Securing high and medium impact BES cyber systems is a tremendous challenge for today’s Bulk Electric System providers. Here are some alarming data points about cyber security threats and vulnerabilities:
A single cyberattack on the North American electrical power grid has the potential to cause hundreds of billions of dollars in economic damage. Following the Great Northeast Blackout of 2003, the North American Electric Reliability Corporation (NERC) took the initiative to draft Critical Infrastructure Protection (CIP) standards to prevent such an attack from happening again. The NERC CIP standards have gone through several iterations since then and currently standard at version number six.
The challenge for BES networks transitioning to and complying with NERC CIP v6 is multifaceted, requiring:
Tufin provides the responsible entity with the essential toolbox for today’s cyber security challenges and compliance with NERC CIP standards. It helps you maintain continuous compliance for NERC CIP V6 across complex network environments by centralizing your visibility and control. By automating policy-based change management and policy optimization you are able to maintain a single audit trail and ensure policy adherence.
Tufin includes powerful network segmentation tools that help utilities reduce cyber risk and mitigate damage in the event of a cyberattack, protect BES cyber assets, and reduce risk exposure associated with transient assets. Tufin’s NERC segmentation template can be used for whitelisting and blacklisting to protect your BES network.
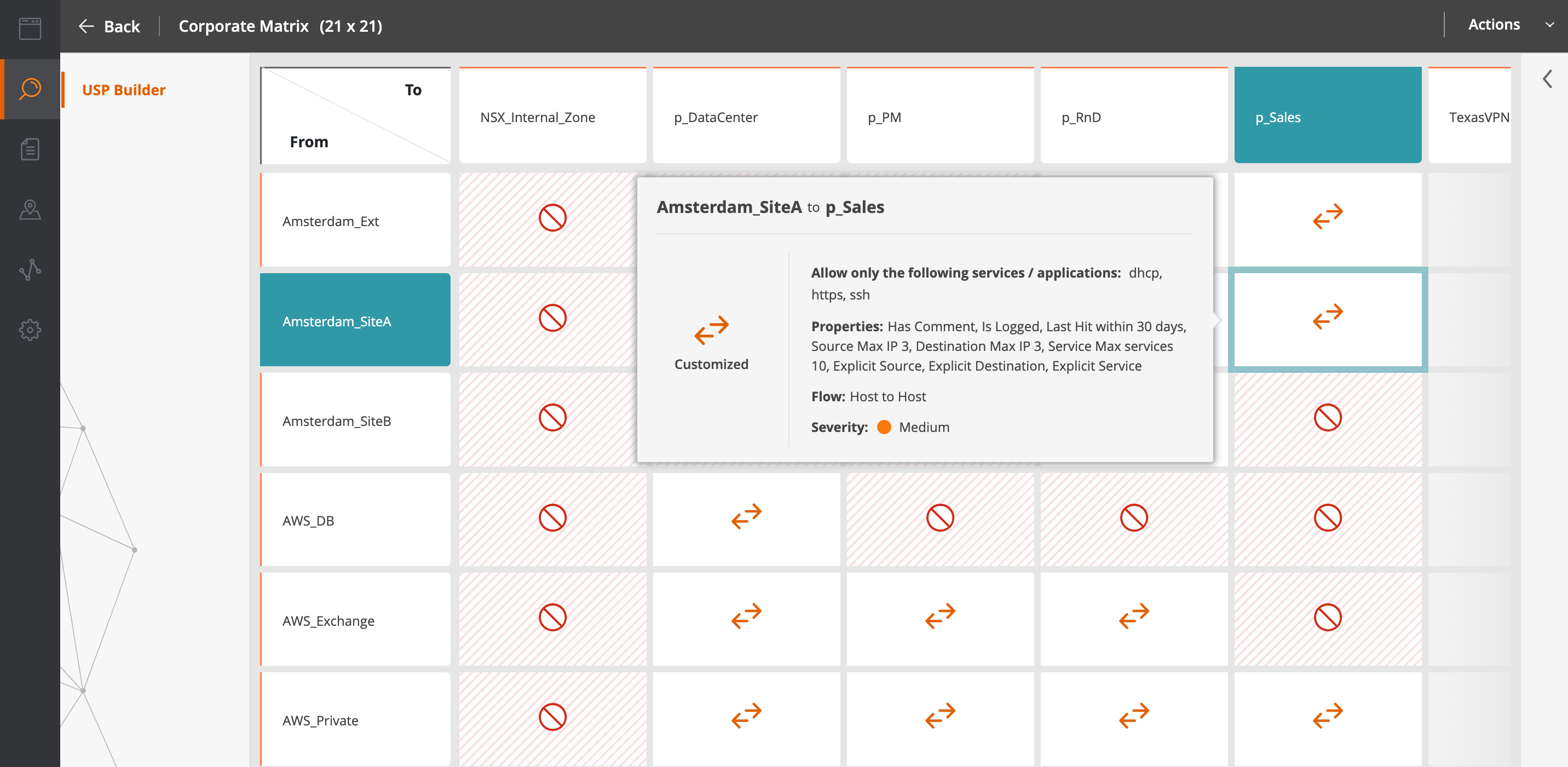
Tufin’s unified security policy management matrix allows uses your enforcement point configuration data to document a global security policy within an at-a-glance view. Within this dashboard you can refine your segmentation policies and build out new, more advanced segmentation policies. Then you can push those configuration changes out to firewalls and security groups.
Tufin centralizes firewall management across on-premises and cloud, enabling utilities to control and secure application connectivity across their network including dynamic load control systems, industrial control systems, advanced metering software, load modeling, electric grid monitoring, transmission assessment, risk analysis, and other critical applications.
Modern BES cyber systems are comprised of multi-vendor, multi-technology firewalls and other security products that are complex to manage and often provide a fragmented view of security. Tufin solutions provide deep network visibility across heterogeneous networks that includes on-premises, cloud, and hybrid network configurations, facilitating cyber risk management.
NERC CIP standards are constantly evolving to meet the shifting threat landscape posed by new forms of cyberattacks and new technologies such as IoT-connected devices. Tufin helps utilities continuously update and consistently enforce security policies to meet the latest NERC CIP standards. With Tufin, utilities can quickly develop and implement new security rules to deter, detect, and prevent malicious code and other cyber attacks including those transmitted through transient assets.
NERC CIP compliance standards now require that utilities report on any attempts to compromise their infrastructure. Tufin technology automatically generates audit trails to demonstrate NERC CIP compliance on demand, helping you meet tight deadlines and avoid high penalties.

Tufin’s compliance reporting is more accurate than other vendors can provide, because the solutions topology modeling is highly accurate and updates daily as your network evolves. This allows Tufin to see more of your network and associated controls to minimize false positives, for example.
With Tufin’s Reporting Essentials, each report is generated from a predefined report template that you can configure according to your preferred settings. These report settings can then be saved for future use. You can define which information is displayed, how frequently the report output is generated, and the date and time in which it is distributed to recipients. These automation capabilities eliminate the need to manually create reports (although this feature is also supported), and allow you to align the timing of the report output distribution to when it is required. This will allow you to automatically distribute reports before reoccurring meetings, and enable participants to come better prepared.
Report recipients can view the generated reports in their browser, and/or you can distribute the reports as PDF or CSV files.
Tufin’s reports address a number of use cases, such as the following:
Today, there are no less than a dozen cyber security standards outlined in NERC CIP V6 that are specifically aimed at protecting critical infrastructure. Tufin is facilitates meeting any standards related network access controls that prevent unauthorized access to networks, network change management, recovery and response planning and more. The NERC CIP standards include:

Gain end-to-end visibility, automate policy management, and mitigate risks across your global hybrid network – from traditional enterprise firewall infrastructure to modern cloud CI/CD pipelines – without impacting speed or agility.

Only Tufin provides automation and a unified security policy, from on-prem to cloud, across NetSec and DevOps.