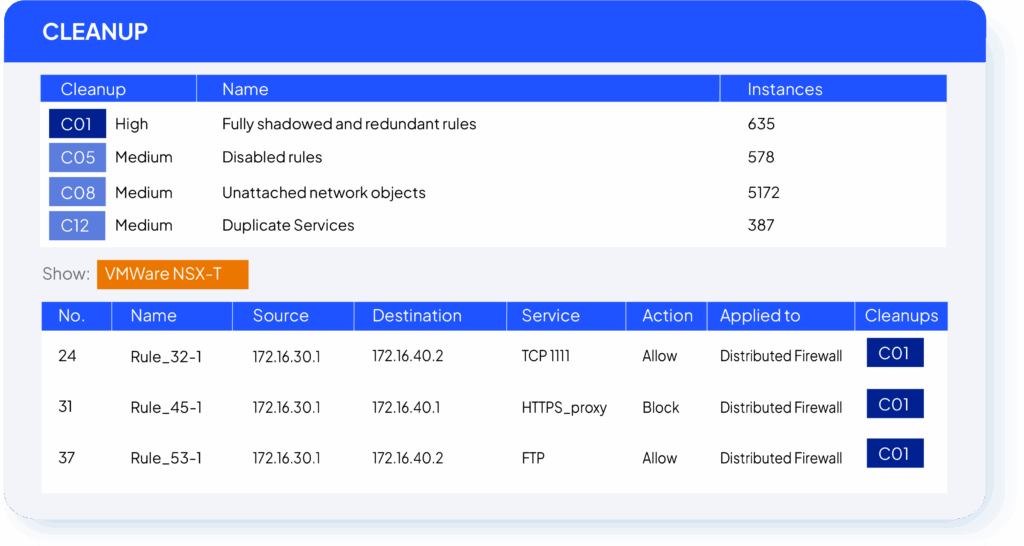
Security Policy Cleanup
Over time, policies accumulate outdated servers, unused rules, and duplicate objects that add risk and complexity. SecureTrack+ makes it simple to find and remove this clutter so your security posture stays clean, efficient, and audit-ready.
Features:
Server Decommissioning
Identify all the rules, applications, and dependencies tied to a server before it’s retired. SecureTrack ensures continuity by letting you replace, move, or remove the server while maintaining required connectivity and minimizing disruption.
Cleanup Browser
Drill into unused, shadowed, disabled, or duplicate rules and objects across devices. The browser makes it easy to pinpoint and export cleanup candidates, helping you optimize policies and eliminate redundancy.
Rule and Object Usage
Generate reports that show the most-used, least-used, and unused rules and objects. These insights guide rulebase optimization, making it easier to remove irrelevant rules and tune heavily used ones for better performance.
Security Policy Optimization
SecureTrack+ helps organizations reduce overly permissive access and streamline their rulebases. By analyzing real traffic patterns it provides clear recommendations that make policies tighter, safer, and more efficient.
Features:
Automatic Policy Generator
Automatically builds an optimized firewall rulebase by allowing only the traffic that is actually in use. APG can tighten permissive rules, support new firewall deployments, and uncover traffic patterns for forensic analysis.
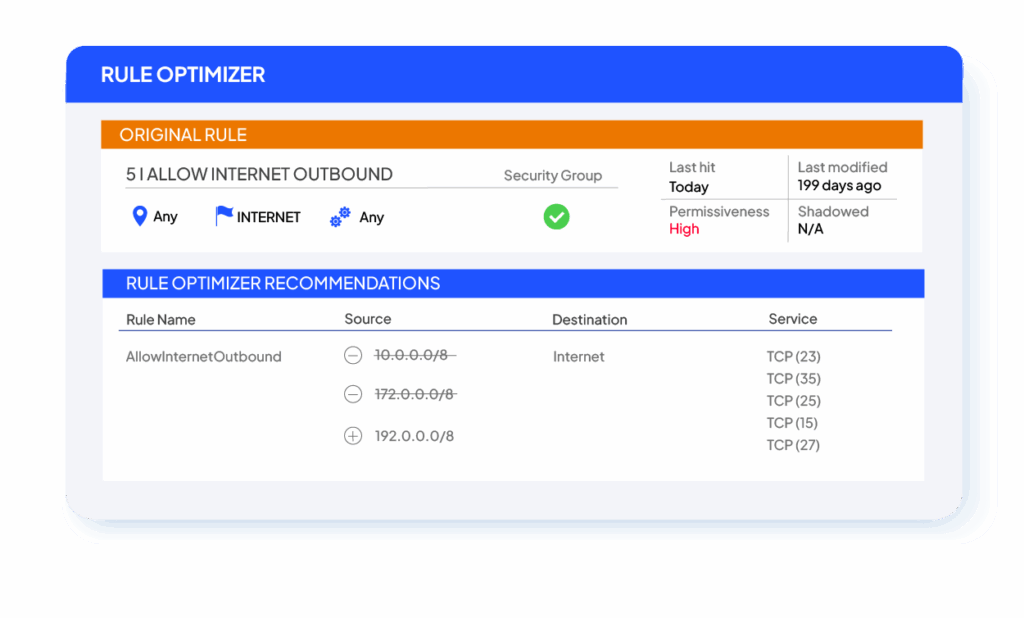
Rule Optimizer
Analyzes real traffic usage data to recommend tighter, safer replacements for existing rules. Based on each rule’s source, destination, and service fields, it identifies which addresses and ports are truly required. Recommendations can be adjusted for stricter enforcement, helping teams remove unnecessary access while maintaining business continuity.
Policy Optimization
Dashboard widgets highlight overly permissive rules, unused rules, and optimization opportunities across devices. Predefined queries and cleanup trends make it easier to prioritize changes and track improvements over time.
Change Tracking
Over time, policies accumulate outdated servers, unused rules, and duplicate objects that add risk and complexity. SecureTrack+ makes it simple to find and remove this clutter so your security posture stays clean, efficient, and audit-ready.
Features:
Revision Comparison
Compare any two revisions side by side with color-coded highlights to see exactly what changed. Each revision includes full accountability, showing who made the change and when.
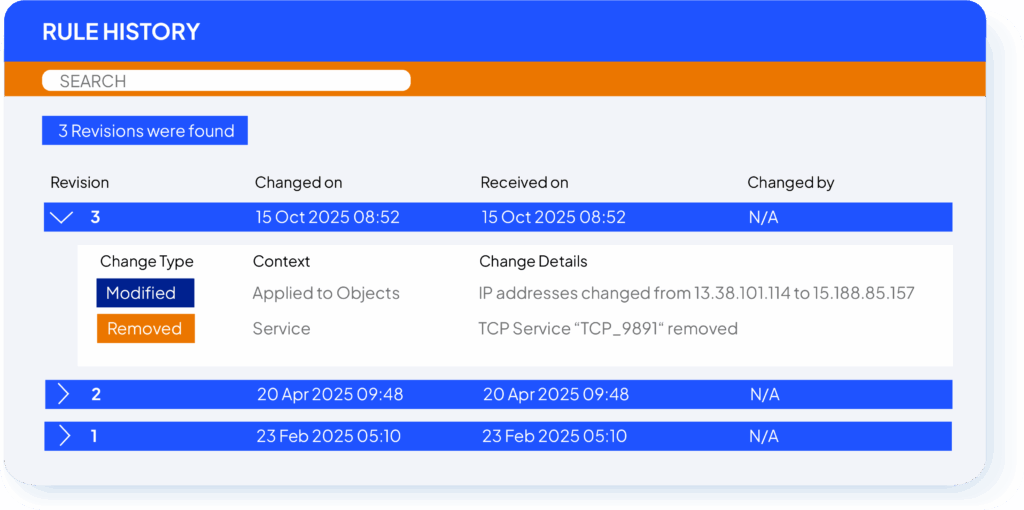
Rule History
Drill into a specific rule to see all direct and indirect changes over time. SecureTrack shows when the rule was modified, by whom, and the details of what was added, removed, or adjusted.
Revision History
View a timeline of all revisions for each device, complete with notifications when new revisions are created. This running log makes it easy to audit device activity and understand how policies have evolved.
Change Browser
Quickly browse recent revisions across single devices or groups of devices in a sortable view. Revisions are automatically flagged as authorized or unauthorized based on ticketing data, giving you instant visibility into risky or unapproved changes.
Vulnerability Exposure Prioritization
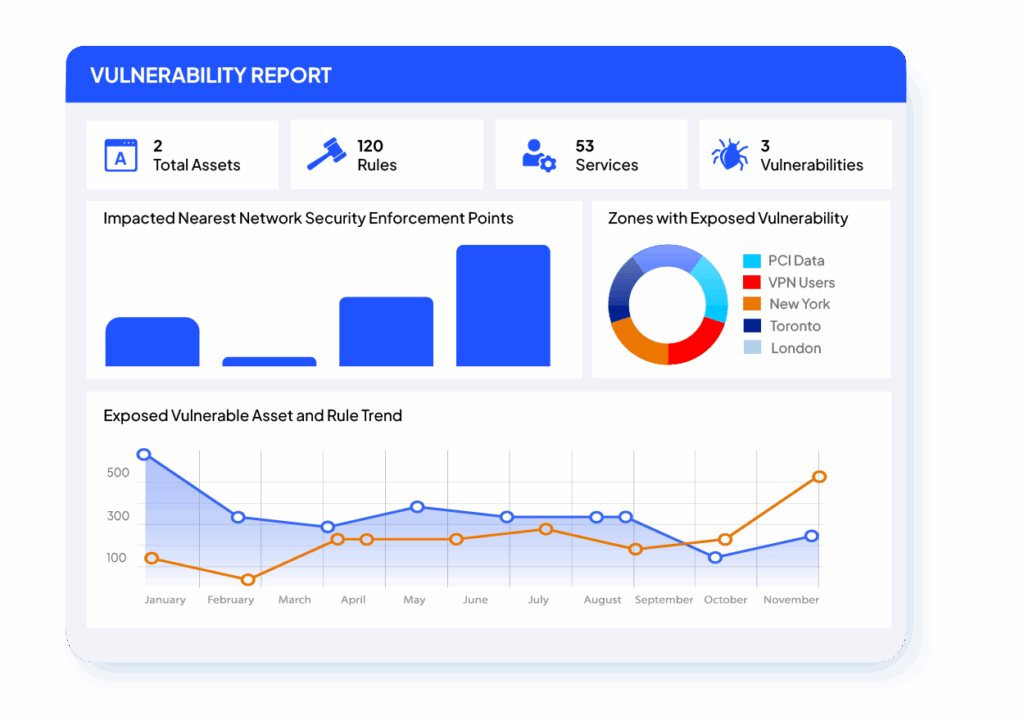
SecureTrack+ helps teams move beyond visibility by linking vulnerabilities to the policies that expose critical assets. By integrating with vulnerability scanners, it highlights the riskiest paths and provides clear priorities for remediation.
The Vulnerability Mitigation App (VMA) integrates with vulnerability scanners to identify firewall rules that expose assets to known vulnerabilities. The app ranks exposures by criticality, helping teams prioritize mitigation and track risk reduction over time.
Network Mapping & Visualization
SecureTrack+ provides foundational visibility into how network devices and policies are connected. While it does not offer full interactive mapping, it enables teams to monitor relationships and dependencies as a static reference point.
For advanced topology analysis, check out our SecureChange+ tier.
Transforming Network Security & Automation
Elevate your network security and cloud security operations with Tufin’s product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.
SecureTrack+
Firewall & Security Policy Management
Drive your security policy journey with SecureTrack+
- Centralize network security policy management, risk mitigation and compliance monitoring across firewalls, NGFWs, routers, switches, SDN and hybrid cloud
- Automate policy optimization
- Prioritize and mitigate vulnerabilities
SecureChange+
Network Security Change Automation
Enhance your visibility and automate mundane tasks with SecureChange+
- Achieve continuous compliance
- Reduce network change SLAs by up to 90% with network change design and rule lifecycle management
- Identify risky attack vectors and detect lateral movement
- Troubleshoot connectivity issues across the hybrid cloud
Enterprise
Zero-Trust Network Security at Scale
Fortify your network security operations with Enterprise
- Achieve zero-touch automation through provisioning of network access changes
- Deploy apps faster through application connectivity management
- Minimize downtime and data loss with High Availability and built-in redundancy
Why Choose Tufin? Let Us Show You.
Schedule a demo and see for yourself.




