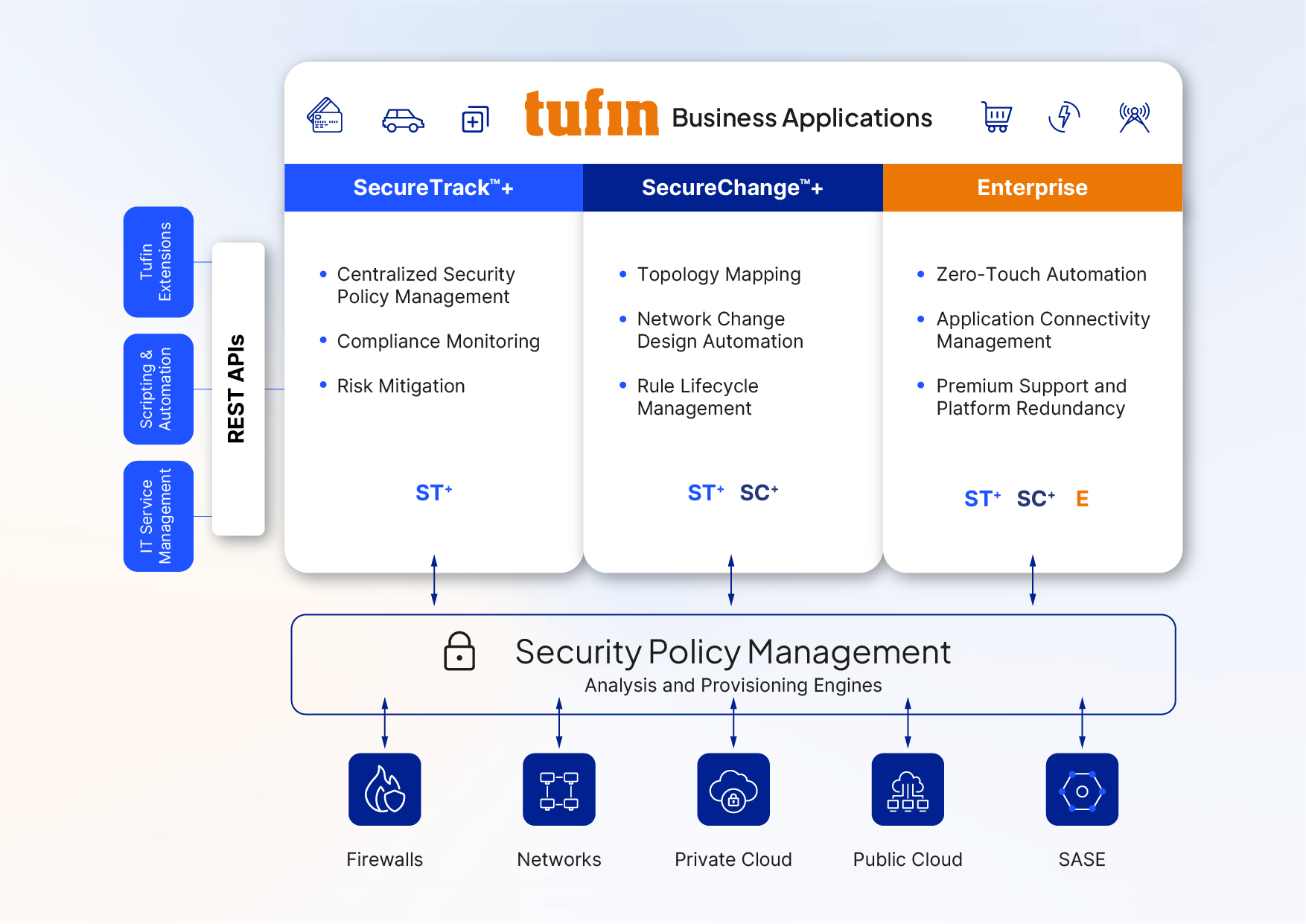
The complete solution for automatically designing, provisioning, analyzing, and auditing firewall security policy changes from the application down to the network.

Define and enforce a central security policy to control who can talk to whom and what can talk to what across the hybrid network.
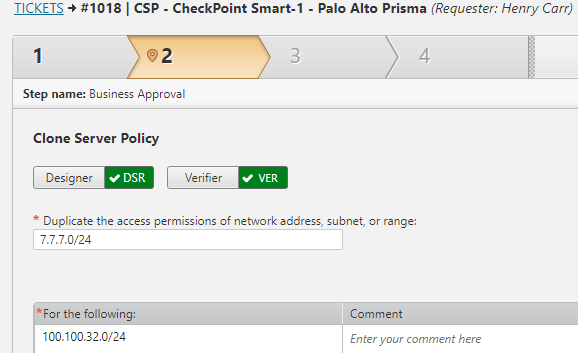
Leverage one of the most sophisticated network topology engines in the industry to automatically design and provision requested policy changes across the entire network, including private and public cloud infrastructure.
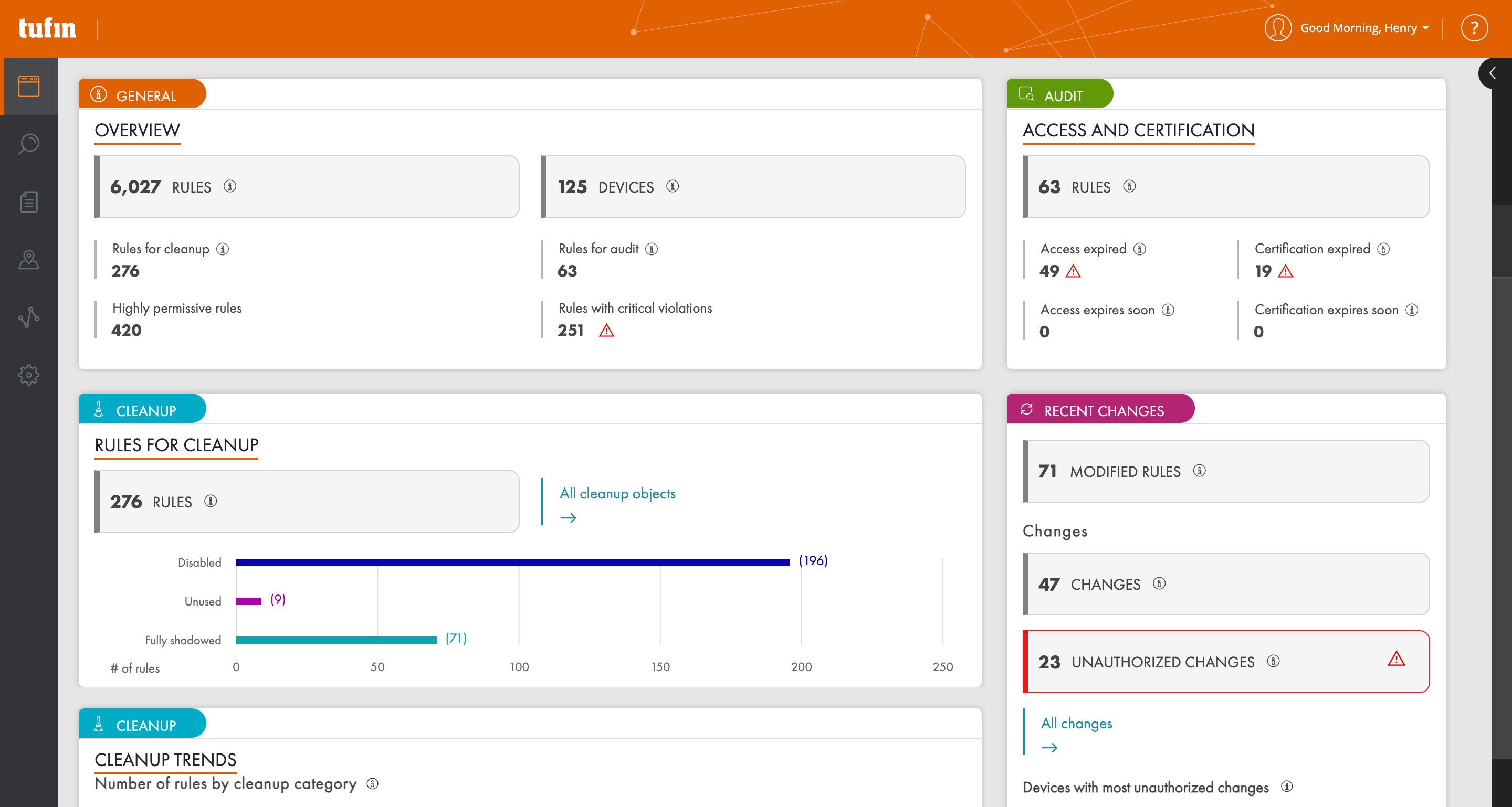
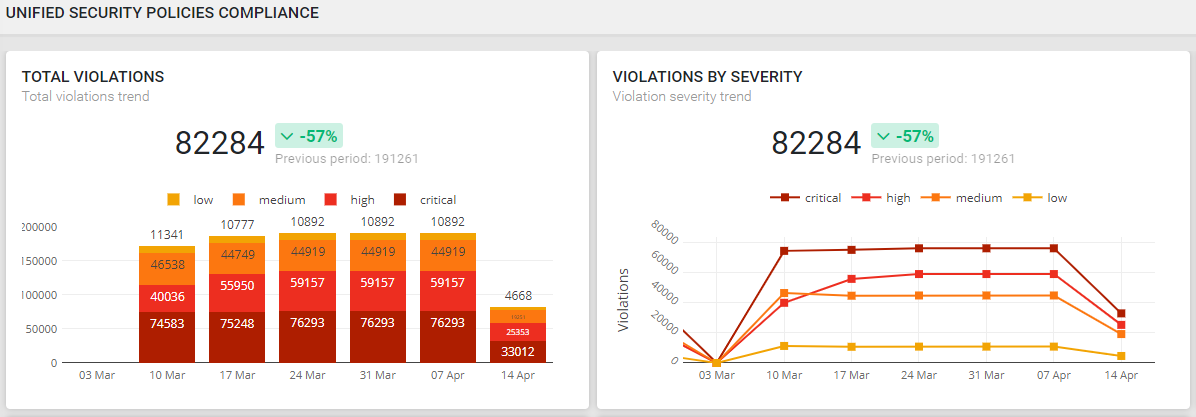
Use a data-driven approach to analyze the configuration of firewalls, routers, switches, and cloud platforms. Identify risks, misconfigurations, and unused rules that can be removed.
Integrate the Tufin Orchestration Suite with a wide range of platforms and existing security and IT operations tools to ensure a single pane of glass for controlling network security changes.
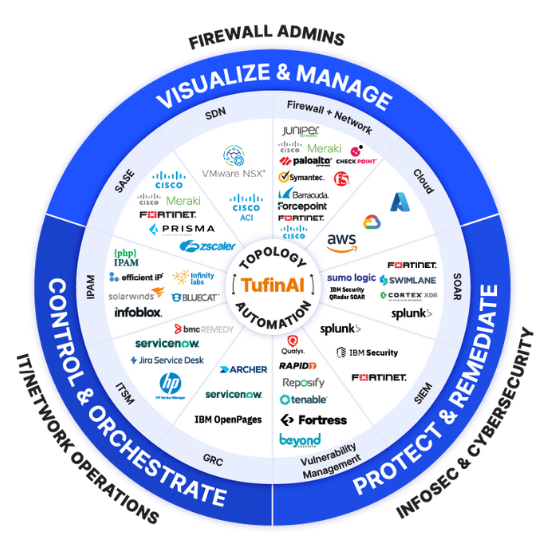

Gain end-to-end visibility, automate policy management, and mitigate risks across your global hybrid network – from next-generation enterprise firewall infrastructure to modern cloud technologies– without impacting speed or agility.

Only Tufin provides automation and a unified security policy, from on-prem to cloud, across NetSec and DevOps.