Streamline network management and improve firewall performance by regularly identifying and removing duplicate, expired, unused, or shadowed rules and objects in your firewall rule bases, ensuring policy optimization, strengthening security controls, and maintaining a zero trust environment for endpoints with real-time adjustments to existing rules.
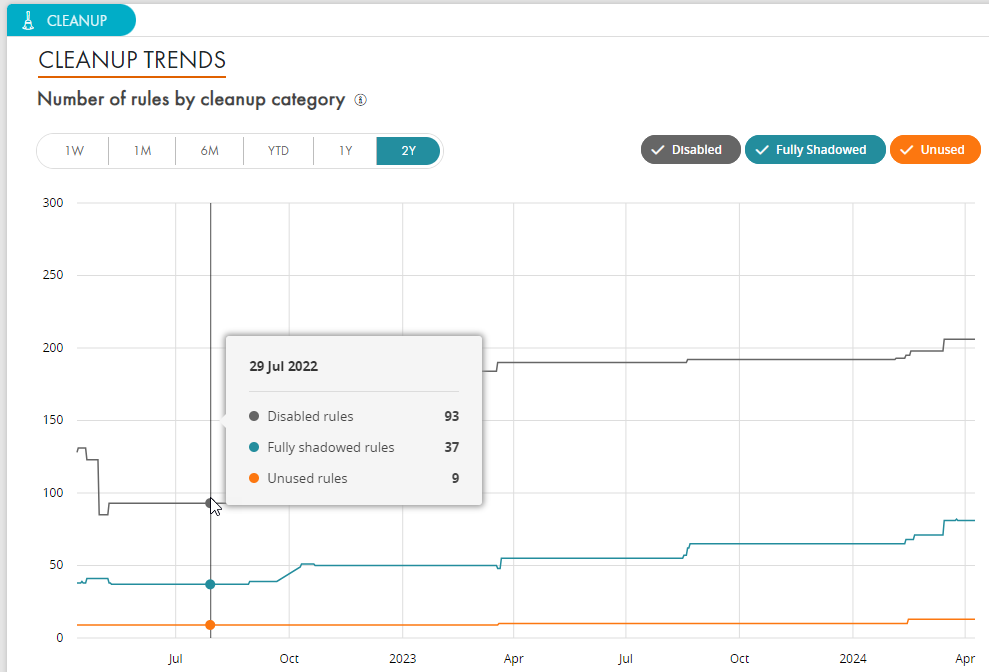
Enhance network security by optimizing and tightening rulesets through rule recertification, reducing shadowing and insecure firewall configurations, and ensuring segmentation and network access are properly managed with secure authentication for new rules within a robust policy management framework.
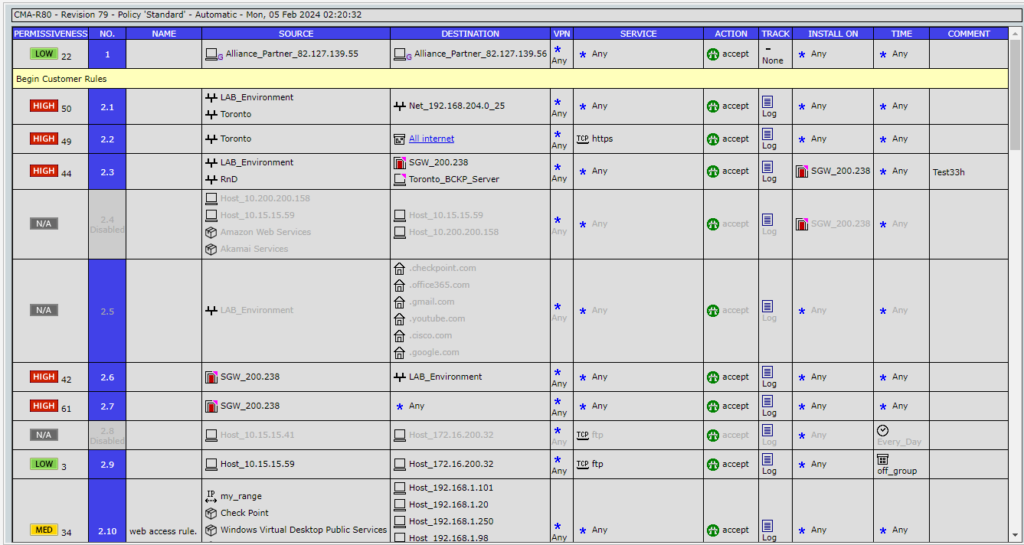
Properly document rules, objects, and policy revisions, along with enforcing consistent naming conventions, to ensure clarity, accountability, and ease of future management and audits.
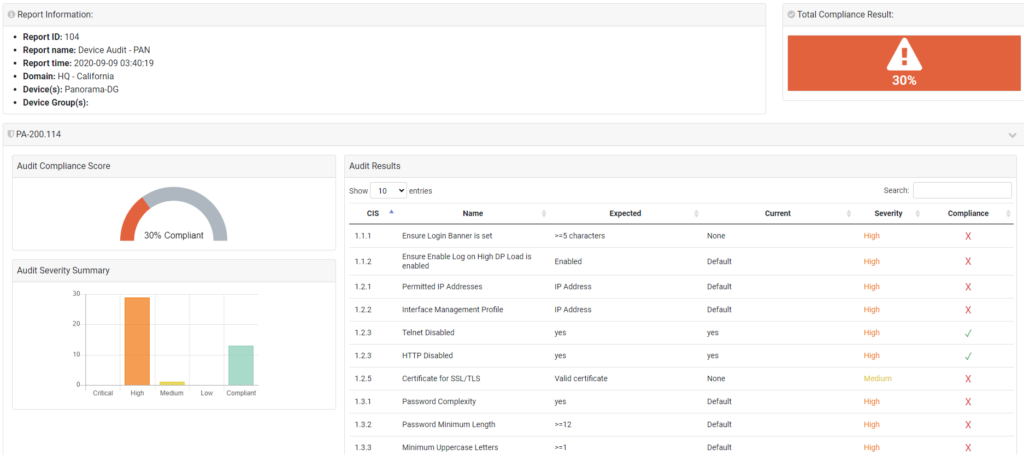
Elevate your network security and cloud security operations with Tufin's product tiers. Addressing the most challenging use cases, from segmentation insights to enterprise-wide orchestration and automation, experience a holistic approach to network security policy management.